A simple guide to VPNs for business
Business VPNs are an essential networking tool. They secure remote access to internal networks and are critical for connecting offices, physical sites, and cloud services over the internet.
However, there’s more than one type of VPN, and understanding how each is used across different scenarios is key to making informed, confident decisions as a business owner.
In this guide, we’ll break down how business VPNs work, the types available, how to set one up, and what to consider when integrating them with your broadband or network setup.
Contents:
- What is a VPN?
- How business VPNs work
- Types of business VPN
- How to set up a business VPN
- Integrating business VPNs with broadband
- Top business VPN providers
- Business VPN costs and pricing
- The future of business VPNs
What is a VPN?
A Virtual Private Network (VPN) is a technology that establishes a secure, encrypted connection between devices, sites or the cloud over the public internet. VPNs are:
- Virtual: The connection is software-based, rather than physical. It sits on top of the physical lines that carry data.
- Private: All data sent through the VPN is encrypted and shielded from unauthorised access.
- Network: It links two or more points into a single, secure network.
VPNs are best known for giving remote employees secure access to company networks, but their business applications go far beyond that.
IT teams often set up and manage their VPNs to connect branch offices, protect data in transit, enable secure access to internal and cloud systems, and ensure compliance with UK cybersecurity regulations.
Businesses typically avoid consumer-grade VPNs like NordVPN, as these lack secure access to internal resources and don’t offer the customisability, routing control or access management features necessary for cybersecurity compliance.
How business VPNs work
Business VPNs create a secure, encrypted tunnel between two or more points, such as an employee’s laptop and the company network, or between different office locations.
This tunnel behaves like a private link established over the public internet, shielding business data from interception or tampering.
Establishing a VPN connection involves four key steps:
Let’s take a closer look at each stage:
1. Establishing trust (handshake)
To initiate a VPN connection, both endpoints (peers) begin by verifying each other’s identity. This is typically done by sharing digital certificates, pre-shared keys, or login credentials with each other.
Once authenticated, both peers perform a cryptographic key exchange using protocols such as Diffie-Hellman or Elliptic Curve Diffie-Hellman.
This ensures they can agree on a shared set of encryption keys without ever exposing those keys to the wider internet.
2. Encrypted tunnel creation
Once trust is established, the VPN host forms an encrypted tunnel using a specified protocol such as IPSec, SSL/TLS, or WireGuard, depending on the use case. For example:
Network-layer VPNs like IPSec encrypt all traffic leaving a device. These are ideal for persistent site-to-site connections between offices.
Transport-layer VPNs like SSL/TLS typically secure traffic from a specific application (e.g. a web browser or remote desktop client), making them suitable for remote access.
Regardless of the protocol, the VPN tunnel acts as a protected pathway through which encrypted data flows, invisible to anyone outside it.
3. Data encapsulation
Before transmitting data over the VPN tunnel, the data is encapsulated. This means wrapping the data packet inside a new packet, along with an additional IP header, metadata needed for routing, and the encryption required to enter the tunnel.
This process hides the original packet’s source, destination, and contents. Beyond security, it also helps users bypass geo-restrictions, enforce network access control, or isolate sensitive traffic to avoid cybersecurity threats.
4. VPN data transmission
Finally, the encapsulated and encrypted data packets are transmitted across the public internet. Thanks to strong encryption algorithms like AES-256, even if the traffic is intercepted, it remains unreadable without the correct decryption keys.
When the data reaches the receiving endpoint, it is decrypted and decapsulated, restoring the original content. The data is then delivered to its intended destination: a business application, internal server, or cloud resource.
The VPN tunnel remains active for the duration of the session and can be closed at any time by either peer to end the secure connection.
Types of business VPN
There is no single categorisation for business VPNs. Instead, every VPN implementation combines specific features that suit different business use cases.
For example, a remote worker logging into the company network using a VPN will be using a solution with the following characteristics:
- Use case: Remote access
- Architecture: Client-to-site VPN
- Deployment: Self-hosted VPN
- VPN Protocol: SSL (Transport Layer)
Understanding these characteristics helps identify the type of VPN your business is using or which configuration best fits your operations. Let’s look at each element in more detail.
