ISO 27001 certification for businesses
ISO 27001 is the internationally recognised standard for information security management. Certification demonstrates an organisation’s commitment to robust data protection and cybersecurity practices.
Many businesses achieve ISO 27001 to meet regulatory and compliance requirements, obtain secure public sector and enterprise contracts, and support customer onboarding.
This guide outlines what ISO 27001 is, who needs it, and what the certification process involves.
Contents:
- How does ISO 27001 work?
- Which businesses need ISO 27001 certification?
- What has changed between ISO 27001:2013 and ISO 27001:2022?
- ISO 27001 certification requirements
What is ISO 27001?
ISO 27001 is the global standard and certification for managing information security. Organisations get certified to meet the contractual requirements of government bodies, enterprise clients, or when operating in highly regulated sectors, as the standard demonstrates strong data protection practices.
The standard focuses on establishing an Information Security Management System (ISMS): a structured set of policies, processes, controls, and organisational practices used to protect information.
Formally, the aim of ISO 27001 is to ensure the confidentiality, integrity, and availability (CIA) of an organisation’s information:
- Confidentiality: Only authorised people can access data
- Integrity: Data remains accurate and trustworthy
- Availability: Information is accessible when needed
In practice, protecting “information” means protecting the entire business. Systems, people, suppliers, and processes all play a role, as breaches, leaks, and disruptions ultimately compromise one or more elements of CIA.
ISO 27001 is vendor-neutral and applies to organisations of all sizes and industries. The current version of the standard, ISO 27001:2022, places greater emphasis on cloud services, evolving threat landscapes, and organisational resilience.
How does the ISO 27001 certification process work?
ISO 27001 is a certification standard, not just a set of guidelines. Organisations apply for certification, implement the required framework, and are then independently audited by an accredited certification body. If the organisation meets the standard’s requirements, it becomes ISO 27001 certified.
In practice, ISO 27001 requires a business to establish a formal, repeatable system for managing information security and to demonstrate, through a series of audits, that the system is operating effectively.
Below is a step-by-step overview of the certification process.
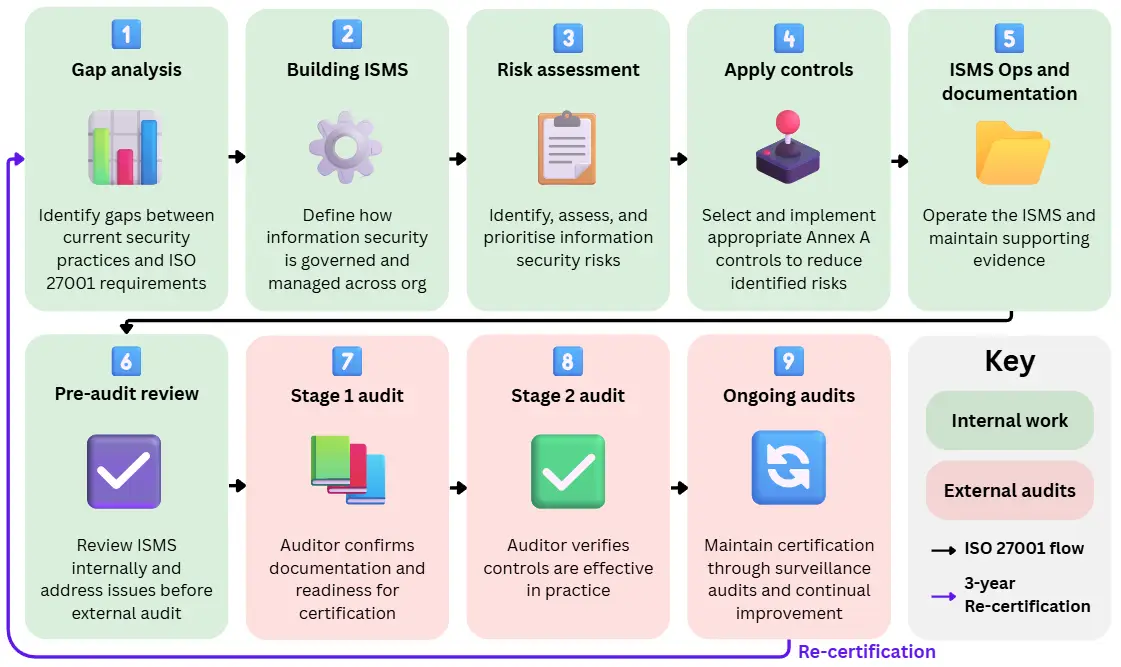
1. Gap analysis and preparation
Most organisations start by comparing their existing security practices against the requirements of ISO 27001. This gap analysis identifies what already exists, what needs improving, and what must be created before certification.
