Virtual Local Area Networks (VLANs)
VLANs are the hammer and chisel of local area network administrators. It’s a foundational tool for shaping how traffic flows within a business site.
Whether separating teams, securing sensitive systems, or prioritising real-time communications, VLANs give businesses precise control over network traffic without the cost or complexity of additional hardware.
This article explains how VLANs work, why they’re used, and how to configure them across various environments, from small offices to multi-site enterprises.
Contents:
- What is a VLAN?
- How does a VLAN work?
- Key benefits of VLANs
- Setting up VLANs
- VLAN business use cases
- VLAN security vulnerabilities
What is a VLAN?
A VLAN (Virtual Local Area Network) is a virtual sub-network within a larger network that allows organisations to segment traffic by device, user, department, traffic type, etc.
For example, users who authenticate as “network admins” are placed in a “Management VLAN”, giving them access to LAN configuration tools. Similarly, data identified as VoIP traffic is assigned to a “Voice VLAN” to prioritise call quality and minimise latency.
This traffic and these users may connect from different parts of the network, such as WiFi access points, other buildings or floors, or even remotely via VPN, but they’re grouped virtually into the same subnet.
Some common VLANs and how business users and devices are assigned to them are illustrated below: 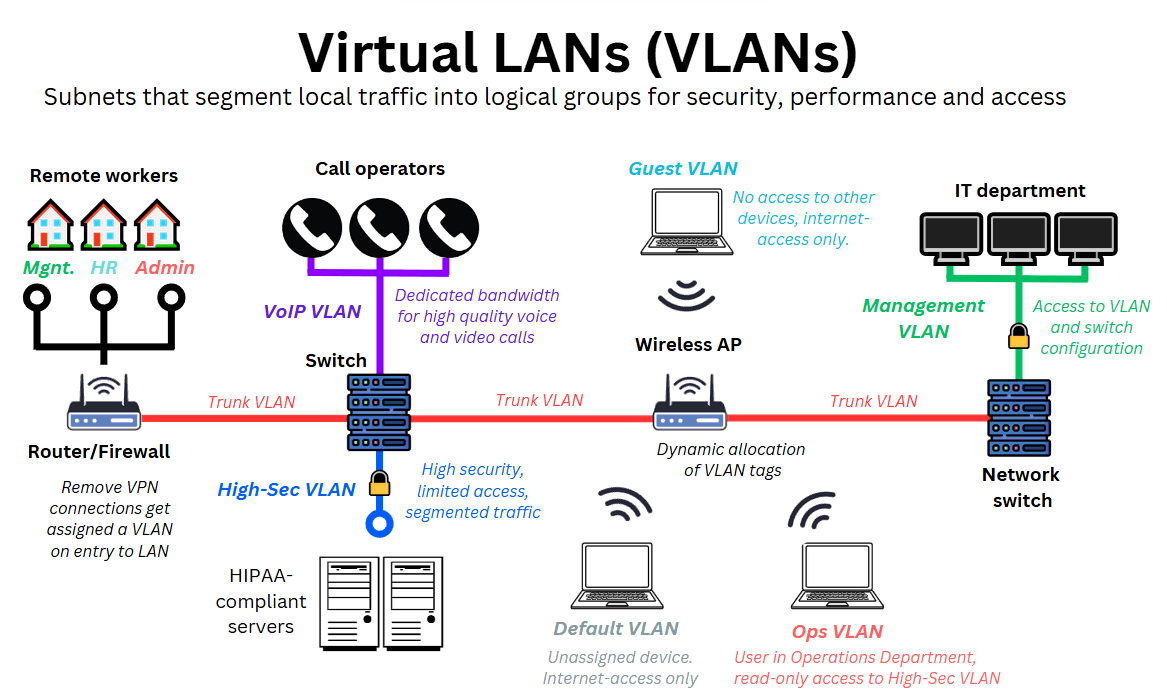
This approach gives network administrators granular control over access, traffic flow, and user privileges, without the need to build separate physical networks with their routers, switches, and cabling.
How does a VLAN work?
In simple terms, VLANs (Virtual Local Area Networks) divide a business’s network into logical, isolated sub-networks. This improves security, performance, and control without a separate physical infrastructure.
VLANs operate by “tagging” the network traffic that devices (e.g., laptops, PCs, servers) generate within the local network. This tagging doesn’t happen at the device level, but at key junctions in the network infrastructure, such as managed network switches and WiFi access points.
These VLAN tags allow the network to identify each data packet (called an “Ethernet frame” in this context) and apply specific policies based on predefined rules.
