Multiprotocol Label Switching (MPLS)
Multiprotocol Label Switching (MPLS) is a fundamental technology behind high-performance private networks, like those of global enterprises, payment systems, and even the NHS.
MPLS helps data travel more efficiently across fixed routes, making it an ideal addition to connections between key business assets such as offices, warehouses, labs, data centres, and cloud services.
This guide provides business decision-makers with a clear understanding of MPLS, including how it works, its benefits and limitations, SD-WAN integrations, and key considerations for deployment.
Contents:
- What is Multiprotocol Label Switching (MPLS)?
- How does MPLS work?
- MPLS integration with SD-WAN
- Benefits and drawbacks of MPLS
- MPLS security
- MPLS business implementations
What is Multiprotocol Label Switching (MPLS)?
Multiprotocol Label Switching (MPLS) is a powerful technology that helps internet traffic move more efficiently across fixed network routes. It creates faster, more reliable connections between key business sites such as offices, data centres, and cloud services.
Enterprises and institutions rely on MPLS for their high performance, low latency backbone networks. MPLS makes networks so reliable that service providers who deploy them can offer strict Service Level Agreements (SLAs) that guarantee latencies as low as 10ms and uptimes above 99.99%.
MPLS can be deployed on top of any business network and at any scale, as it operates as an overlay of specialised rules that are fully compatible with all types of broadband connections. Partnerships with international MPLS providers enable UK providers to establish global MPLS networks.
The downsides of MPLS are its high cost, lack of basic security features, and lack of support for remote workers, temporary connections and IoT applications outside the MPLS network. Addressing these limitations requires a more holistic and dynamic approach to network management.
To bridge this gap, MPLS is increasingly being implemented alongside SD-WAN solutions, which optimise and secure traffic across any connection (including MPLS!) at a much lower cost.
How does MPLS work?
MPLS can be implemented in various ways and for multiple purposes, but the way it works under the hood is always the same. Its key components work together to optimise the flow of data packets travelling with MPLS labels. Let’s take a look:
Key components of MPLS
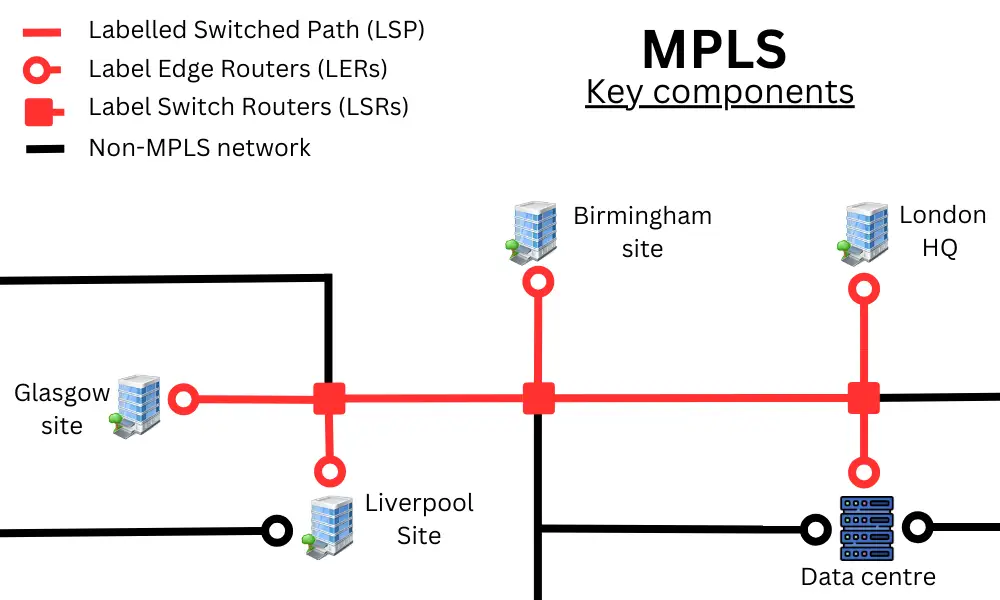
There are three key infrastructure components in any MPLS network:
Label Switched Path (LSP)
A Label Switched Path (LSP) is any predefined route within the MPLS network that data packets follow. These pathways are established between MPLS-enabled routers and switches based on MPLS labels.