In reality, many businesses already have technical controls in place (such as Single-Sign On or encrypted devices) but governance is informal. For example, no written policies, no documented risk assessment, or inconsistent security processes.
2. Business builds an Information Security Management System (ISMS)
The ISMS is the foundation of ISO 27001. It is not a tool or product, but a framework for organising and managing information security day to day.
At a practical level, the ISMS defines:
- What information needs protecting (e.g. customer data, payment details, internal financial records)
- What risks the business faces (e.g. phishing attacks, unauthorised access, data loss)
- Who is responsible for security decisions (e.g. a director or senior manager, not just IT)
- What rules staff must follow (e.g. using managed devices, strong passwords, secure remote working)
These decisions are captured in policies and procedures that apply consistently across the organisation.
3. Risk identification and prioritisation
ISO 27001 uses a risk-based approach. The business identifies where information could realistically be compromised and assesses the likelihood and potential impact of each risk.
This ensures security efforts are focused on what matters most, rather than applying generic or unnecessary controls. High-priority risks might include:
- Phishing and credential compromise: High likelihood; results in unauthorised access to email, cloud systems, and sensitive data.
- Loss or theft of laptops and mobile devices: Medium likelihood; results in exposure of customer data or internal business information.
- Unauthorised access to cloud services: Medium likelihood; results in data breaches, service disruption, or regulatory consequences.
These risk assessments directly inform which security controls are selected and how rigorously they are applied.
4. Security control selection and implementation
Once risks are understood, the business selects security controls for each. These controls are chosen from Annex A (a catalogue of recommended security safeguards) of the standard. For example:
- Phishing and credential compromise: Applying MFA, cyber security awareness training, and email filtering.
- Lost or stolen devices: Implementing full-disk encryption, remote wipe, and asset tracking.
- Unauthorised access to cloud services: Implementing access logs and regular access reviews.
Each selected control must be implemented in practice and justified against the risks it is intended to mitigate.
5. System use and documentation
In addition to controls, ISO 27001 requires evidence that security is managed consistently in day-to-day operations. To pass certification and ongoing audits, organisations must maintain documented information such as:
- Written policies and procedures
- Records, including risk assessments and risk registers
- Evidence that operational controls are actually followed
Auditors will look for real-world application, not documentation created solely for compliance.
6. Pre-audit internal review
Before external certification, the organisation normally reviews its own ISMS through an internal audit and a management review to ensure issues are identified and addressed internally before an external audit:
- Internal audit: Checks whether policies, controls, and processes are being followed as intended.
- Management review: Assesses overall ISMS performance, risks, incidents, and improvement actions.
7. Audit of documentation and readiness
This is the first step of the external audit. The certification body reviews the ISMS scope, documentation, and overall readiness for certification.
At this stage, auditors confirm that required policies, risk assessments, and governance processes exist and are aligned with ISO 27001 requirements.
Any major gaps must be resolved before the organisation can proceed to the full certification audit.
8. Audit of operational effectiveness
The second stage of the audit is the main certification audit. Auditors assess whether the ISMS and selected security controls are operating effectively in practice.
This includes reviewing records, testing controls, and interviewing staff to confirm that security procedures are understood and followed. Common examples of nonconformities at this stage include:
- Policies are not being followed in practice, such as access controls that exist on paper but are not consistently applied.
- Incomplete or outdated risk assessments, where new systems or changes have not been reviewed.
- Lack of evidence, such as missing access logs, training records, or incident documentation.
If nonconformities are identified, corrective actions must be completed and verified by the certification body. Once all issues are satisfactorily closed, the organisation is formally awarded ISO 27001 certification.
