Business broadband security: How to protect your internet connection
Broadband security specifically protects your internet connection from external threats, such as unauthorised access, data interception, and DDoS attacks. Our experts cover the basics: routers and firewalls, encryption through VPNs or SD-WAN and compliance. It also explains backups, monitoring, and tips to keep your systems secure.
Content highlights:
- What is broadband security?
- Why business broadband needs to be secure
- Core components of a business internet connection
- Strengthening your business broadband security setup
What is broadband security?
Broadband security refers specifically to all the defences that protect your broadband internet connection(s) from external cyber threats.
This includes attacks coming from various external sources, such as your business broadband provider, cloud services, and other independent actors.
Broadband security measures focus on:
- Preventing unauthorised access to your local network from unwanted external actors.
- Securing traffic to and from all external sources against interception or data alteration.
- Blocking malicious traffic and preventing Distributed Denial of Service (DDoS) attacks that could disrupt or slow down your internet connection.
- Encryption of data in transit ensures sensitive information remains confidential when transmitted over the internet.
Broadband security focuses exclusively on the external connection, whereas local network security protects devices like computers, servers, and IoT devices within the local area network from any threats that may have bypassed broadband defences.
Why business broadband needs to be secure
All aspects of cybersecurity are crucial in defending against cyberattacks, but broadband security is particularly important as it protects the boundary between your private local network and the outside internet.
For business owners, there are several reasons why ensuring robust broadband security is vital:
- Protects against external threats: Secures your internet connection from unauthorised access by external actors, preventing cybercriminals from infiltrating your network.
- Safeguards sensitive data: Ensures that sensitive business data, like customer information and financial records remain private and protected from interception during transmission.
- Ensures business continuity: Protects your internet connection from DDoS attacks and other disruptions that could cause costly downtime, keeping operations running smoothly.
- Ensures regulatory compliance: Helps your business meet data protection regulations (like GDPR), avoiding penalties for non-compliance.
- Protects customer trust: By securing online transactions and protecting customer data, you maintain customer trust and safeguard your business reputation.
- Defends against evolving cyber threats: Keeps your broadband connection secure from increasingly sophisticated cyberattacks, staying one step ahead of potential threats.
Core components of a secure a business internet connection
A secure broadband connection is one in which all of its core components are working as intended to defend all traffic against external threats.
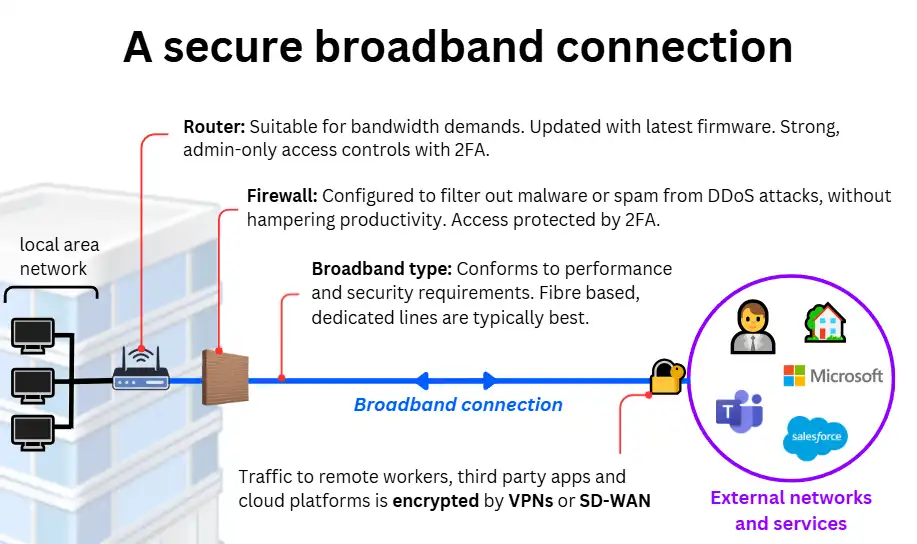
The core elements are:
Firewalls
Firewalls act as a permeable barrier between your business network and the internet, filtering traffic to prevent unauthorised access. They examine incoming and outgoing data, blocking any malicious traffic or threats based on predefined security rules. Firewalls must be regularly configured to match your business’s evolving traffic needs and to adapt to emerging security threats.