1. Use case
The use case defines the primary reason your business needs a VPN. This is usually the first factor that determines how the rest of the VPN setup will look.
- Remote access VPNs: Connect individual employees, authorised contractors or devices to the business network from outside the office. This is typical of hybrid, business travel or home-working setups.
- Site-to-site VPNs: Links multiple fixed locations, such as branch offices, warehouses or retail outlets, to operate as a single private network. Often implemented on top of MPLS or Business Ethernet networks.
- Intranet VPNs: Securely links teams or departments of the same organisation across geographic regions. It can also extend to temporary sites via SD-WAN.
- Extranet VPNs: Provides limited, controlled access to specific systems for trusted third parties such as suppliers or partners. These VPNs are typically configured with strict access controls to ensure external users can only reach designated resources.
- Cloud VPNs: Connect on-premises infrastructure to cloud platforms like cloud business VoIP phone providers, AWS or Microsoft Azure to support hybrid cloud environments.
2. Architecture
Architecture refers to how the VPN is structured, particularly in terms of how devices or networks connect to each other.
- Client-to-site VPNs: Individual users connect securely to a central network. These are typical in remote access scenarios, with users relying on VPN client software or browser-based access.
- Site-to-site VPNs: Connects multiple local area networks (LANs) together using VPN gateways (often business broadband routers or firewalls) to maintain always-on, encrypted links between sites.
- Hub-and-spoke VPNs: A site-to-site setup, where all remote sites connect through a central hub such as the head office. Ideal when resources and services are hosted at HQ for maximum performance and robust cybersecurity compliance.
- Mesh VPNs: All endpoints connect directly to each other, with no central hub. This offers more redundancy but is more complex to manage. Ideal for distributed, highly mobile teams like software developer teams or IoT deployments.
- VPN gateways for cloud: Establish secure, always-on tunnels between on-premises networks and cloud infrastructure, typically managed within the cloud provider’s networking settings.
3. Deployment
Deployment covers how the VPN is hosted, maintained, and delivered. This reflects how much control and responsibility your business has over the VPN infrastructure.
- Self-hosted VPNs: Managed internally using dedicated servers or network appliances. They offer maximum control and customisation but require in-house technical expertise. Only convenient for meeting stringent cybersecurity requirements.
- Managed VPN services: Outsourced to third-party providers who handle setup, security monitoring, and technical support. These are ideal for businesses that want strong protection without managing infrastructure.
- Cloud-native VPNs: VPNs hosted in the cloud. Best VPN deployment for fully remote teams without physical premises,those with little on-premise infrastructure, or those with a hybrid cloud-on-site service.
4. VPN Protocol
The VPN protocol is the technical standard underlying the VPN solution. It defines how data is encrypted and transmitted, whether at the network layer or app layer.
- IPSec: Operates at the network layer and is widely used for site-to-site VPNs. It encrypts all traffic leaving a device or network.
- SSL or TLS: Works at the transport layer and is commonly used for remote access VPNs. It is ideal for securing browser-based or app-specific connections.
- OpenVPN: An open-source VPN protocol used to build self-hosted VPNs. It’s flexible and widely supported, so it can be used for any setup and layer.
- WireGuard: A modern VPN protocol known for its speed and efficiency. It uses simpler code and is gaining popularity for quick-and-easy business VPNs.
- L2TP/IPSec: Combines Layer 2 tunnelling Protocol with IPSec for encryption. It is older and less commonly used today, but still supported by many systems.
- MPLS VPN: An enterprise-grade VPN designed for MPLS networks. It runs over the MPLS provider’s private network, rather than the public internet.
How to set up a business VPN
There is no single way to set up a business VPN. The deployment depends entirely on the use case, business size and wide area network architecture, with setups ranging from simple remote access VPNs to deploying persistent VPNs for an enterprise.
