How can my business survive a cyberattack?
While there are no statistics on the number of attempted business cyberattacks, a government survey suggests that as many as 39% of businesses reported attacks in 2022.
While most are unsuccessful, the few that succeed force businesses to deploy significant financial and human resources to mitigate the attack and deal with the financial, reputational, and legal fallout.
This article presents three case studies of businesses and institutions that suffered and survived a major cyber assault. We take each case apart to ensure we can all learn from their mistakes.
💡 Key takeaways:
- RoyalMail (2023): The best response is to have a contingency plan, stay calm, and avoid paying for ransomware; attackers feed off fear.
- UK Electoral Commission (2023): Existing cybersecurity vulnerabilities should not be taken lightly, as they significantly increase your exposure.
- Tesco Bank: Non-compliance with regulations exposes your business to million-pound fines.
The Royal Mail ransomware attack of 2023
This high-profile case made the BCS’s biggest cyberattacks of 2023 list, not only because of the million-pound costs to Royal Mail but also because it affected one of the UK’s critical infrastructure services.
Timeline
Here is a summary of what happened:
| Date | Event | Impact |
|---|---|---|
| Nov 2022 | Emotet Detected | Malware found on servers; risk of further attack. |
| Early Jan 2023 | Ransomware Attack Starts | LockBit RaaS disrupts Belfast center. |
| Mid-Jan 2023 | Public Acknowledgment | Disruption to international services announced. |
| Feb 2023 | Ransom Ultimatum | $40M demand made; Royal Mail opts not to pay. |
| Late Feb 2023 | Service Restoration Begins | £10M spent on cybersecurity; services resuming. |
| Ongoing | Security Enhancements | Upgrades to malware defenses, staff training. |
Cybersecurity background
While Royal Mail’s pre-attack cybersecurity measures are not publicly available, this sophisticated ransomware attack easily breached their defences.
As part of the UK’s Critical National Infrastructure (CNI), Royal Mail would have been expected to adhere strictly to Network and Information Systems (NIS) regulations. These regulations mandate enhanced security measures for operators of essential services like Royal Mail to protect against network and information systems risks.
The ransomware attack
The crisis unfolded when Royal Mail detected the Emotet malware on its servers at its Heathrow Worldwide Distribution Centre in November 2022 but could not contain it. The attackers managed to steal 44GB of data, primarily concerning staff records for about 200 employees.
Royal Mail publicly acknowledged the ransomware attack on January 10, 2023, after the situation escalated into a full-blown attack that included disrupting Royal Mail’s operations. Customers and businesses experienced international shipping delays and service interruptions as the company refused to pay the ransom.
At the height of the crisis, the attackers infiltrated a distribution centre near Belfast, causing the printers to uncontrollably print the attackers’ ransom demands, a signature move of Lockbit cybergang’s ransomware attack.
💡 Who is LockBit? It is a ransomware group known for its ransomware-as-a-service (RaaS) tactics. They recruit affiliates to deploy their ransomware, sharing the profits from successful ransom payments. They became prominent as late as 2019 and have continuously improved their malware variants, including Lockbit 2.0 and Lockbit 3.0.
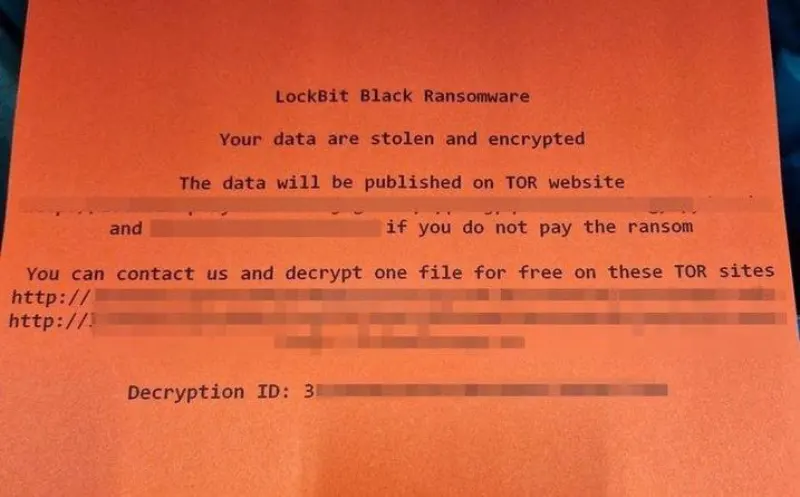
The attackers then explicitly threatened, “We are ready to make a discount, remove the stolen information and provide a decryptor for $40m,” pushing Royal Mail between a rock and a hard place.