VLAN tags can be assigned based on various criteria, including:
- Device identifiers (e.g., MAC address)
- User logins (e.g., via 802.1X authentication)
- Access ports (physical switch ports)
- Data types (e.g., voice or video)
- Device types (e.g., security cameras)
- Remote connections (e.g., via VPN)
- Zero Trust Network Access (ZTNA) policies (e.g., based on device security posture)
Once traffic is tagged, network switches and routers use these tags to route, secure, prioritise, or isolate traffic according to the rules defined for each VLAN.
In the following sections, we’ll break down the key components that make VLANs work:
VLAN Tagging (802.1Q)
VLANs are assigned to local internet traffic at the physical switches and routers within a business LAN, such as an office, shop or industrial site network, etc.
At these network junctions, Ethernet frames (i.e., LAN data packets) are tagged with VLAN labels that assign them to a unique VLAN subnet.
This tagging process relies on a globally standardised protocol called IEEE 802.1Q, which supports up to 4,096 VLANs within a single local network.
Dynamic and fixed VLAN assignment
There are two distinct ways in which Ethernet frames are assigned VLANs:
Fixed VLAN assignment
VLAN IDs are statically assigned to all traffic coming from a specific switch or router access port. This ‘hardcoded’ method is ideal for fixed devices like servers, desktop PCs, security cameras, etc., ensuring consistent access control and clear traffic segmentation.
Dynamic VLAN assignment
VLAN IDs are assigned dynamically based on attributes like device type, user credentials, traffic type, or connection method. This is especially useful for environments with wireless access points or remote users, where devices and users change frequently.
Dynamic VLAN tagging is particularly powerful in modern, flexible work environments where users operate across multiple locations, devices, and roles, often requiring different levels of access and network behaviour.
The diagram below illustrates both dynamic and fixed VLAN tagging:
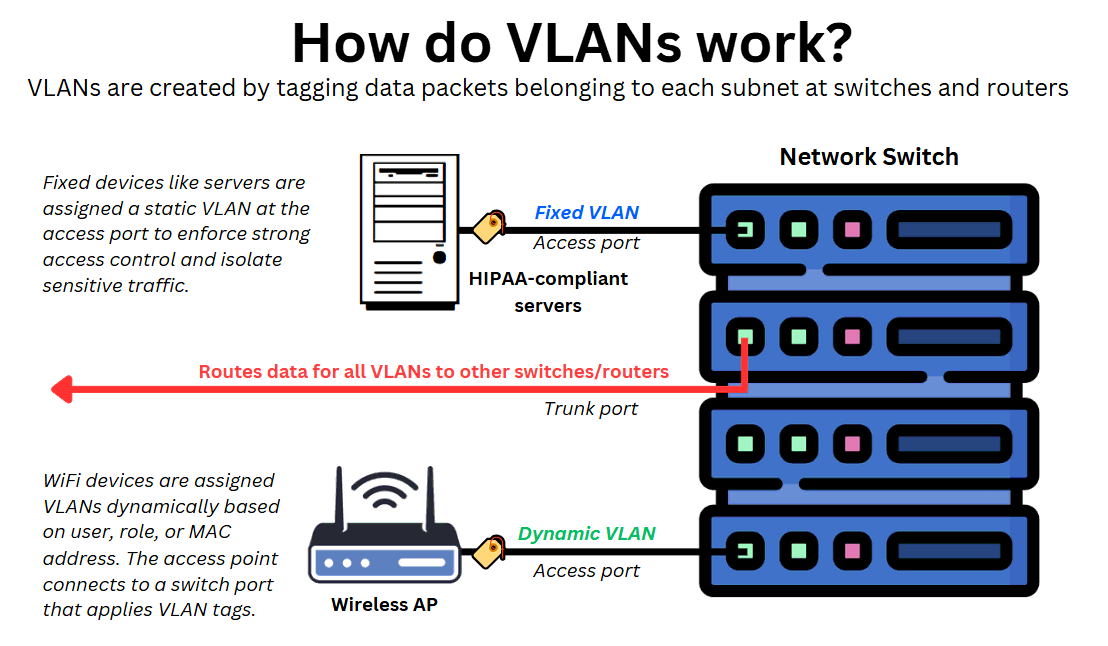
VLAN assignment criteria
VLANs are extremely versatile because the tagging protocol 802.1Q lets network admins recognise and differentiate LAN traffic based on a wide range of features, including:
Device identifier (MAC Address)
Static VLANs can be assigned based on a device’s unique MAC address. For example, a printer may always belong to the “Printer VLAN,” or a specific employee’s laptop may be assigned to the “Finance department VLAN.”