In any case, we cover four typical VPN configurations for real-world business needs:
1. Remote access VPN for a small team (self-hosted)
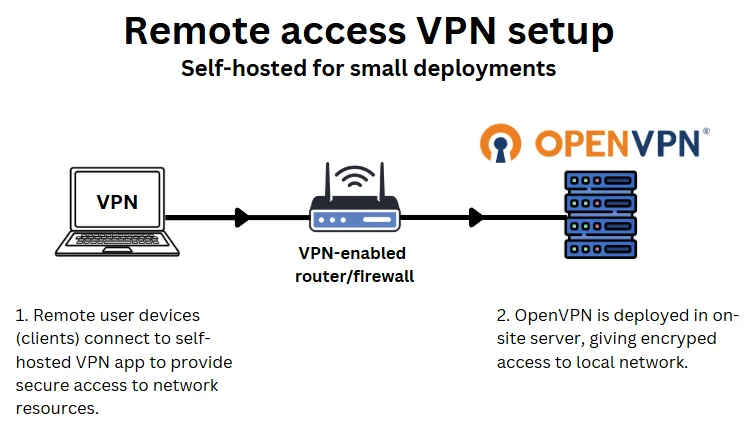
Who it’s for: SMEs with in-house or freelance IT support who want low-cost, secure remote access for employees working from home or on the move. For example, an independent accounting firm or a small design or marketing agency.
Small businesses with remote or hybrid teams often need secure access to internal systems such as file servers, CRMs, or remote VoIP solutions, particularly where SD-WAN is not in place.
Self-hosting a VPN remains a common approach because it’s cost-effective and relatively straightforward to set up using open-source tools like OpenVPN or WireGuard. However, it requires some technical know-how and ongoing in-house management.
Self-hosted VPNs can be deployed on-site or via a Virtual Private Server (VPS) hosted in the cloud or a data centre.
This setup typically requires:
- A VPN server (hosted on-site or via a VPS)
- VPN software such as OpenVPN or WireGuard
- VPN client applications installed on staff devices
- Firewall configuration and port forwarding
How its setup:
Your IT team installs and configures the VPN server, creates user credentials, and distributes connection profiles to staff.
Employees connect using a VPN client, either manually or via an always-on connection, encrypting their traffic and granting secure access to internal resources.
This setup provides complete control and low operating costs but relies on internal resources to monitor, maintain, and secure the VPN environment over time.
2. Managed VPN service (outsourced solution)
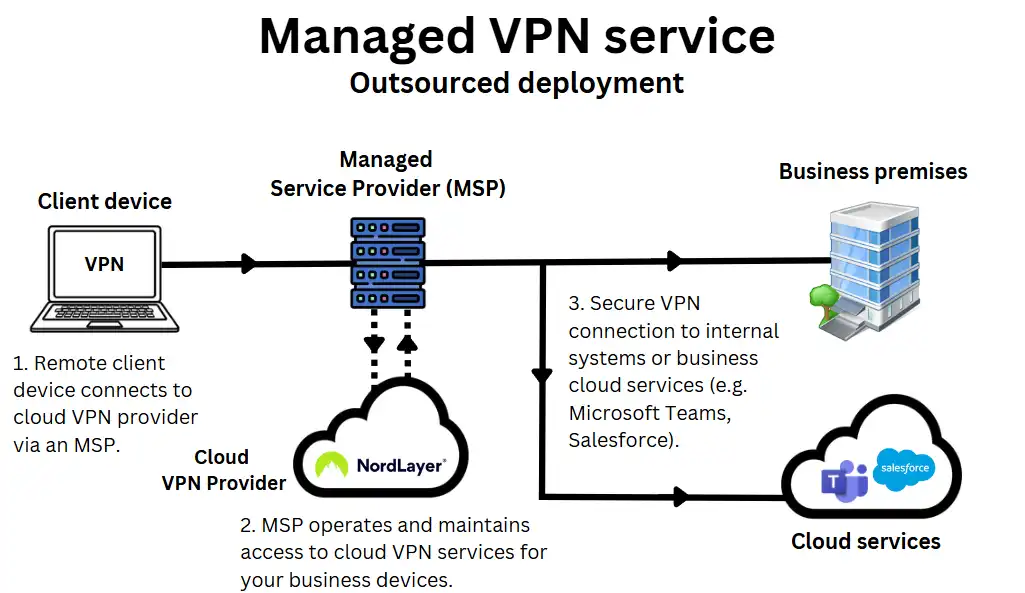
Who it’s for: SMEs without internal IT teams who need a secure VPN managed by an external provider or a business VPN platform such as NordLayer. For example, an independent dental practice, a recruitment agency, or a legal firm.