Encryption
Encryption ensures that all data transmitted over the broadband connection is encoded, making it unreadable to anyone intercepting it. This is especially important for protecting sensitive information, like financial transactions or customer data, during transit over the internet.
VPN (Virtual Private Network)
A VPN creates a secure, encrypted tunnel for data to travel through when connecting to external users, networks or services. It ensures that any communication between your site and remote locations (such as cloud services or remote employees) is protected from eavesdropping or tampering. Strong user authentication is required for access control to the tunnel.
SD-WAN, SASE and cloud-native WANs
Multi-site and remote-first businesses are switching to more holistic, wide area network architectures, which optimise and secure the entire business network instead of focusing on individual broadband connections.
In these cases, VPNs are often replaced (or used alongside) new technologies like SD-WAN solutions, cloud-based WANs, or building a SASE security network, which takes charge of broadband security by managing routing, implementing updates, and configuring routers consistently across all links.
DDoS protection
Distributed Denial of Service (DDoS) attacks are designed to overwhelm your internet connection by flooding it with traffic. Implementing DDoS protection helps detect and mitigate these attacks, preventing service disruptions or outages that can affect your business operations. DDoS protection must be calibrated to handle the expected traffic volume of your business and adapted to mitigate evolving attack methods.
Intrusion Detection and Prevention Systems (IDPS)
These systems monitor network traffic for suspicious activity and potential threats. If an intrusion attempt is detected, they can alert administrators or even block the attack in real-time, helping to prevent breaches and other malicious activity.
Strong authentication and access control
Ensuring that only authorised users have access to your network is vital for broadband security. Multi-factor authentication (MFA) and strict access control policies limit who can connect to your network, preventing unauthorised access and minimising the risk of internal threats.
Regular software and firmware updates
Keeping your broadband devices (i.e. business broadband routers and modems) and security software up to date is crucial. Security patches often address known vulnerabilities that attackers could exploit. Regularly updating software and firmware helps to close these gaps and maintain a secure connection.
Secure DNS (Domain Name System)
Secure DNS services help ensure that your internet traffic is directed to legitimate and trustworthy websites. They can block access to malicious or compromised domains, reducing the risk of phishing attacks, malware, or other types of cyber threats.
If hosting your services under a dynamic IP environment, dynamic DNS services must be well configured and secured.
Router and device configuration
Ensuring that routers and other network devices are properly configured is essential. This includes changing default passwords, using strong encryption methods (e.g., WPA3 for WiFi), and disabling unnecessary services that may open up security vulnerabilities. WiFi is normally seen as part of local security, but since the signal typically penetrates outside the premises, it can be a way to access the network.
Compliance frameworks
Compliance frameworks ensure that the security measures applied to your broadband connection align with legal and industry regulations. Frameworks such as GDPR, PCI-DSS, and HIPAA set out specific requirements for securing data during transmission and protecting access to sensitive information.
They provide the guidelines that ensure encryption, secure data transmission, and access control are not only practical but also compliant with the relevant laws and standards.
Security of different business broadband types
Business broadband connections vary widely in their security characteristics. Key factors that influence security include:
- Medium of transmission: Fibre, copper, coaxial cable, and wireless (e.g., microwave or 5G) each have different levels of speed, stability, and vulnerability to interference or interception.
- Broadband contention: Some connections are fully dedicated to a business, while others are shared with many users, potentially introducing more risk through congestion or shared infrastructure.
- Provider service: They may implement bandwidth throttling, traffic prioritisation, or other performance-related controls, which can indirectly impact security and reliability.
- Speed symmetry: Connections may come with equal or unequal download/upload speeds, affecting the ability for network monitoring.
Here is how these factors affect the security of individual connections:
ADSL broadband
ADSL broadband is largely a legacy technology that remains in use in fringe setups such as rural properties without any fibre whatsoever.
