How do Next-Generation Firewalls (NGFW) work?
Next-Generation Firewalls (NGFWs) are advanced firewalls capable of inspecting the contents of internet data in real time to detect and block threats like malware before they reach local networks or cloud environments.
This article explains how NGFWs work, how they differ from traditional firewalls, their benefits, and how to choose the right one for your business application.
Content highlights
- How does a Next-Generation Firewall work?
- Next-Generation Firewalls vs traditional firewalls
- Why businesses need Next-Generation Firewalls
- Types of Next Generation Firewalls (NGFWs)
What is a Next-Generation Firewall (NGFW)?
A Next-Generation Firewall (NGFW) is an advanced, enterprise-grade type of firewall that expands on the core functions of traditional firewalls.
Instead of simply allowing or blocking traffic based on surface-level information like IP addresses, ports, or protocol headers, an NGFW goes deeper by decrypting and inspecting the actual contents of data packets.
This process, called Deep Package Inspection (DPI), can uncover hidden threats like malware, suspicious behaviour, or data leaks, even when they are embedded inside encrypted HTTPS traffic (which is how most modern attacks are delivered).
This deep visibility gives security teams comprehensive insight into internet traffic across office networks, cloud platforms, and virtualised systems, with only a modest performance trade-off during decryption and inspection.
NGFWs also leverage continuous threat intelligence, automatically updating themselves with indicators of new cyberattacks so they can detect both known and emerging threats in real time.
They can be deployed in multiple forms, depending on where protection is needed. For example:
- A hardware appliance protecting an office’s local area network
- Software securing virtualised applications in a data centre
- A cloud-delivered firewall-as-a-service protecting distributed cloud apps, users and sites
How does a Next-Generation Firewall work?
Next-Generation Firewalls (NGFWs) work by deeply inspecting internet traffic at the network edge, similar to how a high-security border checkpoint screens travellers and goods entering a country
If traditional firewalls act like quick roadside checks (glancing at number plates and IDs), NGFWs operate more like airport security. Every packet goes through X-ray scans, identity verification, and real-time intelligence checks before being allowed through.
To achieve this without causing major delays, NGFWs rely on specialised hardware processors and parallel inspection engines that analyse each packet in just milliseconds. However, this level of scrutiny (especially when decrypting HTTPS traffic) does introduce some performance overhead.
Here’s what happens to a data packet as it passes through a NGFW:
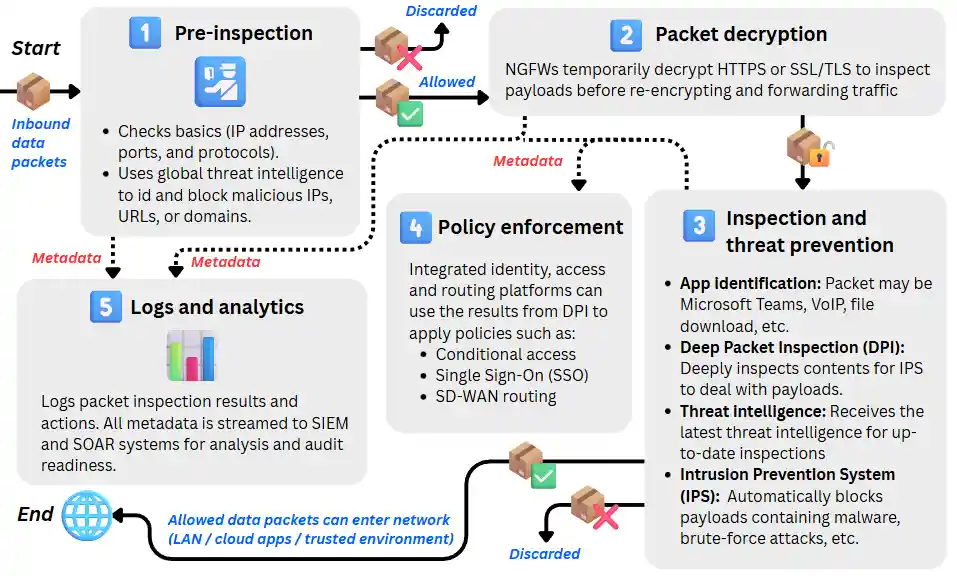
1. Pre-inspection: Basic filtering and reputation checks
Before deep analysis begins, the NGFW applies traditional firewall logic, verifying IP addresses, ports, and protocols to ensure each packet aligns with basic routing and access rules.