Label Edge Routers (LERs)
These are the business broadband routers at the edge of the MPLS network that act as entrance (ingress) and exit (egress) points. In simpler terms, LERs function as the ‘on-ramps’ and ‘off-ramps’ of the MPLS highway, connecting the local area networks of the various sites, servers and data centers to the low-latency MPLS network.
Label Switch Routers (LSRs)
These are the network switches that act as junction points within their MPLS network. MPLS labels are swapped and updated at each relay point, ensuring the packet follows the correct predefined pathway.
LSRs are usually managed by broadband providers (for regional or national MPLS networks), with partner providers managing any international MPLS pathways. Large enterprises or institutions with private dark fibre infrastructure manage their own LSRs.
Journey of a data packet across MPLS network
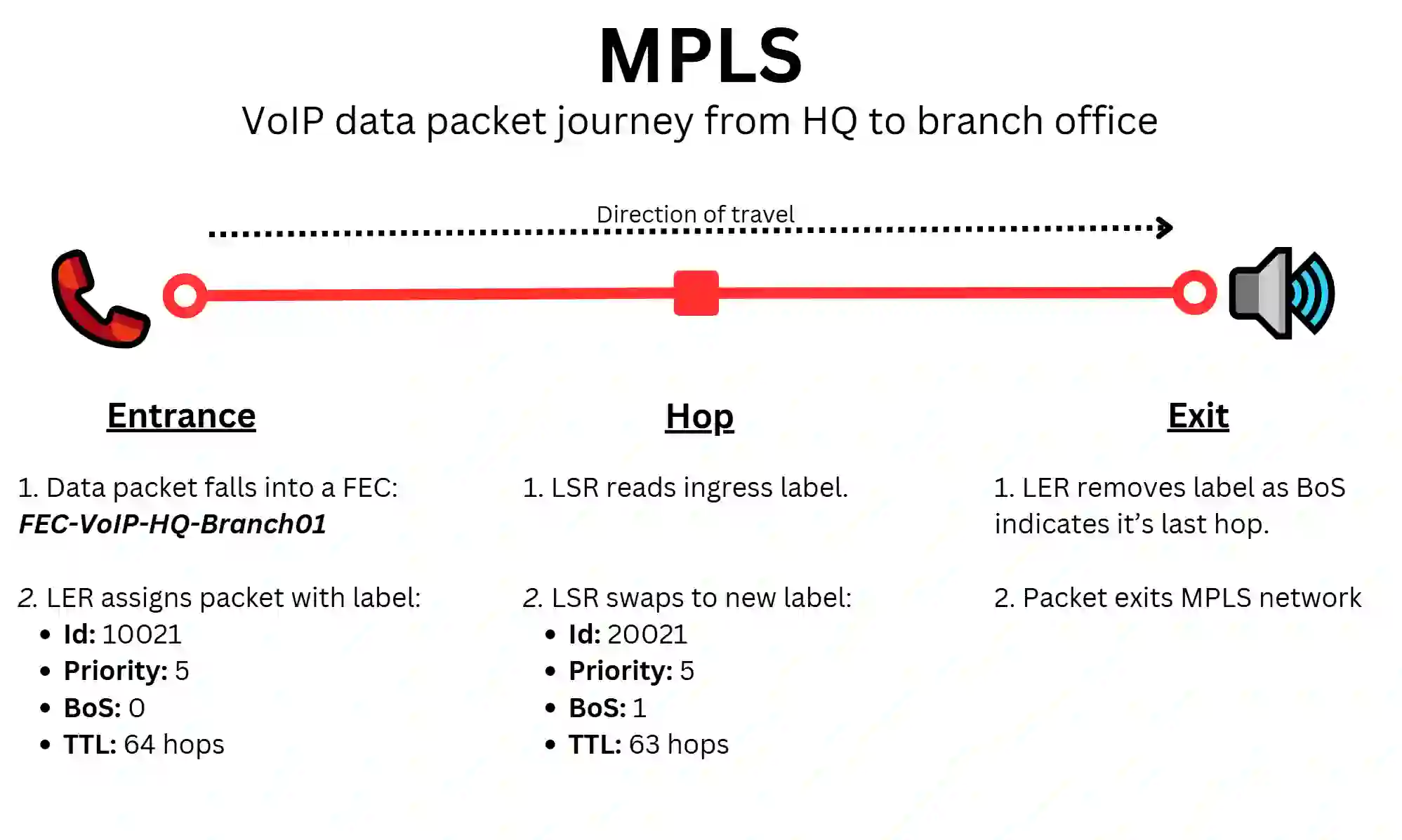
1. Ingress: Entering the MPLS network
When a data packet leaves a site (for example, from your headquarters heading to a branch office), it first reaches an MPLS-enabled edge router (LER).