Ultimately, the company chose not to pay the exorbitant ransom, instead focusing on containing the attack, restoring services, and fortifying its cybersecurity defences.
Royal Mail’s response
Royal Mail was initially unable to contain and eliminate the threat despite appearing to follow compliance closely. They communicated with the relevant authorities and publicly announced the breach after the situation escalated to disrupt operations.
The key takeaway is that Royal Mail did not buckle under the pressure of disrupted operations, hacked printers, and stolen data to pay the $40m ransomware; instead, it focused on restoring services and improving security measures. This highlights the importance of an appropriate cybersecurity Incidence Response Plan (IRP).
Subsequently, Royal Mail invested significantly in upgrading its cybersecurity infrastructure (Part of its £10 million emergency investment). This included integrating more advanced threat detection systems, enhanced encryption practices, stricter access controls to safeguard against future incidents, and improving staff training to make them less vulnerable to phishing.
It appears that Royal Mail’s good response complied with regulations. Despite the large scale of the breach, regulators have not publicly confirmed any fines or ongoing investigations.
💡 The high-profile ransomware attack led global law enforcement to take down Lockbit’s website
Financial impact
Financially, the attack was a heavy blow to Royal Mail. It aggravated an already challenging financial year, contributing to a substantial half-year loss of £319 million. The direct costs related to mitigating the ransomware attack and bolstering cybersecurity defences post-attack were reported to be around £10 million.
Key lessons
- Acting in compliance with regulations does not guarantee you will remain 100% secure. Still, it will help your business avoid significant scrutiny or fines, especially if it handles finances or takes care of critical infrastructure.
- Ransomware attackers use fear tactics to get companies to pay ransom. However, this comes at a heftier price than not giving in and undertaking all the necessary steps to contain it and ramp up security.
Quotes and Media Reactions
Here are a couple of quotes summarising the situation from all angles:
“Negotiations lasted nearly a month, from January 12 to February 9, but Royal Mail went silent for nearly a week before that final date. It never appeared willing to pay the ransom and employed several stalling techniques.” – the register
“Coming out of a breach is, in itself, a painful ordeal, as quite often the breached organisation – to find the aspects in its cyber security architecture that need improvement – goes through in detail all the steps that led to the breach initially. ” – Dirk Schrader, VP of Security Research at Netwrix
“This incident is a stark reminder that even high-profile entities like Royal Mail are not immune to cyber threats. It underscores the necessity for continuous enhancement of cybersecurity measures across all sectors” – Bleepingcomputer.com
The UK Electoral Commission 2023 data breach
Timeline
| Date | Event | Impact |
|---|---|---|
| Aug 2021 | Undetected Breach | Unauthorized access to the Commission’s servers; breach begins but goes undetected. |
| Oct 2022 | Suspicious Activity Detected | Commission alerted by suspicious login patterns; breach confirmed. |
| Aug 2023 | Public Notification | Electoral Commission publicly acknowledges the breach nearly a year after detection. |
| Ongoing | Security Enhancements | Strengthening of network login requirements, improvement of threat monitoring, and firewall policy updates. |
Cybersecurity background
Before the breach, the Electoral Commission had infamously attempted to become certified under the Cyber Essentials scheme. Still, it failed in multiple areas, including updating Windows on all its laptops and a dated version on some staff’s mobile phones.
While these vulnerabilities weren’t directly exploited (the attack targeted its email servers), it highlighted a lack of stringent practices, something that attackers likely became aware of.
The data breach: What happened?
The data breach was first noticed in October 2022 due to suspicious login request patterns, but it was later determined that it occurred as early as August 2021.
During that time, hostile actors successfully infiltrated the Commission’s systems. They gained access to its email systems, control setups, and copies of electoral registers held for research purposes and permissibility checks on political donations.