At the same time, it performs lightweight pre-filtering using global threat intelligence databases to instantly block traffic from known malicious IPs, URLs, or domains.
If a packet matches a known threat or violates a routing rule, it’s dropped immediately, conserving processing resources. Packets that pass these checks proceed to deeper inspection.
This early triage dramatically reduces load on the NGFW’s inspection engines and prevents obvious threats from consuming compute cycles that should be reserved for advanced analysis.
2. SSL/TLS inspection (packet decryption)
Because the vast majority of modern internet and site-to-site traffic is encrypted (HTTPS, SSL/TLS), NGFWs must temporarily decrypt packets to inspect their payloads.
Using certificate-based keys or trusted man-in-the-middle (MITM) inspection methods, the firewall:
- Terminates the encrypted session
- Decrypts and inspects the traffic
- Re-encrypts it before sending it onward
This cryptographic process (not the ensuing inspection itself) is the single most resource-intensive stage of NGFW operation. It requires significant CPU power, hardware crypto accelerators, entropy generation, and per-session caching.
As a result, independent tests consistently show throughput drops of 40-60% when full SSL/TLS inspection is enabled, both at hardware NGFWs and cloud-based NGFW/FWaaS platforms.
For traffic that cannot be decrypted (true end-to-end encrypted applications such as Signal or WhatsApp), the NGFW still analyses metadata, including destination IP, session frequency, connection behaviour and traffic volumes.
These indicators can still reveal command-and-control (C2) patterns, data exfiltration attempts, or malicious tunnelling activity.
3. Deep inspection and threat prevention
Once traffic is decrypted, the NGFW activates its full stack of inspection engines, operating across the network and application layers, using multiple analytic techniques in parallel.
Application identification (Layer 7 awareness)
The NGFW uses protocol decoding, signature matching, and behavioural heuristics to classify traffic by application, distinguishing between services like Microsoft Teams, Dropbox, or custom SaaS APIs.
This allows granular, application-level policy enforcement (e.g., allow corporate OneDrive, block personal Google Drive), something traditional firewalls cannot do.
Deep Packet Inspection (DPI)
The payload of each packet is examined in detail to identify malicious code, embedded macros, or attempts at data exfiltration. DPI unpacks compressed archives, decodes file formats, and matches byte patterns against malware signatures and exploit heuristics.
Threat intelligence correlation
Real-time lookups against cloud-based threat feeds enable the firewall to detect known indicators of compromise (IOCs), malware signatures, and command-and-control communications as they emerge within live traffic.
Intrusion Prevention System (IPS)
Working in tandem with DPI, the IPS applies signature-based, anomaly-based, and behavioural detection to block active exploits, brute-force attacks, and zero-day attempts. Advanced NGFWs leverage machine learning to baseline “normal” network behaviour and trigger alerts when deviations suggest compromise.
Performance considerations
All of these inspection engines run in parallel using hardware acceleration (ASICs or NPUs), allowing the NGFW to perform deep analysis in microseconds while keeping throughput high and latency low (unlike the previous decryption step).
4. Policy enforcement and zero trust
Once the deep inspection and threat prevention are complete, the NGFW can go further and enforce context-aware access controls as part of Zero Trust Network Access (ZTNA).
When it is integrated with Identity and Access Management (IAM) systems such as Microsoft Entra ID, Okta, or Google Identity, it can align packet-level data with user and device identities, giving security teams granular access control.