User login (802.1X Authentication)
Dynamic VLAN assignment based on user credentials. After authentication, users can be automatically placed into role-based VLANs like “HR department VLAN” or “Sales department VLAN.”
Access port
This is the same as the Fixed VLANs described earlier. VLANs can be assigned based on the physical port a device connects to. For instance, devices plugged into a certain port may be placed into a “Floor 2 VLAN” or “Server VLAN” by default.
Data type (e.g., SIP headers for VoIP)
Traffic can be tagged and routed based on its type. For example, SIP-based VoIP traffic can be directed to a “Voice VLAN” for prioritised handling, ensuring low latency and high VoIP call quality.
Remote connection (VPNs)
When users connect remotely via VPN, VLANs can be assigned based on user profiles, ensuring traffic follows the same policies as if they were on-site. The business broadband router reads the tag and applies the correct VLAN policy.
ZTNA (Zero Trust Network Access) assessment
In Zero Trust environments, VLAN assignment can reflect a device’s security posture. Devices or users that fail authentication checks (e.g. 2FA, certificates) may be redirected to lower-trust segments such as a “Guest VLAN.”
This is typical in businesses working with SASE or SD-WAN solutions for flexible wide area networking.
Legacy devices
Older or unmanaged devices that don’t support tagging (e.g. outdated printers or PCs) are typically placed into a default VLAN with minimal privileges for safety and compatibility.
Types of VLANs
VLANs segment network traffic into distinct subnets, improving both organisation and security.
While VLAN tagging is highly flexible (allowing traffic to be grouped by user, device, location, connection type, function, etc.), most networks rely on a few standard VLAN categories to keep things manageable.
These “types” of VLANs aren’t fundamentally different technologies, but rather common ways to organise and apply VLANs based on business needs. Organisations can create custom VLANs for any use case, but the following are the most widely used in business environments:
Data VLAN
The Data VLAN is one of the most commonly used categories. It segments network traffic based on business roles or departments (e.g. upper management, finance, HR, admins), ensuring that different types of data are isolated, organised, and routed efficiently.
It is called a “Data VLAN” because it typically carries general business traffic such as email, file transfers, web browsing, and internal systems access.
Voice VLAN
The Voice VLAN is dedicated to business VoIP phone system traffic. It prioritises voice packets to ensure high-quality, low-latency calls across the network.
Because voice traffic is highly time-sensitive, assigning it to a dedicated VLAN helps prevent jitter, delay, and packet loss, ensuring clear communication even in high-traffic environments.
Management VLAN
The Management VLAN is used exclusively for managing network devices such as switches, routers, firewalls, and wireless access points.
By Isolating access, it enhances security and ensures that only authorised personnel can configure and monitor network infrastructure, protecting core network operations from unauthorised interference.
Default VLAN
The Default VLAN (typically VLAN 1) is the fallback for devices not yet assigned to a specific VLAN.
It’s useful during initial setup or onboarding new devices, allowing them to communicate with the network until they can be categorised. By default, this VLAN carries minimal privileges to reduce risk while maintaining basic connectivity.
Private VLAN (PVLAN)
A Private VLAN (PVLAN) is an advanced type of subdividing a primary VLAN into multiple isolated secondary VLANs.
While devices in a PVLAN can share central resources (such as internet access), they remain isolated from one another.
This configuration is ideal for niche use cases like cloud hosting, virtual private servers (VPS), and managed service environments where resource sharing is needed without inter-device communication.
VLAN policies
Once VLANs are configured, network switches and routers apply policies to traffic based on its VLAN tags.
These policies control how traffic is handled, prioritised, and secured across local area networks. Common VLAN policies include:
Traffic segmentation
VLANs can isolate sensitive data (e.g. patient records in healthcare) by routing it through encrypted or restricted channels, separate from general traffic. This supports cybersecurity compliance with industry-specific regulations, such as HIPAA and FCA.
Quality of Service (QoS)
In Voice VLANs, QoS policies prioritise VoIP traffic to minimise delay, jitter, and packet loss. This ensures reliable, high-quality calls even during peak network usage, essential for organisations that depend on real-time communications.
Access Control Lists (ACLs)
ACLs can be applied per VLAN to control which users or devices can access specific resources strictly. For example, only users in the Finance Department VLAN may access financial systems, helping prevent unauthorised access to sensitive information.
Inter-VLAN routing
While VLANs are isolated by default, inter-VLAN routing allows controlled communication between them. For instance, devices in the Guest VLAN might have internet access, but be blocked from accessing internal business systems, protecting the core network.