The edge router examines the packet’s destination (IP header) and characteristics (data type and application). It classifies it into Forwarding Equivalence Classes (FECs), which are groups of data packets with similar characteristics. For example, a data packet carrying VoIP call data from the HQ to the branch office can be classified as: “FEC-VoIP-HQ-Branch01“.
Each type of FEC is then assigned a different ingress label indicating its priority level (e.g., Class 1 for high-priority traffic) and next hop (e.g., network switch #1). This ingress label (also known as “MPLS short label”) is inserted above the IP header to prompt the node to prioritise the MPLS indications, and contains the following data:
| Field | Bit Size | Description |
|---|---|---|
| Label Value | 20 bits | Identifies the packet’s path. |
| Traffic Class | 3 bits | Used for Quality of Service (QoS) to prioritise certain types of traffic. |
| Bottom of Stack (BoS) Bit | 1 bit | Indicates whether this is the last label in the stack. |
| Time to Live (TTL) | 8 bits | Prevents packets from circulating indefinitely by limiting the number of hops. |
2. Forwarding and swapping: Navigating the MPLS network
As the packet moves across the MPLS network, each Label Switches Router (LSR) reads the MPLS short label containing the relevant routing information instead of performing a full IP-based routing inspection, greatly reducing processing delays.
The LSR also swaps the label for a new one corresponding to the next Label Switched Path (LSP), keeping the packet on track, and optimally labelled.
3. Egress: Exiting the MPLS Network
When the packet reaches the egress edge router (LER) at its destination (i.e. the branch office’s router in this example), the MPLS label is removed (‘popped’). The data packet is then forwarded to its final destination (e.g., a VoIP phone in the branch office) using standard IP routing within the local network.
MPLS integration with SD-WAN
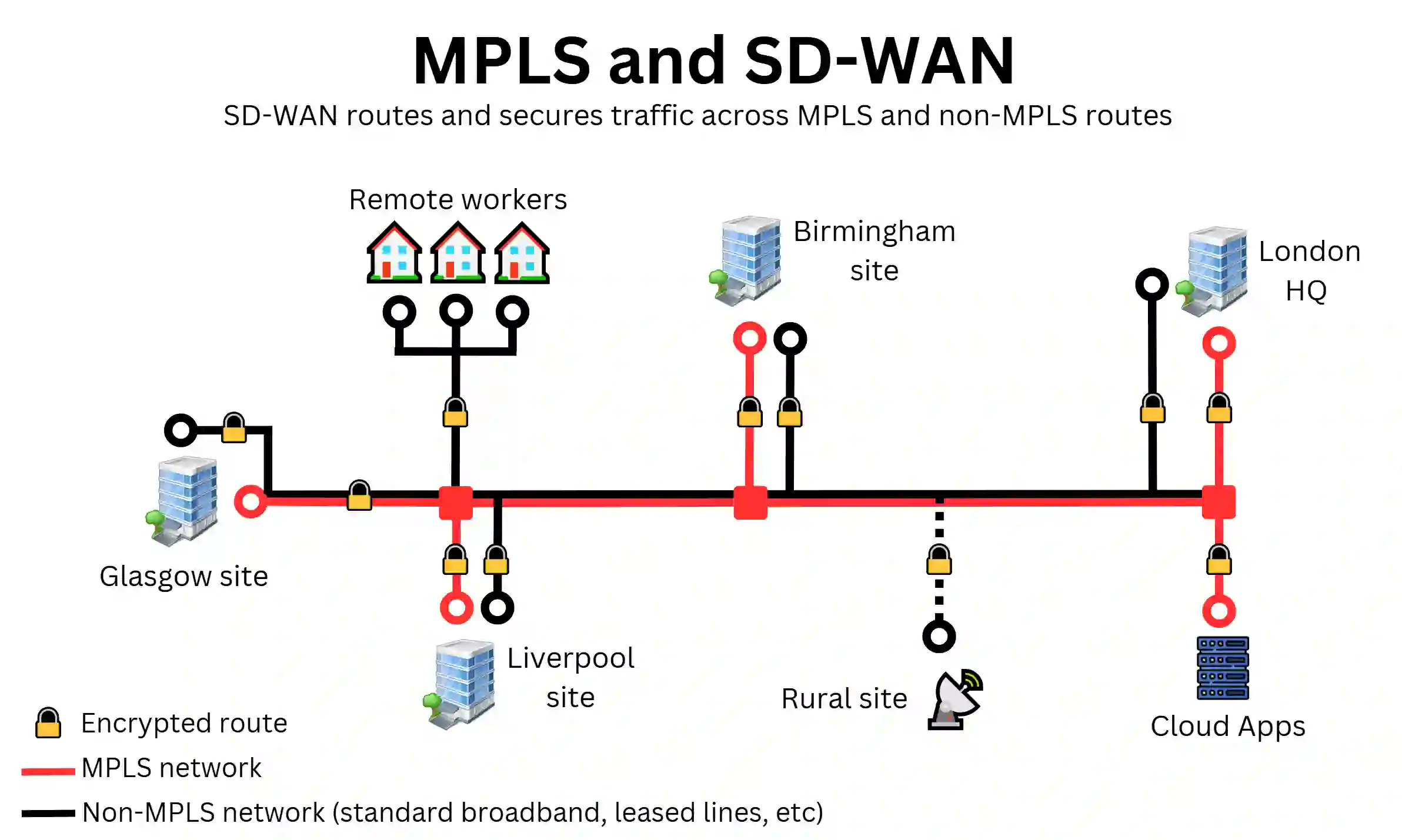
MPLS powers some of the lowest latency business wide area networks in the UK. its performance benefits are confined to its own label-switched network, leaving remote workers, secondary broadband, and cloud connections without its advantages, despite its high cost.
What’s more, MPLS lacks built-in encryption and security features, leaving your business network vulnerable without additional protection.