Access decisions can be based on multiple attributes uncovered during DPI, including:
- Application type: Such as a mobile-based VoIP call through Microsoft Teams
- User identity: Such as a middle manager accessing internal HR tools
- Tokens and certificates: Such as a valid Microsoft 365 session token or a trusted SSL certificate
- Code signatures: For example, a digitally signed software update or verified executable
5. Logging, analytics, and continuous monitoring
Every decision (allowed, blocked, or flagged) is logged with full metadata, including timestamp, user identity, application, policy, and threat indicators.
These logs are streamed to Security Information and Event Management (SIEM) and Security Orchestration, Automation, and Response (SOAR) systems for correlation, analytics, and automated response.
This enables organisations to conduct post-incident investigations, detect multi-stage attacks, and meet compliance requirements through detailed audit trails.
Machine learning–enhanced analytics can also surface trends, such as recurring intrusion attempts or emerging attack patterns across global telemetry.
Key features of Next-Generation Firewalls
All NGFWs share a set of core features that distinguish them from traditional firewalls and other network security tools.
Encrypted traffic inspection (SSL/TLS Inspection)
NGFWs have the core capability to decrypt and inspect SSL/TLS sessions, providing full, real-time visibility into encrypted payloads. After inspection, traffic is re-encrypted and forwarded securely, maintaining visibility without compromising privacy or compliance.
Deep Packet Inspection (DPI)
NGFWs are unique in that they can analyse the actual content of data packets in real time, not just their headers. This allows them to uncover hidden malware, exploits, and policy violations that would otherwise pass undetected.
DPI enables identification of specific applications and behaviours, forming the foundation for contextual policy enforcement and precise access control.
Intrusion Prevention System (IPS)
If DPI gives NGFWs deep visibility, built-in IPS capabilities give them active defence. The IPS detects and blocks known exploits, brute-force attempts, and zero-day attacks in real time.
By combining signature-based detection with behavioural analysis, the IPS functions as an automated, always-on protection layer within the firewall framework.
Integration with complementary security solutions
Modern NGFWs continuously share and receive security telemetry with other platforms such as threat intelligence feeds, Identity and Access Management (IAM), and SIEM/SOAR systems.
Their network-edge visibility makes them a central component of zero trust security architectures, both as a data source for analytics and as an enforcement point for access policies.
Next-Generation Firewalls vs traditional firewalls
Next-Generation Firewalls (NGFWs) are the natural evolution of traditional network firewalls.
Both sit at the edge of a network, inspecting the flow of data packets as they enter and leave. However, traditional firewalls focus mainly on filtering based on IP addresses, ports, and protocols.
At the same time, NGFWs go further, inspecting the contents of traffic in real time and correlating what they find with global threat intelligence.
This allows them to be significantly more powerful at detecting threats and strengthening business-wide security by sharing their findings across other systems.
That said, traditional firewalls remain useful in many contexts. They’re simpler to deploy, more affordable, and introduce less latency, making them well-suited for scenarios where advanced inspection isn’t critical.
The table below summarises their key differences across functionality, performance, integration, and practicality:
| Feature | Traditional firewall | Next-generation firewall (NGFW) |
|---|---|---|
| Core function | Filters traffic based on IP addresses, ports, and protocols. | Inspects and analyses traffic content using Deep Packet Inspection (DPI). |
| Inspection depth | Surface-level (header-only) inspection. | Full-packet inspection including payload, applications, and user context. |
| Threat detection | Limited to basic rule-based filtering. | Detects malware, exploits, zero-day threats, and policy violations in real time. |
| Encryption handling | Cannot decrypt encrypted traffic (SSL/TLS). | Performs SSL/TLS decryption and inspection to analyse encrypted data safely, at the expense of performance. |
| Intrusion prevention | Requires a separate IPS device. | Includes an integrated Intrusion Prevention System (IPS) for automated blocking. |
| Application awareness | Sees traffic as generic data streams. | Performs application-level filtering (Layer 7), recognising apps like Teams or Dropbox. |
| Threat intelligence integration | None or very limited. | Actively connects to global threat intelligence feeds for live reputation checks. |
| Policy enforcement | Based on static IP and port rules. | Enables identity-based and context-aware policies via IAM, like Microsoft Entra ID. |
| Performance | Fast and lightweight with minimal latency. | Despite specialised hardware, SSL/TLS decryption reduces performance by 40-60%. |
| Complexity | Simple to deploy and manage; few configuration layers. | More complex setup; integrates with multiple cloud and identity systems. |
| Cost | Low initial and maintenance costs; ideal for small budgets. | Higher upfront cost; delivers broader, enterprise-grade protection. |
| Performance overhead | Minimal, since no decryption or DPI occurs. | Moderate/High; DPI and encryption handling require specialised hardware. |
| Deployment options | Primarily on-premises hardware or basic virtual appliances. | Available as hardware, virtual, or cloud-managed firewalls. |
| Ideal use case | Small or low-risk networks needing basic perimeter defense. | Enterprise, hybrid, and cloud environments requiring deep visibility and integration. |
Why businesses need Next-Generation Firewalls
NGFWs have become a crucial component of modern zero-trust enterprise security.