9. Ongoing (post-certification) audits
ISO 27001 certification operates on a three-year cycle because it requires ongoing verification that the ISMS remains effective over time.
In addition to the initial certification, organisations must complete the following:
- Annual surveillance audits: Auditors review updates to risk assessments, evidence of staff training, incident-handling procedures, internal audit results, and the management of changes to systems or the business.
- Recertification every three years: Reassesses the ISMS against the full ISO 27001 standard to confirm continued conformity and effectiveness.
Surveillance audits are less intensive than the initial certification audit and focus on ensuring that the ISMS is maintained, updated, and improved as the business evolves. This ongoing oversight is what gives ISO 27001 its long-term credibility.
Which businesses need ISO 27001 certification?
ISO 27001 certification is always beneficial, as it requires businesses to operate within a robust and internationally recognised information security framework. However, it is rarely a strict legal or contractual requirement.
Whether a business needs ISO 27001 depends on its industry, the sensitivity of the data it handles, and the criticality of the services it provides.
Below are the most common scenarios in which ISO 27001 is used and how it is applied in practice.
Businesses operating in highly regulated sectors
Status: Expected
In highly regulated sectors such as finance, healthcare, and telecommunications, ISO 27001 is not explicitly mandated but is widely used as a recognised framework to demonstrate compliance with security and data protection obligations.
This commonly applies to:
- Financial services: Banks, fintech companies, payment providers, and investment firms
- Healthcare: Private clinics, digital health platforms, and care providers
- Telecommunications: Organisations operating critical national infrastructure
Businesses working with government or public-sector supply chains
Status: Expected (often required)
In the UK public-sector, tendering processes require suppliers to hold ISO 27001 certification. Without it, organisations may be excluded from tenders or face additional scrutiny.
This includes work with:
- Central government departments
- Local councils
- NHS procurement
- Defence and security supply chains
Technology and service providers selling to enterprise customers
Status: Expected
Enterprise customers normally expect ISO 27001 certification before onboarding suppliers that will access their systems or data, even if indirectly. In these cases, ISO 27001 becomes a commercial requirement rather than a purely security-driven decision.
This is particularly common for:
- SaaS companies
- Cloud hosting providers
- Managed service providers (MSPs)
- Business VoIP phone providers
Other businesses handling sensitive or high-value data
Status: Recommended
For businesses outside regulated, public-sector, or enterprise environments, ISO 27001 is often adopted where sensitive or commercially valuable data is central to operations.
It provides a structured way to manage data security, reduce risk, and demonstrate responsible handling of information, even where there is no external requirement to do so. It replaces informal or ad-hoc security practices with a consistent, auditable framework.
Examples include:
- Professional services firms managing confidential client information (e.g. legal, accountancy, consultancy)
- Marketing, data, and research agencies processing customer or campaign data
- E-commerce and subscription-based businesses storing customer and payment-related information
- Growing SMEs and start-ups whose products or platforms rely heavily on user or operational data
Businesses seeking cyber insurance or improved insurance terms
Status: Beneficial
ISO 27001 is not required to obtain cyber insurance in the UK, but is helpful for supporting broader coverage or more favourable terms. Insurers increasingly assess governance, risk management, and security controls during underwriting, and holding ISO 27001 clearly evidences:
- Formal risk management processes
- Defined security policies and responsibilities
- Ongoing monitoring and incident response capabilities
What has changed between ISO 27001:2013 and ISO 27001:2022?
ISO 27001:2022 is the next revision of the 2013 standard. Its purpose is not to change how information security is managed, but to modernise the standard to reflect current technologies, cloud adoption, and evolving cyber threats.
The core principles of ISO 27001 remain unchanged. Most updates focus on Annex A, where security controls have been reorganised, clarified, and updated.
Annex A changes in ISO 27001:2022
Annex A has been significantly restructured in the 2022 update. There is a new control structure, many existing controls have been consolidated or clarified, and a small number of new controls have been introduced to reflect modern business environments.