Time based connections
VLAN policies can be scheduled to allow or restrict access during specific hours. For example, a Guest VLAN might only be active during business hours, reducing exposure and conserving bandwidth outside of operating times.
Access and trunk ports
VLAN configuration requires a deep understanding of how VLANs are handled by switch and router ports, specifically, the difference between “access” and “trunk” ports.
All network switches and routers have ports where Ethernet cables connect devices across the LAN. This is where you plug in your PCs, servers, VoIP phones, IoT devices, and mesh networks.
When configuring VLANs, it’s important to distinguish between the two port types:
- Access ports (Device-to-switch connections): Assign VLAN IDs to all incoming Ethernet frames (like data packets) from end devices.
- Trunk ports (Switch-to-switch connections): Carry traffic for multiple VLANs for inter-switch and inter-VLAN communication.
New VLANs must be manually assigned to access ports, whereas trunk ports automatically support all VLANs configured on the switch.
Key benefits of VLANs
Here are the core advantages of using VLANs in a business network:
Improved security
VLANs isolate sensitive data and control which devices can access specific resources, reducing the risk of unauthorised access.
This is especially important in sectors like finance and healthcare, where isolating financial records or patient data supports compliance with regulations such as GDPR or HIPAA.
Data breaches can often be contained to a single VLAN.
Better network performance
VLANs reduce congestion and limit broadcast traffic by segmenting and network load balancing the traffic, improving overall efficiency.
For example, giving each VLAN a different priority score means that business-critical traffic (e.g. hosting services, real-time communications, financial transactions) remains unaffected, even during congestion.
Simplified network management
VLANs make it easier to manage and scale your network. New departments or locations can be added without disrupting existing operations as your business grows or reorganises.
Enhanced flexibility
Devices can be grouped logically, regardless of their physical location. For example, employees in different cities can be placed in the same VLAN, allowing consistent access to shared resources and centralised IT control.
Cost effectiveness
VLANs reduce the need for separate physical infrastructure. A single switch can support multiple VLANs, helping small and growing businesses maximise their existing hardware investment.
Simplifies troubleshooting
Network segmentation makes diagnosing issues faster. If a problem arises in a specific VLAN (e.g. the marketing VLAN), IT can isolate and resolve it without affecting the rest of the network.
Setting up VLANs on a business network
Setting up a VLAN is a multi-step process that requires planning, configuration, and ongoing management to ensure the network remains secure, efficient, and scalable.
The good news is that all business-grade networking equipment supports VLAN protocols natively, so your IT team can handle the setup in-house, much like other LAN technologies.
Here’s an overview of how network administrators typically set up and manage VLANs:
1. Planning the VLAN structure
The first step is to define how the network should be segmented. Network admins and key business leaders assess business requirements, including security, traffic management, and performance, to design a logical VLAN layout.
For example, departments like Finance or HR normally require stricter access controls, while teams such as Marketing benefit from prioritised bandwidth for large file transfers, cloud apps and real-time comms.
2. VLAN configuration
Admins then implement the VLAN structure on managed switches, routers, and sometimes firewalls.
This is typically done via a command line interface (CLI), especially in enterprise environments using Cisco, Juniper, or similar hardware.
However, many modern switches offer graphical user interfaces (GUIs) accessible via web browsers, making basic VLAN configuration more approachable for non-specialist staff.
Popular devices with user-friendly interfaces include Cisco Meraki, Ubiquiti, and Netgear Pro switches.
In the GUI, admins can:
- Define VLANs by assigning IDs and names (e.g. VLAN 20 as “Guest VLAN”)
- Assign ports to specific VLANs (e.g. Port 01 to “High-Sec VLAN”)
- Configure dynamic VLAN tagging (based on device type, user authentication, etc.)
- Apply VLAN-specific rules (e.g. QoS, ACLs, trunk settings)
- Monitor VLAN status and connected devices
In larger networks, admins will also configure inter-VLAN routing using a Layer 3 switch or router, typically through trunk ports.
3. VLAN testing
VLANs are tested once the configuration is complete to ensure everything functions correctly. This includes verifying:
- Device VLAN membership
- Inter-VLAN communication (if applicable)
- Access controls and policy enforcement
- Network performance and traffic segmentation
4. VLAN maintenance and monitoring
Ongoing management involves reviewing and updating VLAN configurations, security settings, and compliance requirements.
As your network evolves (i.e. new departments, devices, or locations), VLANs can be added or modified to meet changing business needs across both local and wide area network.