Many SMEs in the UK opt for a fully managed VPN service to avoid the complexity of configuring, hosting and maintaining their own VPN infrastructure.
This is particularly common among businesses without a dedicated IT team or those already working with an external MSP (Managed Service Provider) like Focus Group.
Managed VPN solutions are typically delivered as a subscription service. They are usually bundled into a wider managed IT support package that may include a business VoIP phone system, a leased line broadband connection and a cybersecurity SaaS.
On the MSP’s side, VPNs are implemented through third-party cloud VPN providers like Nord Layer or Perimeter 81, or their custom-built VPN, depending on the MSP’s needs.
This setup typically includes:
- A cloud-hosted or hybrid VPN managed by your provider.
- A centralised management console for access and monitoring
- VPN client apps or browser-based access for users
- Ongoing support, monitoring and updates handled externally
How it’s set up:
- Your MSP or provider handles the full deployment, including server configuration, user provisioning and security policies.
- Employees are given login details or VPN apps to connect securely, without needing to manage anything on their devices beyond the install.
- While most MSPs use third-party VPN platforms for convenience and scalability, some may also build and host custom VPNs, especially for larger client accounts with custom network requirements, on-premises infrastructure, or specific compliance needs.
- This setup offers convenience, fast rollout and minimal internal overhead, making it ideal for growing businesses or non-technical teams.
3. Cloud VPN for hybrid infrastructure
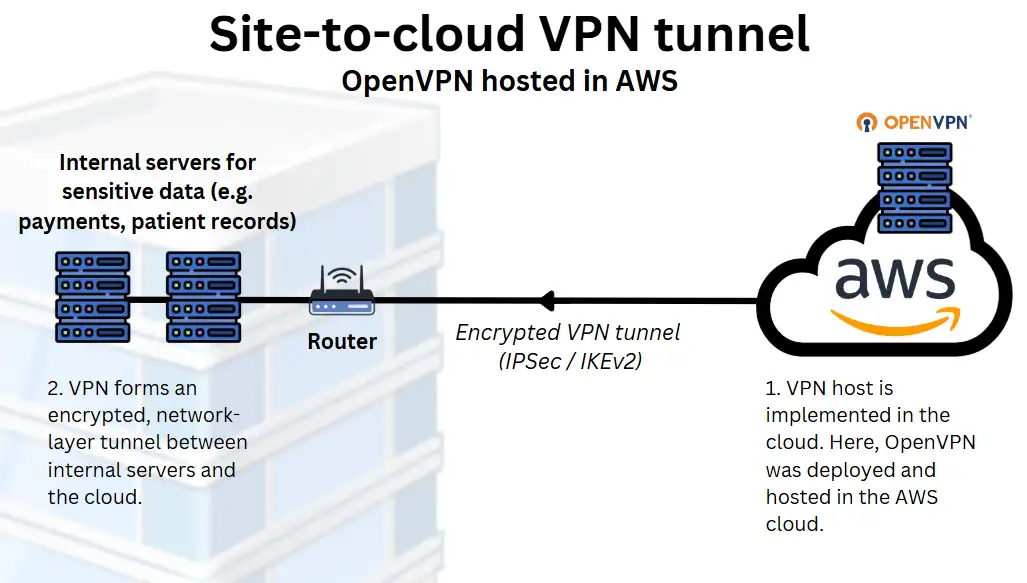
Who it’s for: Hybrid or cloud-native SaaS companies or digital agencies using AWS or Azure to link cloud-hosted apps with on-site resources.