Enter SD-WAN, which brings optimised routing and cybersecurity to the entire business network, including MPLS, broadband, and even satellite connections like Starlink and OneWeb. It orchestrates and secures traffic across all connections, directing it based on real-time network conditions and predefined policies, while providing its suite of SD-WAN security features.
By combining MPLS with this powerful engine, businesses can benefit from four key enhancements:
- Auto-failover and load balancing for MPLS
- Improved performance for remote work
- Reduced cost by reducing the need for MPLS
- Enhanced MPLS security with SD-WAN
Auto-failover and load balancing for MPLS
MPLS networks include built-in redundancy and failover but require manual setup and can only redirect traffic through predefined Label Switched Paths (LSPs).
SD-WAN automates failover and load balancing, intelligently redirecting traffic based on real-time congestion and application priority. Traffic can be redirected across any redundant business broadband connection, whether its a wireless leased line, a satellite link, or even a basic copper wire connection.
This significantly enhances network resiliency at a much lower cost and without the hassle of additional MPLS deployments.
During network congestion, critical applications like VoIP, UCaaS and cybersecurity monitoring can continue relying on MPLS routes, while less-sensitive traffic like guest networks is offloaded to secondary connections.
Improved performance for remote work
Remote workers can access the business’s MPLS backbone by connecting to an MPLS-linked site via VPN. However, their experience ultimately depends on the journey from their remote connection to the MPLS edge, which is static and doesn’t form part of the Label Switched Paths.
SD-WAN enhances the performance of this segment by:
- Dynamically selecting the best route to the MPLS edge, adapting to congestion and performance fluctuations.
- Prioritising business-critical applications (remote VoIP, video calls) to ensure their performance.
- Providing end-to-end encryption and security, even beyond the VPN gateway.
Reduced costs by reducing reliance on MPLS
MPLS delivers top-tier performance, but its dedicated circuits are expensive, inflexible and take consuming to implement. Some business applications require MPLS-grade reliability, but this level of performance isn’t always necessary.