The accessed data included reference copies of the electoral registers covering nearly every registered voter in Great Britain from 2014 to 2022 and those registered as overseas voters. The registers contained voters’ names and addresses but did not include details of those registered anonymously. The breach also compromised the email system, potentially exposing personal communications and information submitted through web forms and emails.
While none of the stolen data has been published online or seen in public domains, the possibility that this valuable information could surface or be utilised for malicious intent, like spreading misinformation for political gain or a massive phishing operation, remains a concern.
💡 Sanctions: The UK government has sanctioned a China-backed company that was supposedly behind the Electoral Commission data breach, which allowed hackers to access information about millions of voters. The new Cold War is certainly digital.
The Electoral Commission’s response
Upon detecting these suspicious activities, the Electoral Commission swiftly engaged with cybersecurity experts and national security bodies, including the National Cyber Security Centre (NCSC).
The first steps involved an immediate assessment of the intrusion to understand the scope and to secure the compromised systems. This included identifying and isolating affected parts of their network to halt any further unauthorized access.
💡 Compliance: The Commission reported the incident to the Information Commissioner’s Office (ICO) within 72 hours of confirming the breach, as required by cybersecurity regulations.
Forensic investigations remain ongoing (as of May 2024) to determine how the breach occurred and what systems were affected. It will also be critical to determine a lack of compliance and any fines that may be imposed.
The Electoral Commission is taking significant steps to overhaul and strengthen its cybersecurity infrastructure in response to the breach. This includes updating and tightening network login requirements, enhancing threat monitoring capabilities, and revising firewall policies to better protect sensitive data.
💡 Poor communication: Despite fulfilling their legal obligation, the electorate chose not to tell data subjects about the breach, which is certainly not the norm.
Financial Impact
There is no publicly available information on the costs incurred by the Electoral Commission yet. However, historical cases and the scale of the breach will likely elevate costs into the millions of pounds in incident response, system remediation and upgrades, legal and regulatory costs, and long-term security enhancements. This remains TBD.
Key Takeaways:
- Early detection systems: The Electoral Commission took over a year to detect the breach, highlighting the importance of early detection mechanisms and the need for continuous monitoring of IT systems.
- Data breaches: People remain largely unaware of the impact of a data breach. If their e-mails, phones, and addresses are available to a malicious actor disguised as a government entity, it could conduct very sophisticated phishing operations. This could include e-mails, calls or even parcels sent in the name of her Majesty’s government.
💡 Is this why paper voting remains relevant? In part, yes. Paper voting is not immune to controversy, inefficiencies and high costs, but at least most cybersecurity threats can be avoided. This is something blockchain technology can truly revolutionise.
Quotes and Media Reactions
“Secondly, if it were all the mailboxes in all the past and current employees, there would be an absolute treasure trove of employee and external information to mine… That would mean anyone/everyone should be very suspicious of any email or physical mail they receive from the government for a while.” –Mark Ridley, director at Ridley Industries
“There’s not enough information there for someone to go and cast a vote as you, and certainly not enough information to conduct ID theft.” However, “It doesn’t help if the organization responsible for the integrity of elections gets hacked. It raises concerns about the overall security posture of the systems that safeguard our democratic processes.” – Professor Alan Woodward, computer scientist specializing in security, University of Surrey
The UK’s democratic process is significantly dispersed, and key aspects remain based on paper documentation and counting, which means it would be very hard to use a cyberattack to influence the process. –The Electoral Commission
If they knew about the breach in October 2022, why has it taken 10 months to provide notification? The excuse that they ‘had to remove the actors and their access” and “put additional security measures in place” points to a very cumbersome technology estate and worrying lack of responsiveness. – Dewi Price, CIO at Inizio Digital.
Tesco Bank: The 2016 funds theft
Timeline
| Date | Event | Event Description |
|---|---|---|
| Pre-2016 | Insufficient cybersecurity | Tesco Bank conducted routine security assessments but did not fully address vulnerabilities in their systems. |
| November 5-6, 2016 | Cyberattack | The cyber attack began, targeting the bank’s debit card and transaction processing systems. |
| November 5-6, 2016 | Emergency Response | Tesco Bank detected unusual transactions and halted online banking and contactless payments to prevent further losses. |
| Late 2016 to 2017 | Post-Attack Remediation | Tesco Bank undertook significant security overhauls and implemented changes to enhance cybersecurity measures. |
| October 2018 | Fine Imposed | The FCA fined Tesco Bank £16.4 million for failing to prevent the foreseeable attack. |
Cybersecurity background
Before the attack, there were indications of vulnerabilities in Tesco Bank’s systems that were not fully addressed, including issues in the design of their debit card and controls against financial crime.