Businesses operating across both on-premises and cloud environments often use a cloud VPN to connect these systems securely.
This setup is standard among SaaS providers, agencies, or tech-led SMEs that host applications or data in platforms like AWS, Microsoft Azure, or Google Cloud, but still run some local infrastructure for critical applications such as payments or patient data handling.
Cloud VPNs create a secure connection between a business’s physical network and a cloud-hosted network to ensure resources on each can communicate securely.
This setup typically includes:
- An active account with a cloud provider (e.g. AWS, Azure)
- A cloud VPN gateway
- A VPN-capable router or firewall on-premises
- A tunnel using a protocol like IPSec or IKEv2
How it’s set up:
Your IT team or managed service provider provisions a VPN gateway using your cloud provider’s network tools.
They then configure your on-site network hardware to establish a site-to-cloud VPN tunnel. This tunnel routes traffic securely between your office network and your cloud environment.
Cloud VPNs are ideal for hybrid infrastructure, as they maintain secure, reliable access between environments without needing everything hosted in the same place. They’re also scalable and well-supported by major cloud platforms.
4. Site-to-site VPN between physical locations
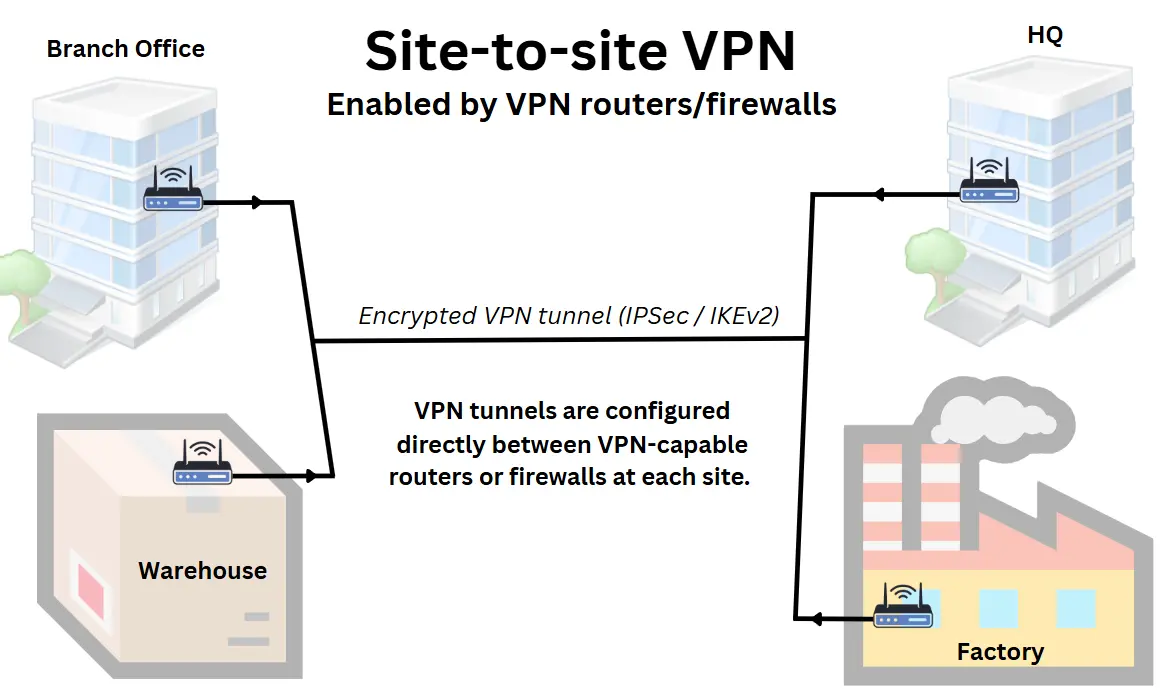
Who it’s for: Perfect for multi-site organisations, like a regional retail chain, a consultancy firm with offices across the UK, or a courier company, that require secure, always-on connectivity between branches without relying on SD-WAN for security.