New control structure
The previous 14-domain structure was deemed too overcomplicated and has been replaced with four clearer control categories:
- Organisational controls: Governance, policies, supplier and incident management
- People controls: Security awareness, training, acceptable use
- Physical controls: Premises, equipment, and physical access protection
- Technological controls: Access control, encryption, logging, network security
Removed, consolidated and new controls
The total number of controls has been reduced from 114 to 93, primarily through consolidation and the removal of duplicates. At the same time, new controls have been introduced, and some existing controls expanded to address gaps or less explicit areas in the 2013 version.
Key additions include controls covering:
- Threat intelligence: Monitoring and using information about emerging cyber threats
- Cloud services security: Managing risks associated with cloud providers and shared responsibility models
- Data masking: Protecting sensitive data used for testing, analytics, or non-production purposes
- Monitoring activities: Clearer expectations around logging, network monitoring, and detection of security events
Changes to risk treatment and the Statement of Applicability
Alongside Annex A, ISO 27001:2022 places stronger emphasis on how risk treatment decisions are justified and documented. Organisations are expected to clearly explain:
- How risks were assessed and prioritised
- Why specific Annex A controls were selected or excluded
- How accepted risks align with business objectives and organisational context
As a result, the Statement of Applicability (SoA) has become increasingly important during audits.
Transitioning from ISO 27001:2013 to ISO 27001:2022
ISO introduced a formal transition period to allow organisations certified to ISO 27001:2013 to move to the updated 2022 version. This transition period lasted three years, aligning with the standard certification cycle.
During this time, organisations were expected to update their Information Security Management System (ISMS) to reflect the new requirements. This typically involved:
- Reviewing and updating documentation to align with ISO 27001:2022 terminology and structure
- Remapping existing security controls to the new Annex A categories
- Identifying and addressing any gaps introduced by new or expanded controls
- Updating the Statement of Applicability to reflect the revised control set
The transition was usually assessed during scheduled surveillance or recertification audits, rather than requiring a separate certification process.
The transition period has now ended, and all new certifications and recertifications are issued exclusively against ISO 27001:2022.
ISO 27001 certification requirements
Any organisation can pursue ISO 27001 certification, provided it meets the certification requirements defined in Clauses 4 to 10 of the standard.
These clauses specify the requirements for establishing, operating, and continually improving an Information Security Management System (ISMS). Certification bodies audit organisations directly against these clauses.
To achieve and maintain ISO 27001 certification, a business must demonstrate compliance with each requirement in practice. Below is a clear explanation of what these requirements mean for a typical business.
Clause 4: Context of the organisation
The business must understand its environment and clearly define the scope of its ISMS. In practice, this means:
- Identifying internal and external factors that affect information security
- Understanding the needs of customers, regulators, and other interested parties
- Defining exactly what parts of the business, systems, and data are covered
The scope must be documented and reflect how the business actually operates.
For example:
A 30-person consultancy defines its ISMS scope as covering staff, client data, laptops, cloud email, CRM, and document storage systems, while excluding unrelated personal devices.
Clause 5: Leadership
Information security must be actively supported and owned by management. Directors or senior managers are accountable for the ISMS, not just IT teams. This requires:
- Demonstrable commitment from senior leadership
- A documented information security policy
- Clear assignment of roles, responsibilities, and authority
For example:
A managing director formally approves the information security policy and assigns responsibility for the ISMS to the operations director, with regular management reviews scheduled.
Clause 6: Planning
This clause introduces ISO 27001’s risk-based approach. Businesses must:
- Identify information security risks
- Assess their likelihood and impact
- Decide how each risk will be treated (mitigated, accepted, transferred, or avoided)
- Define measurable information security objectives
These decisions must follow a consistent methodology and be documented.
For example:
A business identifies risks such as phishing attacks and lost laptops, assesses their impact, and decides to mitigate them through Multi-Factor Authentication, staff training, and device encryption.
Clause 7: Support
The ISMS must be properly supported across the organisation. This includes:
- Ensuring staff are competent and security-aware
- Communicating security responsibilities clearly
- Maintaining documented information such as policies, procedures, and records
Documentation must be controlled, current, and accessible to those who need it.
For example:
New starters complete security awareness training, staff formally acknowledge key policies annually, and ISMS documents are stored in a controlled shared folder.
Clause 8: Operation
This clause focuses on putting plans into action.