Their ability to inspect traffic deeply and in real time allows them to detect hidden threats, enforce access policies, and feed intelligence to other security tools.
While smaller networks might still rely on traditional firewalls or cloud-native protection, organisations managing hybrid infrastructure, remote access, or sensitive data need NGFWs to maintain visibility, trust, and control across all layers of their operations.
Below are the most impactful ways NGFWs strengthen business security.
Securing business wide area networks (sites, cloud, data centres)
In modern enterprise networks, data no longer stays within a siloed network perimeter. Workflows require constant communication between on-premises systems, branch offices, and multiple cloud applications and services.
To enable this, businesses deploy secure wide area networks, connecting these environments through Business Ethernet, VPNs, MPLS lines, and in some niche cases, dedicated dark fibre lines.
Hardware deployed at the edge of these environments (local area networks, cloud gateway, or data centres) acts as intelligent checkpoints between interconnected systems.
They decrypt, inspect, and re-encrypt traffic using Deep Packet Inspection to uncover malicious payloads, policy violations, or misconfigurations, even within the organisation’s own private network.
Traditional firewalls treat internal or site-to-site traffic as inherently trustworthy. NGFWs, by contrast, extend zero trust principles across the entire enterprise, continuously verifying every packet and connection, whether it originates from the internet or another branch office.
The hardware NGFW can detect:
- Hidden malware within site-to-site transfers or cloud syncs
- Misconfigured or unauthorised workloads communicating laterally
- Sensitive data moving to unapproved destinations
Enabling zero trust secure remote and hybrid work
When employees work remotely, their devices connect through VPNs or SD-WAN tunnels to access corporate resources. A traditional firewall can only confirm that an encrypted session exists, not what’s actually inside it.
A cloud-delivered NGFW (FWaaS) or virtual NGFW deployed at the edge or cloud gateway decrypts and inspects this traffic using DPI, revealing application types, credentials, and behavioural patterns.
It then feeds this information to Identity and Access Management (IAM) platforms to enable conditional access and Single-Sign On (SSO) decisions based on real observed context, not just static credentials.
For example, an IAM might allow access to Microsoft 365 if the session originates from a trusted corporate laptop with a valid token, but deny access if the same user suddenly logs in from an unknown device or network.
The NGFW enforces these IAM decisions physically, blocking or quarantining non-compliant traffic in milliseconds. Together, the NGFW and IAM integration deliver true zero trust for remote and hybrid workforces, continuously verifying every user, every device, and every connection.
Protecting virtual workloads and multi-cloud environments
Many business applications no longer run on fixed servers but instead reside in virtual machines or cloud platforms, such as AWS, Microsoft Azure, or Google Cloud. These environments can expand, contract, or migrate between clouds at any time, depending on business needs.
Virtual NGFWs are designed to protect these flexible, software-based environments. Instead of being installed as physical devices, they run as software inside the cloud itself.
Their job is to monitor and secure the constant flow of information between cloud apps and services (called east-west traffic) to make sure nothing suspicious or unauthorised slips through.