Site-to-site VPNs to securely connect multiple LANs allows teams in different offices, warehouses or branches to access shared systems and data as if they were all in the same location.
Site-to-site VPNs are typically configured between routers, firewalls, or dedicated VPN appliances at each site, forming a permanent, encrypted tunnel over the public internet or private business networks like MPLS or Business Ethernet.
This setup typically includes:
- A VPN-capable router, firewall or VPN appliance at each location
- A static IP address or for each site or a dynamic DNS solution.
- A configured VPN tunnel using IPSec or similar network VPN protocol
- Routing rules and firewall adjustments
How it’s set up:
Your IT team or VPN service provider configures a secure VPN tunnel between each site using IPSec. Once connected, the tunnel runs in the background continuously, routing encrypted traffic between locations without requiring any action from staff.
This setup is a cost-effective, stable choice for businesses centralising systems such as VoIP platforms, file servers or internal apps, while keeping multiple sites securely connected.
💡 Site-to-site VPN solutions are slowly losing ground to SD-WAN for multi-site network security and optimisation.
Integrating business VPNs with broadband
If you’re planning to run a VPN over your existing small business broadband connection, whether for remote access, site-to-site connectivity, or secure access to cloud services, there are a few technical considerations to get it working reliably.
Here’s what to keep in mind when integrating a VPN with your broadband setup:
1. Most VPNs work over standard broadband
VPNs don’t require a specialist connection to function. The encrypted tunnel can be formed over SoGEA, full fibre business broadband, or even business satellite broadband.
This applies to both the broadband used at your main site and the connection used by the client or remote employee at home.
2. For on-site VPN hosting, hardware matters
If you’re self-hosting a VPN server or linking multiple locations via site-to-site VPN you’ll need VPN-capable routers/firewalls.
3. Leased lines offer better performance for VPNs
A leased line connection that offers guaranteed speeds, lower latency, and symmetrical upload/download will improve VPN performance and reliability, especially for multiple users or persistent site links.
In rural areas without access to fibre, wireless leased lines and EFM offer alternative, Ethernet-grade solutions. Alternatively, compare business broadband deals to find the best connection for your premises at the best price.
4. VPNs will affect your connection speed
VPNs introduce bandwidth overhead by encrypting and encapsulating data before transmission. This will reduce your available speed, particularly during high-bandwidth activities like file transfers or UCaaS video conferencing.
A faster, uncontended broadband connection can help mitigate this on the business side, though performance will still depend on the client’s broadband if they connect remotely.
Top business VPN providers
Choosing the right VPN solution for your business depends on how much control you want, the scale of your network, and whether you have in-house IT or use a managed service provider.
VPN providers don’t all offer the same thing. Some only provide open-sourced software, others offer complete cloud-based services, and many are fully implemented by a third-party managed service provider using tools from across the VPN stack.
Here’s a breakdown of the main types of VPN providers used by UK businesses, starting from the most basic to the more managed:
1. VPN software providers (self-hosted tools)
These providers offer VPN software that must be installed, configured, and hosted by your IT team or a third-party provider.
They offer flexibility and control, but require more technical capability. They’re ideal for businesses that want complete control over their VPN architecture, or need to integrate into existing firewalls, routers or cloud servers.
- OpenVPN Inc. (Access Server): A commercial version of the open-source standard, often used in custom business VPN setups.
- WireGuard (project): A lightweight, modern protocol known for speed and simplicity; used widely in DIY or embedded VPN environments.
- SoftEther VPN: A multi-protocol VPN server platform suitable for complex configurations or legacy support.
2. Cloud VPN providers
These are fully hosted, subscription-based VPN services. They provide the infrastructure, software, and management tools and are ideal for small and mid-sized businesses that want secure access with minimal overhead.
These platforms are best for businesses that want fast rollout, low maintenance, and secure remote access without building their network infrastructure.
- NordLayer: A business VPN built on NordVPN’s infrastructure, with central user management and device control.