In fact, many businesses are now scaling their networks at a significantly lower cost by using SD-WAN to manage multiple cheaper broadband connections. This approach delivers comparable performance, ensures consistent security across the WAN, and significantly reduces both direct costs and opportunity costs, by as much as 50%.
Additionally, this leads to lower cybersecurity costs by consolidating security across the entire WAN using SD-WAN derivatives like SASE and Zero Trust Network Access (ZTNA) which eliminate the need for separate security solutions per connection type.
Enhanced MPLS security with SD-WAN
MPLS is more secure than public internet connections as it operates on a private, provider-managed network, but it lacks built-in encryption and advanced security controls. This makes it reliable but not inherently secure against modern cyber threats. SD-WAN delivers all of this not only across MPLS links, but across the entire business WAN, including remote and cloud connections.
See our section on MPLS security for more information.
Benefits and drawbacks of MPLS
Here is a summary of the main benefits and drawbacks of deploying or scaling MPLS at your businesses, including those arising from an SD-WAN integration:
MPLS benefits
- Guaranteed performance: SLAs backing MPLS connections commonly offer >99.99% uptime, <10ms latency, and negligible packet loss.
- High performance: Low latency and minimal jitter make it ideal for real-time applications like VoIP calls and financial trading.
- Advanced QoS: MPLS enables application-aware traffic prioritisation across multiple sites through its labelling system.
- Uses provider’s network: MPLS operates within a provider’s private network (outside public pathways) mitigating several cybersecurity threats.
- Global capabilities: MPLS allows global site-to-site connections via partner providers such as Orange (France), T-Mobile (Germany), and AT&T (U.S).
- Direct cloud & SaaS access: Provides dedicated links to AWS, Azure, Google Cloud, business VoIP phone providers, and key business SaaS platforms.
- Seamless SD-WAN integration: MPLS can easily integrate with SD-WAN to receive a performance, flexibility and security boost.
MPLS drawbacks
- High cost: Its high cost makes it prohibitive for small businesses or large-scale deployments across many locations.
- Limited flexibility: Not ideal for dynamic, cloud-first environments or remote work scenarios where broadband and SD-WAN offer greater agility
- Long deployment and scaling times: Setting up new MPLS circuits can take weeks or even months, delaying network expansion or business scaling.
- Lack of built-in encryption: MPLS does not encrypt data by default, requiring additional security measures like SD-WAN, VPNs, IPsec, etc.
- Provider dependence: Businesses are often locked into long-term contracts with a single MPLS provider, making changes or switching providers complex and costly.
MPLS security
MPLS technology is designed for low latency and high reliability, but not necessarily for security. It isolates traffic and avoids congestion, but lacks basic encryption, traffic inspection, and access controls, leaving it dependent on additional security layers.
Below, we outline MPLS’s built-in security features and the critical protections it lacks.
In-built MPLS security features
MPLS provides some security advantages over standard IP routing, including:
- Traffic isolation: MPLS uses Layer 3 VPNs (L3VPNs) to separate customer traffic within the provider’s backbone, ensuring that each business has a dedicated Label Switched Path (LSP).
- Avoids the public internet: MPLS does not traverse the open internet, reducing exposure to DDoS attacks, IP spoofing, and interception attempts.
- End-to-end path control: Unlike standard IP routing, MPLS paths are pre-established and not dynamically advertised, reducing the risk of route hijacking.
- Consistent performance: Since MPLS traffic is managed with strict QoS policies, it is less vulnerable to congestion-based attacks like Denial-of-Service (DoS) floods.
- Quality of Service (QoS): MPLS enables application-aware traffic prioritisation, ensuring VoIP calls, financial transactions, and real-time applications remain uninterrupted even during congestion.
Security gaps in MPLS
MPLS does not include many essential security measures, requiring businesses to implement additional protections:
- No encryption: MPLS traffic is not encrypted by default, meaning data could be intercepted if the provider’s network is compromised. Businesses must add IPsec, SSL, VPNs, or SD-WAN to secure sensitive data.
- No traffic inspection: MPLS does not provide intrusion detection, malware filtering, or deep packet inspection (DPI). Firewalls and advanced threat detection systems are required to monitor and block malicious activity.
- No access control: MPLS lacks user authentication or device verification. It only handles traffic transmission, meaning businesses must implement ZTNA, role-based access control (RBAC), or SD-WAN for identity verification.