The business must:
- Implement its risk treatment plan
- Operate selected security controls consistently
- Manage changes that could impact information security
Auditors will look for evidence that controls are operating day to day, not just defined on paper.
For example:
Access to client systems is restricted by job role through conditional access and VLANs; laptops are encrypted by default; and changes to cloud systems are reviewed and approved before deployment.
Clause 9: Performance evaluation
The organisation must regularly review how well its ISMS is performing. This requires:
- Monitoring and measuring security performance
- Conducting internal ISMS audits
- Holding management reviews at planned intervals
These activities help identify issues before they become serious problems.
For example:
The business conducts an annual internal audit, reviews incidents and risks quarterly, and discusses ISMS performance during scheduled management meetings.
Clause 10: Improvement
ISO 27001 requires continual improvement of the ISMS.
Businesses must:
- Identify nonconformities and security incidents
- Take corrective action
- Update risks, controls, and processes as the business changes
For example:
Following a phishing-related email compromise, the business updates its training programme, improves email filtering, and records corrective actions within the ISMS.
Mandatory list of ISO 27001 documents
ISO 27001 does not define a fixed checklist of mandatory documents by name. However, the standard requires organisations to maintain specific documented information to demonstrate that their ISMS meets the requirements set out in Clauses 4 to 10.
In practice, a well-established set of documents is required to pass ISO 27001 certification audits. These documents (summarised in the table below) form the core evidence that certification bodies assess to confirm compliance:
| Document | Why it’s needed | Relevant ISO 27001 clause(s) |
|---|---|---|
| ISMS scope document | Defines what parts of the business, systems, and data are covered by the ISMS and what is excluded | Clause 4 |
| Information security policy | Sets the organisation’s security objectives and demonstrates leadership commitment | Clause 5 |
| Risk assessment methodology | Ensures risks are identified and assessed consistently and in a repeatable way | Clause 6 |
| Risk assessment results (risk register) | Provides evidence that information security risks have been identified and evaluated | Clause 6 |
| Risk treatment plan | Documents how identified risks will be treated and which controls will be applied | Clause 6 |
| Statement of Applicability (SoA) | Explains which Annex A controls are applied or excluded and why | Clause 6, Annex A |
| Information security objectives | Defines measurable security goals aligned with business objectives | Clause 6 |
| Competence and awareness records | Shows staff are trained, aware, and competent in information security responsibilities | Clause 7 |
| Documented policies and procedures | Provides operational guidance on how security is managed day to day | Clauses 5, 7 |
| Operational control records | Demonstrates that security controls are implemented and operating in practice | Clause 8 |
| Internal audit programme and reports | Confirms the ISMS is reviewed internally and issues are identified | Clause 9 |
| Management review records | Shows senior management review ISMS performance and make decisions | Clause 9 |
| Corrective action records | Demonstrates how incidents, audit findings, and nonconformities are addressed | Clause 10 |
How much does ISO 27001 certification cost for businesses?
ISO 27001 certification represents a significant investment, particularly for small and medium-sized businesses. Costs are not fixed and vary widely depending on the size, complexity, and maturity of an organisation’s existing security practices.
As a general guide, even a small, single-site business with a limited number of employees should expect a minimum total cost of around £10,000 over a three-year certification cycle. Larger or more complex organisations, particularly those with multiple sites or extensive systems, can expect costs to exceed £60,000+ over the same period.
ISO 27001 certification costs are typically split into two main components:
- The cost of upgrading and operating security
- Certification body audit fees
Cost of upgrading security (internal effort and external support)
Most of the work required for ISO 27001 certification takes place within the organisation. Businesses must document how security is managed, assess risks, implement appropriate controls, and ensure those controls operate consistently.
Many organisations also engage external consultants to guide them through the process, particularly during initial implementation.
Typical internal and external effort includes:
- Gap analysis and planning
- Risk assessment and risk treatment planning
- Writing policies, procedures, and audit evidence
- Implementing or improving security controls across systems
- Staff training (cyber awareness and role-specific training)
- Implementing tools and technology (e.g., Next-Generation Firewalls, VPNs, SASE that will enhance security in key areas)
Cost estimates
For many SMEs, this may equate to:
- £5,000–£30,000+ in internal time and effort (depending on scope and complexity)
- £2,000–£40,000+ in external consultancy support, depending on the level of involvement
Some organisations rely mostly on internal resources, while others outsource large parts of the implementation.