- Perimeter 81: Popular among UK SMEs for its ease of use, integrated firewall, and zero trust networking features.
- Twingate: A modern, app-focused alternative to traditional VPNs, with granular access control and strong identity integration.
- Cloudflare Zero Trust: Offers VPN-like functionality through identity-based access rules, DNS filtering, and secure tunnels.
3. Enterprise-grade VPN providers
Providers offering hardware or software appliances that combine VPN functionality with advanced firewalling and enterprise network controls.
These systems are typically deployed by mid-sized and larger businesses, or those with specific security and compliance requirements.
- Cisco Meraki: Offers cloud-managed networking with built-in VPN features, commonly deployed in UK businesses via MSPs.
- Fortinet (FortiGate): Combines high-performance VPN, deep packet inspection (DPI) and threat management in one device.
- Sophos XG Firewall: Includes integrated remote access and site-to-site VPNs, with strong threat protection features.
- SonicWall: Offers secure VPN appliances with optional cloud-based management, used in both SME and enterprise environments.
4. Managed VPN providers
These providers offer fully managed VPN and networking services, using a combination of the VPN solutions above, like cloud VPNs, enterprise-grade firewalls, or custom-built open-source solutions.
They handle everything, from configuration to deployment to ongoing support and network monitoring:
- Focus Group: A leading UK VPN provider offering managed VPNs as part of broader IT and connectivity services.
- Elite Group: Provides managed networking and VPN services alongside VoIP features and business broadband.
- Boxx Communications: Offers secure VPN access as part of its small business VoIP, IT and telecoms packages.
Business VPN costs and pricing
VPNs are rarely sold as standalone services. In most business scenarios, they are either built using open-source tools (lowest cost), bundled into cloud platforms (medium cost), or included as part of a wider IT or networking package (highest cost), such as managed services or WAN deployments.
The total cost depends heavily on the type of setup, how it’s deployed, and whether your business manages it internally or outsources it.
Here’s a quick comparison of typical UK VPN scenarios and what they cost:
| Scenario | Estimated cost | Notes |
|---|---|---|
| Fully self-hosted remote access VPN | £0 (direct cost) | Uses open-source software (e.g. OpenVPN, WireGuard). Cost = time, setup, and basic hardware. |
| Cloud VPN platform (e.g. NordLayer, Perimeter 81) | £7–£15 per user/month | Subscription-based. Scales with users. Includes access control and support. |
| MSP-delivered managed VPN (SME package) | £50–£200/month | Often bundled with IT support, VoIP or broadband. Pricing depends on the services included. Usually unlimited users. |
| Enterprise VPN with firewall (e.g. Cisco, Fortinet) | £1,000+ setup + ongoing license | Usually part of wider network/security deployment. Managed by an internal IT team or a managed service provider. |
| VPN included in a leased line | Bundled into leased line broadband costs | Typically included in larger connectivity contracts for multi-site businesses. |
The future of business VPNs
Business VPNs are still essential for secure remote access, encrypting traffic, and bypassing geo-restrictions, but their role is evolving as newer networking technologies take the lead:
Competition from SD-WAN and SASE
New solutions like SD-WAN now include encryption by default, along with smarter traffic routing and application-level control. It can replace both traditional site-to-site VPNs and remote access for workers at the same time.
Meanwhile, security models are shifting toward Zero Trust Network Access, where users get identity-based access to specific apps, not the full network. Combined solutions like SASE (Secure Access Service Edge) are becoming more common in cloud-first and hybrid workplaces.
VPNs are becoming default
VPNs are becoming a default addition where SD-WAN isn’t offered. Networking products like Business Ethernet and MPLS often include site-to-site VPN and VPN for remote access as part of the product, rather than as a stand-alone.
VPNs will remain important for small businesses and niche deployments
VPNs remain useful for self-hosted remote access, securing public internet use, and enabling location-specific access. For many SMEs, they offer a simple, familiar way to protect traffic without overhauling the network.
And even as the tech behind it evolves, the term “VPN” will likely remain part of product branding given how popular a solution it has become.