Remaining ADSL connections should be aware that it is one of the most vulnerable technologies due to its limited bandwidth, reduced firmware support, outdated hardware, and the more manageable disruption and interception of its electrical signals.
While ADSL connections will be phased out as part of the “Big Switch Off” planned for January 2027, it is generally recommended to switch to an alternative such as Starlink or 4G broadband.
Here are some details on these risks, as well as things your business can do to mitigate them:
| Weakness | Description | Security Considerations |
|---|---|---|
| Line Tapping | Physical tapping of ADSL copper wires to intercept data transmissions | - Ensuring strong encryption (e.g. https) - Inspecting cabling for any tapping devices. - Implementing Intrusion Detection Systems (IDS). |
| Limited Bandwidth for Monitoring | ADSL is slow and often can't handle the additional bandwidth needs of real-time monitoring tools. | - Use basic monitoring tools - Upgrading to fibre optics. |
| DSL Signal Interference | Electrical signals travelling through copper wires can be easily disrupted using magnetic fields. | - Use cable shielding to reduce interference. - Monitoring signal quality - Using ADSL splitters and filters for redundancy. |
| Outdated Authentication | As an outdated technology, many ADSL routers come with outdated security features (e.g. weak default passwords, No 2FA, no updates support). | - Purchasing a modern ADSL router - Upgrading to fibre-optics - Changing default passwords and enabling 2FA. - Updating router firmware (if available) - Disabling unused routers and services without firmware updates. |
| DDoS | While all technologies are vulnerable, ADSL-hosted services have low bandwidth, making them easier to overhwhelm. | - Upgrade to a higher bandwidth connection using our business broadband comparison service. |
SoGEA
SoGEA broadband is a part-copper wire, part-fibre optic connection that replaced Fibre-to-the-Cabinet (FTTC) broadband.
It leverages the ubiquity of telephony cables for access with the speed of fibre. It remains relevant in underserved areas like rural areas where full fibre (FTTP) still remains unavailable.
This type of fibre optic business broadband inherits many of the vulnerabilities of ADSL because the section between the premises and the street cabinet is still covered by copper wires and has new ones related to the telephony-fibre intersection:
| Weakness | Description | Security Considerations |
|---|---|---|
| Line Tapping | Physical tapping of copper wires to intercept data transmissions | - Ensuring strong encryption (e.g. https) - Inspecting cabling for any tapping devices. - Implementing Intrusion Detection Systems (IDS). |
| DSL Signal Interference | Electrical signals travelling through copper wires can be easily disrupted using magnetic fields. | - Use cable shielding to reduce interference. - Monitoring signal quality - Using ADSL splitters and filters for redundancy. |
| Man-in-the-Middle (MitM) Attack | FTTC connections can be vulnerable to MitM attacks, where an attacker intercepts and potentially alters the communication between two parties. | - Use strong encryption (e.g., TLS). - Use VPNs to secure connections over public networks. |
| Physical Cabinet Security | Street cabinets used in FTTC can be physically accessed and tampered with, allowing attackers to disrupt services or intercept data. | - Independently inspect cabinets or ask broadband provider to check. |
Full fibre business broadband
Full fibre business broadband (Fibre-to-the-Premises) offers an entirely fibre-based journey from the cabinet to the premises. This makes the connection more reliable than any copper or wireless-based connection and ensures threat monitoring remains continuous.
Also, since fibre has become the global connectivity standard, it benefits from priority rollout of the latest hardware and software updates.