Certification body audit fees
Certification body fees are the formal cost of ISO 27001 certification, paid to an accredited certification body (usually UKAS-accredited in the UK). The fees vary based on company size, scope, number of locations, and whether the audit is carried out on-site or remotely.
Cost estimates
Each stage of the certification cycle has its own cost:
- Stage 1 readiness review (one-time): £1,000 – £3,000
- Stage 2 certification audit (one-time): £3,000 – £10,000
- Surveillance audits (annual): £1,500 – £5,000 each
- Recertification audit (every 3 years): £3,000 – £10,000
The total spend over a 3-year cycle typically falls between £8,000 and £25,000+, though this varies with scope and auditor rates.
How does ISO 27001 help with GDPR compliance?
ISO 27001 and GDPR are closely aligned, but they are not the same thing:
- GDPR: A legal regulation that applies to organisations processing personal data (i.e., the majority of UK businesses)
- ISO 27001: A security standard that helps organisations protect information, including personal data, in a structured and auditable way.
ISO 27001 does not make an organisation GDPR compliant on its own. However, it provides a strong security and governance framework that supports many of GDPR’s core security and accountability requirements. For this reason, many organisations use ISO 27001 as the foundation of their cybersecurity compliance programme.
The table below shows how key ISO 27001 components align with GDPR expectations.
| ISO 27001 component (Clause) | How it supports GDPR compliance |
|---|---|
| Risk-based approach | Supports GDPR’s requirement to assess risks to personal data and apply proportionate safeguards |
| Information Security Management System (ISMS) | Provides a formal governance structure for managing personal data securely |
| Annex A security controls | Helps implement appropriate technical and organisational measures (GDPR Article 32) |
| Access control and authentication | Limits access to personal data to authorised users only |
| Encryption and data protection controls | Reduces the impact of data breaches and unauthorised disclosure |
| Incident management processes | Supports detection, investigation, and response to personal data breaches |
| Supplier and third-party controls | Helps manage processor and supplier security obligations |
| Monitoring, logging, and review | Supports accountability and ongoing oversight of security measures |
| Internal audits and management review | Helps demonstrate governance and continuous improvement |
| Independent certification | Provides third-party evidence of security maturity and due diligence |
What ISO 27001 does not cover
ISO 27001 does not address GDPR’s legal and privacy-specific requirements, namely:
- Lawful bases for processing personal data
- Privacy notices and transparency obligations
- Consent management
- Data subject rights (access, erasure, portability, etc.)
- Appointment or role of a Data Protection Officer (DPO)
- GDPR-specific impact assessments (DPIAs)
To meet these requirements, businesses must implement separate legal, privacy, and data-governance processes alongside ISO 27001.
How does ISO 27001 apply to broadband and networks?
ISO 27001 does not mandate specific broadband or networking technologies. Organisations are free to choose the solutions they use, provided they effectively protect information and support confidentiality, integrity, and availability (CIA).
Auditors will assess whether broadband and wide area networking arrangements are secure, resilient, and appropriate to the risks, as poorly managed connectivity can directly undermine an organisation’s ISMS.
Below are common networking technologies and how they typically support ISO 27001 requirements in practice:
Firewalls
ISO 27001 controls addressed: A.8.20 Network security, A.5.15 Access control, A.8.23 Web filtering (where applicable)
Firewalls help prevent unauthorised access to networks and systems by controlling inbound and outbound traffic. They are commonly used to enforce network security boundaries, restrict access based on defined rules, and reduce exposure to external threats.
LAN hardware
ISO 27001 controls commonly addressed: A.8.20 Network security, A.5.16 Identity management, A.5.17 Authentication information A.8.9 Configuration management
Routers, network switches, and WLAN access points provide the foundation for internal network connectivity. Auditors will typically expect these devices to be securely configured, access-restricted, regularly updated, and protected against unauthorised changes or misuse, as weaknesses at this layer can directly impact confidentiality and availability.