Best practices for securing MPLS
Securing MPLS requires filling in these missing protections, but the best approach depends on business size, network complexity, and security needs:
- Smaller businesses: Encryption solutions like IPsec VPNs may be sufficient, while hardware firewalls and endpoint security tools help block external threats.
- Larger enterprises: Integrating SD-WAN, SASE, or cloud-based security solutions provides scalability, automation, and unified protection across MPLS and non-MPLS traffic.
A Managed Service Provider (MSP) can help assess network vulnerabilities and design a comprehensive security strategy, ensuring MPLS is protected without unnecessary costs or complexity.
In summary, it is best to avoid securing MPLS in isolation, but to adopt a holistic security approach that protects all connections simultaneously.
MPLS business implementations
MPLS has many benefits, but a simple implementation isn’t one of them. The process can take weeks to months, with network engineers required on-site(s) at various stages. Here are the key steps to implementing MPLS:
1. Assessment and planning
Before deploying MPLS, businesses must assess whether it aligns with their network needs, budget, and long-term strategy. Key considerations include:
- Why is MPLS needed? Is it for multi-site connectivity, compliance, or application performance gaps? Perhaps financial transactions are experiencing slow finality, or VoIP call quality is too often too low? MPLS is particularly beneficial for linking multiple locations into a unified, high-performance network.
- Replacement or integration? Will MPLS replace an existing Ethernet-over-VPN setup, or will it be integrated with SD-WAN to complement other network solutions?
- Is MPLS affordable? MPLS is usually only warranted for serious scaling or when low latency is non-negotiable, such as in business VoIP phone systems.
- Is MPLS practical? Rural businesses or those far from MPLS provider access points face unreasonably long installation times and high costs.
2. Choosing an MPLS provider
MPLS is available through two main types of providers:
- Business broadband providers: Companies like BT and Virgin Media with large MPLS backbones. These often bundle MPLS services with their existing broadband or leased line installations. Usually less flexible in terms of customisation, but offer comprehensive coverage and high-quality connections with cloud services.
- Managed Service Providers (MSPs): MSPs aggregate MPLS services from multiple carriers, providing businesses with a more flexible and tailored solution. They can offer multi-carrier MPLS, enhanced SLAs, security and network add-ons, and SD-WAN integration at a more competitive price.
When selecting a provider, businesses should evaluate:
- Network coverage and capacity: Ensure the provider covers all business locations and has nearby Points of Presence (PoPs) for optimal performance.
- Service Level Agreements (SLAs): Look for guarantees such as 99.99% uptime, low latency (<20ms between UK sites), and compensation for downtime.
- Pricing: Costs vary based on bandwidth, distance, and infrastructure type (e.g., MPLS over copper vs fibre optics).
- Scalability: Some providers support rapid bandwidth upgrades and new site additions without excessive costs.
- Security: Consider the provider’s offerings for firewalls, VPNs, encryption, etc.
- Cloud connectivity: Consider a provider with the necessary on-ramps or integrations with your required cloud and business VoIP phone providers.
- Installation times: MPLS installation may take between 4 weeks to 6+ months, depending on infrastructure requirements and PoPs.
3. Network design and configuration
MPLS typically becomes the backbone of a business WAN, so requires planning for performance, segmentation, and resilience from the start:
- Topology: Most businesses opt for an MPLS-over-VPN mesh network, which connects multiple sites and cloud services efficiently. Point-to-point MPLS is best for direct, high-priority connections.
- Segmentation: MPLS classifies and prioritises traffic using Forwarding Equivalence Classes (FECs), ensuring critical applications receive priority routing.
- Redundancy and failover: Implement MPLS built-in redundancy or add backup broadband connections managed by SD-WAN for automated failover.
- LAN-MPLS setup: MPLS must be properly configured with the business LAN. SD-WAN simplifies this by centralising network policies across MPLS and broadband links.
4. Deployment and testing
MPLS deployment requires a structured rollout to minimise downtime and ensure performance meets SLAs.
- Site surveys and infrastructure preparation: Engineers assess each site to ensure it has the necessary cabling, equipment, and power requirements before installation.