Even as applications are created, updated, or moved across different clouds, virtual NGFWs keep enforcing the same security rules. They verify every connection, data exchange, or API call to ensure it adheres to company policy and does not conceal malware or data leaks.
This kind of protection is vital for businesses that rely on cloud-based operations, as traditional firewalls at the network edge simply can’t “see” what’s happening inside the cloud.
Preventing advanced and zero-day threats
Cyberattacks evolve faster than static defences can adapt. NGFWs combine DPI, behavioural analytics, and real-time threat-intelligence feeds to detect both known and emerging threats.
DPI reveals what’s inside network traffic (malware signatures, payloads, command sequences), while cloud-based intelligence networks continually update each NGFW with the latest data on zero-days and active campaigns.
This means that if a new ransomware variant appears on the other side of the world, NGFWs in your network can block it within minutes of discovery.
The integrated Intrusion Prevention System (IPS) acts reflexively, automatically blocking, quarantining, or terminating suspicious sessions before IT teams are even alerted.
Both hardware and virtual NGFWs can deliver this capability, but FWaaS extends it globally, applying protection to every remote user and endpoint through the provider’s distributed inspection network.
Meeting compliance and audit requirements
In highly regulated industries (finance, healthcare, defence, and public services), NGFWs provide the visibility and audit trails regulators require.
Regulations such as GDPR, HIPAA, PCI DSS, and ISO 27001 demand evidence of continuous network monitoring, data protection, and incident traceability.
An NGFW with DPI can:
- Detecting and blocking data exfiltration attempts (e.g., personal or financial data leaving the network)
- Maintaining detailed audit logs showing who accessed what, when, and how
- Providing forensic evidence for cybersecurity compliance audits or breach investigations
Hardware NGFWs are often preferred here for their predictable performance and data sovereignty guarantees. However, virtual NGFWs in regionally compliant clouds are increasingly used for hybrid environments, and cloud NGFWs are becoming increasingly compliant-compatible.
Enhancing network performance through SD-WAN
When integrated with an SD-WAN solution, NGFWs can actually improve performance (despite the extra inspection) by providing deeper visibility into traffic.
By identifying the nature of each flow (VoIP call, file backup, CRM session), the NGFW enables SD-WAN to route traffic dynamically over the most secure and efficient path.
For example:
- Low-risk SaaS traffic can go straight to the internet through a direct internet access link.
- Sensitive HR or financial data can be routed through encrypted VPN tunnels or dedicated point-to-point leased lines.
The combination of NGFW, SD-WAN, and complementary cloud-based tools such as CASB, FWaaS, and SWG forms the foundation of Secure Access Service Edge (SASE), a model that merges performance and zero trust security under one architecture.
Securing third-party integrations and supply chain connections
Organisations frequently exchange data and APIs with vendors, contractors, or supply-chain partners, prime targets for attackers.
Recent incidents, such as the 2025 M&S supply-chain breach, highlight how a single compromised partner can cascade across an entire ecosystem.
NGFWs inspect these integrations at the application layer, verifying that inbound and outbound connections behave as expected. They enforce partner-specific rules, ensuring that only authorised APIs or data exchanges occur, and detect anomalies that suggest tampering or unauthorised access.
In cloud environments, virtual or FWaaS-based NGFWs can secure these inter-organisational connections without deploying hardware at each site.
Types of Next Generation Firewalls
Modern NGFWs come in multiple delivery models, allowing organisations to choose how and where inspection and enforcement take place.
Each model provides the same core capabilities but is tailored for specific deployment environments and operational needs.

Hardware NGFWs
Hardware NGFWs remain the highest-performing and most reliable option. These dedicated physical appliances are installed on server racks at the edge of physical networks to handle traffic inspection locally and in real time.
Because all packet processing happens within the device itself, there’s no latency from outsourcing inspection to the cloud. This makes hardware NGFWs the standard choice for securing high-throughput or mission-critical environments where performance and reliability are non-negotiable.