VLAN business use cases
VLANs have become an essential tool for network administrators, effectively managing local area networks with precision and flexibility.
By virtually segmenting network traffic, VLANs allow businesses to secure, optimise, and organise data flows to suit their unique operational needs, offering practical solutions to a range of real-world challenges.
While VLANs can be applied in countless ways, here are three of the most common use cases in business environments:
1. Guest networks
Most organisations offer guest WiFi to provide internet access for visitors. A dedicated Guest VLAN ensures these users (e.g. contractors, clients, or personal devices) are isolated from the core network.
This protects sensitive data and prevents guest traffic from consuming bandwidth needed for business-critical operations.
2. Achieving cybersecurity compliance
UK businesses must comply with data protection laws such as the Data Protection Act and industry-specific standards like GDPR or HIPAA.
VLANs support compliance by enabling strict access controls, enforcing data segmentation, and ensuring sensitive traffic (e.g. financial or patient data) is encrypted and isolated from general traffic.
3. IoT device management
Modern offices often include a wide array of IoT devices, from smart thermostats and security cameras to digital signage.
These devices, while useful, can pose security risks if not properly isolated. VLANs allow administrators to segment IoT traffic from business systems, reducing risk and avoiding the need for additional physical infrastructure.
VLAN security vulnerabilities
VLANs are a fundamental part of network security, helping businesses segment traffic and enforce access policies.
However, like any network technology, they are not immune to threats, and if misconfigured or left unsecured, they can introduce vulnerabilities that attackers may exploit.
Here are some of the most common VLAN-related security risks:
Unauthorised access and VLAN hopping
Attackers may manipulate VLAN tags to “hop” between VLANs, bypassing isolation and gaining access to restricted resources. This can lead to unauthorised data access or system breaches.
Traffic manipulation and spoofing
Attackers can redirect or intercept traffic by spoofing device identities (e.g. switch MAC addresses or IPs) or altering VLAN tags, leading to data leaks, tampering, or privilege escalation.
Denial of service (DOS) and network overload
Malicious users can flood the network with traffic to overwhelm switches and disrupt communication between VLANs. This can degrade performance or knock critical services offline.
Misconfiguration and routing issues
Improper VLAN setup or weak inter-VLAN routing rules can result in unintended segment access.
This undermines isolation and can expose sensitive systems to broader access than intended.
Man-in-the-middle attacks
If VLAN traffic is not secured correctly, attackers may intercept and alter communications between devices, even across VLANs, potentially leading to data breaches or service disruption.
Preventing VLAN attacks
While these are real cybersecurity threats, most can be mitigated through best-practice security hygiene, including:
- Strong authentication: Use 802.1X and other identity controls to ensure only authorised users and devices access the network.
- Traffic encryption: Encrypt VLAN traffic using SSL/TLS or IPsec to prevent eavesdropping and tampering.
- Regular auditing: Review VLAN configurations, ACLs, and routing rules to detect early misconfigurations or vulnerabilities.
VLAN – FAQs
Our business networking experts answer common questions about VLANs for UK organisations:
What’s the difference between a LAN and a VLAN?
A LAN (Local Area Network) connects all devices within a local environment (e.g. an office or restaurant) through switches, routers, and other infrastructure.
A VLAN (Virtual Local Area Network) is a virtual segment within a LAN. It groups devices logically (by role, department, or function), even if they’re not physically connected to the same switch.
For example, within the same office LAN, you might have separate VLANs for HR, Finance, and Operations, each with access rules and traffic policies.
What’s the difference between a VLAN and a VPN?
A VLAN segments traffic within a local network, improving security and performance between internal groups.
A VPN (Virtual Private Network) provides a secure, encrypted tunnel for remote users to connect to the network over the internet. VLANs are used inside the office; VPNs connect users from outside the office.
What’s the difference between a VLAN and a subnet?
A VLAN is a way to segment traffic within a LAN at the switch level, while a subnet is the layer 3 (IP-based) segmentation of a network that supports it.
In many cases, each VLAN is assigned its own subnet, so while not identical, the two often go hand-in-hand.
You can think of a VLAN as the logical separation and the subnet as the addressing scheme that supports it.
What’s the difference between a VLAN and MPLS?
A VLAN is used within a local network to isolate traffic between users or devices. MPLS (Multi-Protocol Label Switching) is a fixed wide area networking technology that routes traffic efficiently between geographically distant locations (like multiple offices or data centres).
While both use tagging mechanisms, VLANs manage traffic locally, and MPLS manages traffic across large networks.