However, fibre optic cables are not infallible against tampering or signal jamming, and their reliability can ultimately backfire if it is used against your business:
| Weakness | Description | Security Considerations |
|---|---|---|
| High Bandwidth Exploitation | High bandwidth can be exploited for data theft or DDoS attacks | Implement DDoS protection, monitor network traffic, use rate limiting |
| Line Tapping and Signal Jamming | Physical tapping/jamming of fibre-optics is harder than copper cables. It requires specialised equipment to 'split' the light signals or 'bend' the cables to intercept/jam the signal. | - Tamper-evident enclosures. - Regular cable inspection. - Use fibre intrusion detection - Secure installation and maintenance practices. |
| Exploitation of large data volumes | High-speed FTTP connections can carry large volumes of sensitive data, increasing the speed a volume of a successful attack. | - Encrypt data at rest and in transit. - Implement strict access controls and authentication. - Regularly audit and monitor data access and transmission logs. |
Cable broadband
Virgin Media’s cable broadband uses coaxial cables to deliver superfast broadband. Despite its high performance, it suffers from other attack vectors due to its shared medium architecture:
| Weakness | Description | Security Considerations |
|---|---|---|
| Coaxial Cable Signal Interception | Coaxial cables can be tapped more easily than fibre optics due to the nature of the electromagnetic signals used. | - Strong encryption - Regular inspection and maintenance of physical cabling. - Intrusion detection systems for monitoring. |
| Signal Leakage | Coaxial cables can experience signal leakage, which makes eavesdropping much easier. | - Ensure proper shielding of coaxial cables and use high-quality connectors and cabling. - Conduct periodic testing for signal leakage. |
| Router and Modem Vulnerabilities | Cable broadband relies on business broadband routers and modems which will have lessened support over time, as fibre is a more scalable technology which received more development focus. | - Ensure regular firmware and software updates - Use devices from reputable manufacturers. - Disable unused services and ports to reduce the attack surface. |
| Bandwidth Allocation and QoS Exploits | Cable's shared medium architecture makes it more vulnerable to the manipulation of Quality of Service (QoS) settings, allowing attackers to prioritise their own traffic and potentially dely service to legitimate users. | - Secure QoS settings. - Monitor network traffic for signs of QoS manipulation. - Implement rate limiting to prevent bandwidth hogging by any single user. |
While fast, it is due to be phased out once full fibre is available across the UK.
Mobile broadband
Mobile business broadband that uses 5G and other cellular networks is vital for redundancy and failover in sites outside the fibre network, and for safe remote working.
It ensures employees have their network when travelling, avoiding public guest WiFi and other security pitfalls. However, wireless cellular networks are not infallible, and the portability of mobile devices also increases their vulnerability.
Here are the security risks specific to 5G business broadband and how to avoid them:
| Weakness | Description | Security Considerations |
|---|---|---|
| Cellular Network Tapping and Jamming | Mobile broadband relies on cellular networks, which can be vulnerable to attacks like SIM jacking, fake base stations (IMSI catchers), and man-in-the-middle (MitM) attacks. These exploits can intercept, alter, or block communications. | - Using strong mobile data encryption (e.g. LTE-A; 5G standards). - Multi-factor authentication (MFA) to protect physical SIM cards. - Implementation of E-SIMs. |
| Device Vulnerabilities | Mobile devices can be targets for malware, phishing, and other cyber attacks, compromising the security of mobile broadband connections. Their sheer number and variety make the attack surfaces larger. | - Ensure devices are updated and patched. - Implement device management solutions. - Implement Zero-Trust security. |
| Public Wi-Fi Risks | Users of portable mobile broadband can accidentally connect to public Wi-Fi networks by accident, which can be insecure and susceptible to various attacks. | - Set devices to only connect to mobile broadband WiFi network and disable unknown networks. - Encourage VPNs for public Wi-Fi networks if no other choice. |
| Physical Device Security | Portable routers and mobile devices are prone to loss or theft, which can lead to unauthorised access to sensitive information and mobile broadband services. | - Use strong, unique passwords and/or biometric authentication. - Enable remote wipe capabilities - Regularly back up data to cloud services to prevent data loss. |
Satellite broadband
Low Earth Orbit (LEO) satellite business broadband is a novel type of connection enabled by trailblazers like Starlink and OneWeb. Issues with satellite cybersecurity are more common in Hollywood blockbusters than in something the average business needs to be concerned about.
Nevertheless, the core elements remain essential, including keeping all hardware updated and secure from internal threats, and using zero-trust network access if possible.