They are most commonly used in large sites, corporate campuses, or regulated industries that need predictable performance and physical control over their security infrastructure.
Key characteristics include:
- Maximum throughput and ultra-low latency, ideal for environments with heavy or time-sensitive traffic.
- Dedicated processors and ASICs for parallel deep packet inspection, encryption/decryption, and threat prevention at wire speed.
- Physical isolation and rugged reliability are essential for regulated or air-gapped networks (e.g., government, healthcare, manufacturing).
- Customisable form factors, such as hardened or fanless units for industrial or remote installations.
- Built-in redundancy and failover support for continuous uptime in critical operations.
- Despite all of these, performance reductions should be expected, mainly from the heavy encryption/decryption.
Virtual NGFWs
Virtual NGFWs provide the same deep inspection and threat prevention as hardware firewalls but run entirely in software within virtual machines, containers, or cloud environments. They are designed to extend NGFW security into cloud platforms and remote data centres where physical NGFWs can’t be deployed.
For example, if a business hosts workloads or runs projects in the cloud (i.e., AWS or Azure), that traffic is preferably not sent through its main on-premises hardware NGFW, as it would consume critical bandwidth.
Instead, IT teams can spin up a virtual NGFW inside the cloud (alongside the projects), inspecting and securing traffic locally between workloads and users.
This ensures consistent protection and policy enforcement for the project or the specific workloads without additional hardware. While virtual NGFWs can’t match the raw performance of ASIC-powered appliances, they’re far more agile and scalable, ideal for hybrid networks and fast-changing cloud projects.
Virtual NGFWs also use flexible cloud-style licensing rather than physical appliance models. Businesses can deploy them through cloud marketplaces on a pay-as-you-go basis, bring their own license from the vendor, or choose throughput-based tiers.
Key characteristics include:
- Easily deployed on AWS, Azure, Google Cloud, or private data centres.
- Provides local protection for cloud workloads, securing traffic without wasting resources of the main on-premise NGFW.
- Elastic scalability, adjusting automatically with workload demand.
- Consistent security policies across hybrid and multi-cloud environments.
- Quick, code-based deployment through orchestration or Infrastructure-as-Code tools.
Cloud-delivered NGFWs (Firewall-as-a-Service or FWaaS)
Cloud-delivered NGFWs move all firewall functionality into the cloud. Instead of installing hardware devices or managing virtual firewalls, organisations can subscribe to a Firewall-as-a-Service (FWaaS) platform operated by a security vendor such as Palo Alto Networks, Zscaler, or Check Point.
All traffic (from users, devices, and branch sites) is securely routed to the vendor’s global inspection points, where deep packet inspection, intrusion prevention, and threat intelligence correlation occur in real-time.
This provides consistent security and access policies for every user and location, without the organisation having to run or maintain its own firewall infrastructure.
Because everything is handled by the provider, FWaaS offers universal coverage, zero maintenance, and seamless integration with cloud-based cybersecurity solutions like SASE, SD-WAN and IAM.
The trade-offs are reliance on the provider’s cloud network and typically higher latency compared to on-premises inspection. However, this latency is often offset by the vendor’s globally distributed points of presence (PoPs) and network optimisation.
FWaaS performance continues to improve as providers expand capacity. For instance, Zscaler now operates over 150 global PoPs, Palo Alto Prisma Access around 100+, and Netskope over 60, reducing the distance users travel to reach inspection points and shrinking real-world latency.
As a result, while FWaaS is especially well suited to remote-first and cloud-native organisations that prioritise flexibility and uniform security, it is increasingly replacing on-premises NGFWs as the default choice for modern businesses.
Key characteristics include:
- Fully managed service, hosted and maintained by the security vendor.
- Global reach, securing traffic for any user or device, regardless of location.
- Instant scalability, with inspection capacity adapting automatically to demand.
- Native integration with SASE, ZTNA, and IAM.
- No hardware or software upkeep, reducing cost and operational complexity.
Choosing a Next-Generation Firewall
Choosing the right NGFW depends on your network size, infrastructure, and security priorities.