- Circuit provisioning and equipment setup: The provider installs the necessary fibre connections and integrates them into their MPLS core network. Businesses must configure routers, firewalls, and SD-WAN appliances (if applicable).
- Testing: IT teams conduct latency, QoS, and failover tests before full migration.
- Phased migration: Instead of switching all locations at once, many businesses deploy MPLS at a few test sites before expanding network-wide.
5. Ongoing management and optimisation
MPLS requires continuous monitoring and adjustment to maintain optimal performance, security, and cost efficiency.
- Continuous monitoring: Businesses use provider dashboards or third-party network monitoring tools to track latency, bandwidth usage, and traffic patterns.
- Adjusting QoS and bandwidth. As network needs change, MPLS QoS policies and bandwidth allocations must be reviewed and adjusted.
- Security and compliance updates: Organisations handling sensitive data (e.g., financial services, healthcare, and government) must ensure MPLS remains compliant with evolving cybersecurity regulations.
- Reviewing provider SLAs: Businesses should conduct periodic performance assessments with their provider to discuss upgrades, scalability, and potential cost optimisations.
Multiprotocol Label Switching (MPLS) FAQs
Our business broadband experts answer commonly asked questions on MPLS for UK businesses:
Does MPLS work in any type of internet connection?
Yes. MPLS is an overlay technology, meaning it can run over various connection types, including fibre, copper, and even wireless technologies like 5G business broadband and satellite business broadband.
However, its performance depends on the quality of the underlying connection, so its typically deploy over high-performance circuits like leased lines rather than standard SoGEA or even contended full fibre business broadband.
What are the cost considerations for implementing MPLS?
MPLS is more expensive than WANs running over the public internet via permanent VPN connections because it requires:
- Dedicated infrastructure, such as business leased line broadband or dark fibre.
- Extensive configuration and maintenance by providers.
- Strict SLAs guaranteeing uptime, latency, and service quality.
Costs depend on bandwidth, distance, SLA requirements, network complexity, and bundled services, see more here.
What’s the difference between Ethernet and MPLS?
Terms like “Business Ethernet” and “Business MPLS” are often used interchangeably by service providers to describe enterprise-grade wide area networks, even though they actually mean different things.
Ethernet is a Layer 2 technology that provides the fundamental framework for networking. It defines the rules, hardware, and protocols that enable data transmission over LANs and WANs. Ethernet can run over various transport mediums, including fibre and copper wires.
MPLS is a Layer 3 technology that operates on top of Ethernet to improve routing efficiency. It adds an intelligent overlay using label switching, which enables faster, more reliable, and traffic-prioritised connectivity across large networks.
Can MPLS work over wireless broadband?
Yes, but it is rarely deployed this way due to higher latency and variable performance. Wireless connections like mobile broadband and satellite are less stable than fibre, making it difficult for MPLS providers to offer strict SLAs.
However, MPLS over 5G backhaul is expected to become more viable as 5G network coverage and performance improve, particularly for industries needing low-latency connectivity in remote locations.
What’s the difference between MPLS and standard IP routing?
Standard IP routing requires routers to inspect each packet’s IP header at every hop to determine its next destination. This process slows down traffic and can cause congestion under heavy loads.
In contrast, MPLS traffic bypasses these repeated lookups by carrying pre-determined ‘fast-track’ labels. While both methods may use the same fibre infrastructure, MPLS ensures lower latency and more consistent performance by avoiding bottlenecks.
What is MPLS used for in the UK?
MPLS is primarily used by large enterprises, financial institutions, and public sector organisations that require secure, high-performance connectivity.
Common UK use cases include:
- Financial services: Low-latency connections to stock exchanges and trading platforms.
- Healthcare: Secure interconnectivity between hospitals and NHS data centres.
- Public sector: Compliance with data segregation and cybersecurity regulations.
MPLS is less common for SMEs due to its higher costs, but some still use it for business-critical applications.
Is MPLS essential for 5G private networks?
No, MPLS is not essential, but it can improve performance when connecting multiple private 5G sites or ensuring low-latency backhaul to data centres and cloud services.
In reality businesses can achieve similar results with SD-WAN, 5G “slicing”, or uncontended leased lines. If a 5G private networks is self-contained within a single site, MPLS offers little benefit since all traffic stays local within the private 5G core.