The bank’s systems did not react quickly enough to unusual transaction patterns, suggesting that their fraud detection algorithms were either outdated or not configured aggressively enough to handle sudden spikes in transaction volumes on individual accounts.
There was an obvious lack of adequate investment in up-to-date and robust cybersecurity measures, especially since Tesco Bank is bound by stringent FCA cybersecurity regulations.
The cyberattack: Unauthorized transactions
Attackers targeted the bank’s debit card and transaction processing system, simultaneously conducting unauthorized transactions from multiple customer accounts. 8,261 customer accounts were compromised during the attack, with fraudulent transactions occurring mostly over a short period.
The attackers exploited weaknesses in debit card security features like PIN verification and transaction authorizations. They are believed to have used a form of ‘guessing attack’ to figure out card details or possibly exploited a bank’s card authorization protocol flaw to mimic or bypass checks for fraudulent transactions.
The attack was largely automated, with the attackers deploying scripts or bots that rapidly performed unauthorized transactions. This method enabled the mass execution of transactions quickly, amplifying the attack’s impact and the amount stolen.
In response, Tesco Bank immediately froze online transactions to stem the losses and assured affected customers of full reimbursement, which was promptly executed.
💡 Lack of Monitoring: Tesco Bank’s financial crime monitoring systems failed to detect or prevent suspicious transactions in real-time, indicating a possible failure to set thresholds for unusual activity or in the responsiveness of their alert systems.
Communication
Once confirmed, Tesco Bank promptly acknowledged the security breach, informing customers and the public that unauthorized transactions had been detected on several customer accounts.
The bank communicated using multiple channels, including direct emails to affected customers, updates on its official website, and press releases to the broader media.
They also provided regular updates regarding the ongoing investigation, the steps to secure their systems, and the progress of customer reimbursements. The communication was fairly transparent, with Tesco Bank disclosing the nature of the breach, the number of accounts affected, and the specific actions customers needed to take, such as changing passwords or monitoring their accounts for unusual activity.
Financial Impact
The financial impact of the Tesco Bank hack in 2016 was significant. It affected direct monetary losses, subsequent fines, and longer-term reputational and operational costs. Here are the details:
| Category | Description | Estimated Cost |
|---|---|---|
| Direct Monetary Loss | Immediate financial theft from customer accounts during the cyber attack. | £2.5 million |
| Regulatory Fines | Fine imposed by the Financial Conduct Authority (FCA) for failing to prevent the foreseeable attack. | £16.4 million |
| Customer Reimbursement | Costs for reimbursing affected customers for the stolen amounts. | £2.5 million |
| Operational and Remediation Costs | Expenses related to enhancing cybersecurity measures, including software and hardware upgrades, and hiring external consultants. | Not specified, estimated in millions |
| Reputational Damage | Impact on customer trust and market perception, potentially affecting customer retention and acquisition. | Long-term financial impact, not directly quantifiable |
Conclusion
Take cybersecurity seriously! There is a lack of awareness due to poor media coverage of these issues, but the reality is that global digitisation, together with improvements in business broadband, are providing increasing avenues for hackers to rake a massive profit at your expense.
Even if you’re a small business and think, ” It won’t happen to me,” you are vulnerable, even if your small business is not the main target of the Lockbit hacking group or any government-backed companies.
How can my business improve its cybersecurity?
For small businesses without critical infrastructure or data, take the Cyber Essentials Certification to prevent 90% of attack vectors at a cost of a few hundred pounds.
For medium businesses or those with more critical systems, the Cyber Essentials Plus Certification is more rigorous and includes an audit, costing 1,000 pounds.
Larger businesses and institutions should have Cyber Essentials done across multiple sites, at the very least. This will help them qualify for a government-supported insurance policy, which requires a business to have an annual turnover of over 20 million pounds.
Additionally, they should ensure compliance with all pertinent regulations, including FCA regulations for financial institutions (Like Tesco Bank) and NIS regulations for critical services (like Royal Mail)