VLANs and network segmentation
ISO 27001 controls commonly addressed: A.8.20 Network security, A.5.15 Access control, A.8.22 Segregation of networks
VLANs support network segmentation in local area networks by separating systems, users, or environments based on switch port, role or risk. This helps limit lateral movement, reduce the impact of security incidents, and restrict access to sensitive systems in line with the principle of least privilege.
Broadband connections
ISO 27001 controls commonly addressed: A.8.16 Monitoring activities, A.8.20 Network security, A.8.14 Redundancy of information processing facilities
Broadband connections enable external connectivity and access to cloud services. Auditors will consider whether these connections are appropriate for the organisation’s risk profile, particularly where interception, outages, or service instability could affect confidentiality or availability. These are some characteristics they will look at:
- Broadband contention: Higher contention increases the risk of congestion and outages, which can affect the availability of security systems and services.
- Broadband redundancy and failover: Lack of alternative connectivity can create single points of failure, impacting business continuity and availability controls.
- Broadband security: Exposure to interception or unauthorised access can affect confidentiality, particularly if traffic is not adequately protected.
- Network monitoring: Limited ability to monitor performance or detect anomalies can weaken incident detection and response capabilities.
If your organisation wants to improve internet connectivity for its sites, use our business broadband comparison service to get the best prices.
SD-WAN and SASE
ISO 27001 controls commonly addressed: A.8.20 Network security, A.8.14 Redundancy of information processing facilities, A.8.16 Monitoring activities, A.5.15 Access control
SD-WAN solutions (Software-Defined WAN) and SASE (Secure Access Service Edge) solutions are used to centrally manage connectivity, security policies, and access controls across multiple sites and users. These technologies can support consistent security enforcement, improved monitoring, and increased resilience, particularly in distributed, hybrid, or cloud-first environments.
ISO 27001 – FAQs
Our business cybersecurity experts answer frequently asked questions (FAQs) regarding ISO 27001 certification:
How long does it usually take to implement ISO 27001?
Implementing ISO 27001 typically takes between 6 and 18 months from project start to certification. The exact timeline depends on the organisation’s size, system(s) complexity, the scope of the ISMS, and how mature existing security practices already are. Businesses with strong controls in place or a clearly defined scope can often move faster, while larger or less mature organisations may require more time.
Do we need specific tools or systems to comply with ISO 27001?
No, ISO 27001 is technology-neutral and does not mandate any specific tools, software, or vendors. Compliance is based on having appropriate processes, controls, and governance in place.
However, many organisations use tools for areas such as asset management, access control, logging, ticketing, or document management to make compliance easier and more scalable. The standard places equal importance on people, processes, and technology.
What is the difference between ISO 27001 and ISO 27002?
ISO 27001 is the certifiable standard that defines the requirements for an Information Security Management System (ISMS).
ISO 27002 is a guidance standard that provides detailed best-practice advice on how to implement and operate the security controls referenced in Annex A of ISO 27001.
Organisations certify against ISO 27001, while ISO 27002 is commonly used as a practical reference when designing or improving controls.
What happens if we fail an ISO 27001 audit?
If issues are identified during an audit, the auditor will raise nonconformities. Minor nonconformities usually require corrective actions to be completed within an agreed timeframe and do not necessarily prevent certification.
Major nonconformities must be resolved before certification can be granted, and evidence of effective corrective action is required. Failing an audit does not mean starting again; it means addressing gaps and demonstrating improvement.
How often do we need to update our ISMS once certified?
ISO 27001 requires the ISMS to be continually maintained and improved, not treated as a one-off exercise. Risk assessments, policies, and controls should be reviewed regularly and updated whenever there are significant business, technical, or regulatory changes.
Ongoing maintenance is formally checked through annual surveillance audits, with full recertification every three years.
Can we limit the scope of ISO 27001 to specific systems or locations?
Yes. Organisations are allowed to define a limited or phased scope, focusing on specific services, systems, business units, or locations. This is common for initial certification and can reduce complexity and cost. However, the scope must be clearly documented, justified, and realistic, and any exclusions must not undermine the effectiveness or credibility of the ISMS.