Leased line broadband
Leased line broadband is the most performant and (arguably) most secure type of connection. Your leased line provider delivers dedicated fibre-optic cables and bandwidth in that segment and within the public fibre domain. There is, therefore, no risk from medium sharing, wireless signal interception, etc.
| Weakness | Description | Security Considerations |
|---|---|---|
| Data transmission tampering, interception or interruption | Leased lines involve dedicated physical fibre connections that can be tampered with or tapped in the same way as FTTP. | - Secure enclosures and regular inspections. - Tamper-evident seals and secure installation practices. - Physical monitoring and alarms to detect tampering. - Use strong encryption. |
| Lack of Redundancy | These dedicated connections may result in a false sense of performance security and negate business broadband redundancy as a safety mechanism. | - Implement a business broadband failover solution (a backup connection). |
💡The high security of leased line connections comes at a cost, with leased line broadband prices much higher compared with other types of broadband.
Strengthening your business broadband security setup
To ensure your broadband connection is secure, it’s crucial to follow a structured approach that starts with understanding best practices and your current broadband before applying the core components in compliance with industry standards:
1. Review government resources
Begin by reviewing the Cyber Essentials certification and the NCSC Cyber Security Guidance for businesses. These resources provide clear, actionable steps for improving broadband security, including tips for compliance, and are useful for both small and large companies alike.
2. Consider managed broadband security
For businesses that wish to partially or fully outsource their broadband security, consider consulting a Managed Service Provider (MSP) for expert assistance. They will audit your entire setup and assist you in strengthening it to ensure it is secure and compliant.
3. Implementing core broadband security
At this point, you have all the tools your business needs to strengthen broadband security. Here are some tips for each core component:
Broadband technology
Review the type of broadband connection you’re using and evaluate potential vulnerabilities specific to your connection type and your usage.
This includes both secondary or failover connections your business uses for continuity and extra security.
The general rule is that fibre-based connections and modern wireless are safe as long as the router is always up to date and the connection’s performance is high enough for your business usage.
If you’re using outdated broadband like ADSL, upgrading to more secure fibre, mobile or satellite options may be necessary. Upgrade today with our business broadband comparison service.
Firewall configuration
Configure firewalls to block unauthorised traffic while allowing legitimate communication. Ensure that your firewall rules are fine-tuned to your business needs. Overly permissive rules can leave vulnerabilities open, while overly restrictive rules can hinder business operations. Regularly update and review firewall configurations.
VPN or SD-WAN review
Ensure your business is getting secure remote access and safe communication with external services via a VPN (more common for single site businesses) or SD-WAN based technologies. Ensure its using strong encryption protocols like IPsec or OpenVPN. Multi-factor authentication (MFA) should be enabled to prevent unauthorised access through compromised credentials.
DDoS protection
Measures to safeguard against DDoS attacks. Cloud-based DDoS protection services are highly effective at mitigating large-scale attacks. Always ensure your broadband provider is deploying rate-limiting and traffic filtering to help absorb and block malicious traffic before it reaches your network. If they don’t, ensure your own firewall does.
Regular updates
Ensure all devices are set to auto-update their firmware and get the latest security patches, whenever possible, to reduce the risk of being exploited through known vulnerabilities. Ensure you are auditing these regularly to make sure there are no misconfigurations.
Compliance reviews
Ensure your overall broadband security is compliant with GDPR, PCI-DSS, HIPAA and any other specialised industry standards (where applicable). It’s often essential to qualify for insurance and avoid fines if you do get breached. Regular audits are necessary to ensure you maintain compliance over time.
Staff training
Ensure all your staff and any third parties that are integrated with your system receive regular training on broadband security. Persevere in making cybersecurity awareness a core value at your business, with employees always adopting a precautionary stance.
Holistic cybersecurity
Remember that broadband security is only a piece of the puzzle. Any system, even if offline, is vulnerable to attacks that can have severe consequences for your business. For example, ensure you look at:
- VoIP security: Ensure your business VoIP phone system is secure against its specific vulnerabilities, such as account hijacking, AI impersonation, and inadequate access controls.