These are the steps that businesses typically take when choosing:
- Assess your environment: Identify whether your traffic primarily runs on-site, in the cloud, or across hybrid networks.
- Match the deployment model:
- Hardware NGFWs for high-performance, on-premises protection.
- Virtual NGFWs for securing workloads inside virtual or cloud data centres.
- Cloud-delivered NGFWs for distributed teams and remote users.
- Evaluate scalability and management: Look for a NGFW provider that offers centralised policy control, automation, and easy integration with IAM or SIEM tools.
- Check performance and compliance: Ensure throughput, latency, and encryption inspection meet your organisation’s requirements.
- Review provider: Choose an IT provider that uses trusted vendors like Palo Alto Networks, Fortinet, or Check Point with proven cloud and hybrid capabilities.
How are Next-Generation Firewalls developing?
NGFWs are continuing to evolve in response to cloud adoption, the explosion of connected devices, and new classes of attacks that bypass traditional signature-based security.
The next generation focuses on intelligence, automation, and scalability, making them faster, smarter, and better suited to distributed, hybrid networks.
AI and machine learning-driven detection
While NGFWs already rely on global threat intelligence feeds for known attack signatures, AI and machine learning add the ability to recognise unknown or zero-day threats that don’t yet exist in those databases.
AI models run by cybersecurity providers analyse live traffic patterns such as command sequences, session timings, or payload entropy to detect subtle anomalies that may indicate an exploit in progress.
These models are continuously trained in the cloud using data collected across thousands of customer firewalls, meaning each device benefits from shared learning.
In practice, this lets NGFWs flag and contain new threats within minutes, without waiting for a vendor to release updated signatures. The result is a self-improving system that detects and mitigates emerging attacks faster than human analysts could.
Cloud-native and distributed architectures
Business networks are becoming increasingly cloud-centric and globally distributed. As a result, NGFWs are also aligning with how modern applications and users operate.
Vendors are increasingly deploying NGFW inspection engines at multiple points of presence (PoPs) around the world, bringing cloud-based inspection closer to the user or workload. This translates to improved performance (lower latency, better scalability and consistency of policy enforcement) of cloud-delivered NGFW services in the hopes of increasing their market share.
Expanded protection for IoT and operational technology (OT)
As the use of smart devices, sensors, and autonomous systems grows, so do the threats that can originate from these devices. This is increasing demand for deep packet inspection (DPI) within these IoT systems, and the need for NGFWs to extend visibility and protection deep into these environments.
Modern NGFWs can now understand non-standard OT and IoT protocols, identify and profile connected devices, and enforce micro-segmentation, isolating critical assets from vulnerable or unknown nodes (much like VLAN segmentation in local networks).
Lightweight NGFW agents are even being deployed at the edge of IoT networks or built into gateways, protecting devices such as industrial sensors, robots, drones, and connected vehicles.
This granular control prevents compromised devices from serving as an entry point for attacks into the wider corporate network.
Hardware acceleration and programmable data planes
To keep pace with ever-increasing network speeds and encryption volumes, NGFWs are leveraging programmable ASICs, FPGAs, and data-plane acceleration technologies.
These allow firewalls to keep up and inspect encrypted traffic at line rate without creating bottlenecks. In the cloud, the same concept is achieved through virtual acceleration, where providers dedicate high-performance compute resources to sustain throughput for customers with demanding workloads.
The result is that full deep-packet inspection and intrusion prevention can now occur at speeds of 100 Gbps or higher, making NGFWs suitable even in the most advanced applications.
Preparing for quantum-safe security
Looking ahead, NGFWs are beginning to adopt quantum-resistant cryptography and advanced inspection techniques for increasingly encrypted traffic.
Future-ready NGFWs will be able to authenticate and inspect quantum-safe encryption standards, maintaining visibility into high-entropy traffic without compromising privacy.
Vendors are also developing container-native firewalls that can operate within microservices architectures, securing workloads that dynamically spin up and down.