- SD-WAN security: If you are using SD-WAN, ensure that all its components are secure, especially ensuring compatibility with routers under its control, and strong access controls to the centralised platform, which is often a single point of failure.
- Network security: Both wide and local area networks must remain secure. VLANs for local network segmentation must be appropriately configured, and any business Ethernet and MPLS links must also be secured.
4. Ensure continuous monitoring and testing
Continuously monitor network traffic for abnormal behavior and conduct security audits to identify potential vulnerabilities. Implement role-based access control (RBAC) to limit sensitive data access.
Real-time network monitoring tools and cybersecurity software are essential to detect threats early. The latter combines intrusion detection systems (IDS) and network behaviour analysis tools to identify and respond to threats quickly.
Broadband cybersecurity compliance with the Data Protection Act 2018
The Data Protection Act 2018 (DPA 2018) is the UK’s implementation of the General Data Protection Regulation (GDPR), which sets high standards for personal data protection.
While it primarily focuses on businesses and organisations handling personal data, it also applies to business broadband providers and other third parties involved in data transmission if there is a data breach in their infrastructure.
DPA 2018 requirements for broadband cybersecurity
Articles 32, 33 and 34 of the GDPR are relevant here:
- Article 32: Requires appropriate technical and organisational measures to protect any personal data handled. This includes measures like encryption, robust authentication methods, integrity and availability.
- Articles 33 & 34: Requires prompt notification of personal data breaches to supervisory authorities and affected individuals.
This means businesses are responsible for ensuring their networks are safe, and any data sent outside this network is appropriately encrypted. Network monitoring and alert systems are required to ensure any breach is caught early and reported.
Compliance responsibilities of businesses vs broadband providers
While most cybersecurity threats target internal networks, a broadband-related breach usually involves the intersection between organisations, broadband providers and infrastructure providers such as Openreach and KCOM.
Take a successful router attack, for example. A business could be responsible if it didn’t update the router firmware promptly, or the broadband provider could be responsible for a zero-day exploit on a low-quality router. In any case, whoever notices first must report the breach promptly.
Ultimately, the Service Level Agreement (SLA) defines the cybersecurity responsibilities of each party. In general, the duties are as follows:
| Infrastructure Providers (Openreach, KCOM) | Broadband Providers (BT, Virgin) | Businesses (End-Users) |
|---|---|---|
| Maintain and secure physical infrastructure such as cabinets and cables, and ensure service availability and operational integrity. | Deliver and maintain broadband services, including measures like firewalls, and in-transit encryption. | Secure internal network with firewalls, anti-malware, threat monitoring and detection, strong authentification, VPNs, etc. |
Business broadband security – FAQs
Our business broadband experts answer commonly asked questions on business broadband cybersecurity in the UK.
Are there any real-life examples of business broadband vulnerabilities?
There certainly have. For example, a 2021 BBC report exposed how six million Sky business broadband routers had a critical bug that would have let attackers take over entire networks.
Researchers found the vulnerability existed for 18 months before Sky engineers addressed it, highlighting the essential need for threat detection systems. Cybersecurity risk can only be minimised, not eliminated.
What are the security weaknesses of broadband connections?
All broadband technologies have standard security features because they have the following common weaknesses:
| Weakness | Description |
|---|---|
| Tampering | All signals, even in wired connections, can be intercepted. If unencrypted, it can lead to potential information leakage. |
| Jamming | All signals, both wired and wireless, can be jammed to disrupt the connection to a business. |
| Routers | All connections have routers acting as the first line of defense, but also as an exposed attack surface. |
| Low Bandwidth Broadband | Slower connections are more vulnerable to DDoS attacks that can quickly overwhelm the bandwidth. They also cannot support advanced real-time monitoring and threat detection, which require substantial bandwidth. |
| High Bandwidth Broadband | The fastest connections can support the most advanced cybersecurity methods and technologies, but if an attack occurs, sensitive information can be leaked more quickly. |

