How does a Wireless LAN (WLANs) work for businesses
A Wireless LAN (WLAN) or WiFi network is the wireless portion of a business local area network. It lets WiFi devices connect to each other, local services, and the wider internet without needing a wired connection.
This article explains how they work, the different types, security, and how to implement them appropriately.
Contents
- What is a Wireless LAN?
- How does a Wireless LAN work?
- Types of Wireless LAN
- How to set up a business Wireless LAN
What is a Wireless LAN?
A Wireless LAN (WLAN) is the wireless access layer of a local area network (LAN) that extends network connectivity via radio signals rather than Ethernet cables.
Devices need to support WiFi technology to connect to the WLAN. Once connected, they can access any local and external resources in the same way as a wired device, such as a PC, within the LAN.
For example, a tablet connected to the WLAN can connect to:
- Other wireless devices (e.g., request a wireless lighting system to turn ON/OFF)
- Wired resources within the LAN (e.g., access a file from a local server, or send a document to the printer)
- Business cloud services (e.g. make a call through the cloud-based business VoIP phone system)
- Access public internet services (e.g., Access Google Search or ChatGPT)
While the local networks of homes and small businesses can be entirely WLAN for convenience, in most cases, the WLAN works in parallel to a more stable wired Ethernet LAN, extending coverage across a larger area and enabling wireless devices to connect within the business site.
WLANs can range from a single router supporting a small office or a university campus WLAN supporting thousands of wireless devices with high security, load balancing, and multi-path resilience.
WiFi technology, which transmits data using radio waves over short distances, forms the foundation of WLANs. It’s based on the IEEE 802.11 standards, which define how wireless devices communicate reliably and securely within a local network.
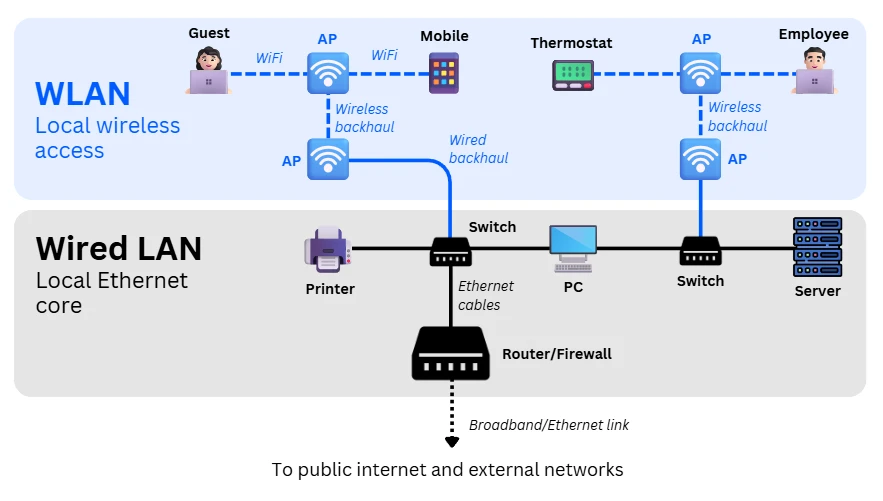
How does a Wireless LAN work?
A Wireless LAN connects wireless devices to local and external network resources using radio communication, coordinated by wireless access points (APs).
Data reaching and leaving devices is transmitted via antenna, travels wirelessly through WiFi, is converted to wired Ethernet at the access points, and usually travels across a wired LAN onto the router/firewall, where it is either routed back to another local resource or onto an external service.
Here’s the process in detail, using a WiFi device sending data out as an example:
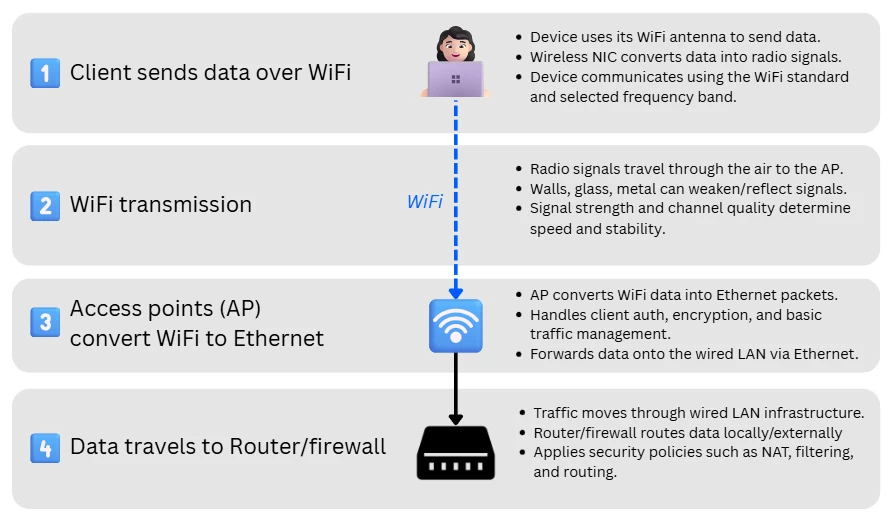
1. Client device sends data over WiFi
A wireless device like a laptop or smartphone sends data through its built-in WiFi antenna, using the WiFi standard (e.g. WiFi 4 or 6) and the frequency band requested by the WiFi network it connects to. The conversion into radio signals is done by the device’s wireless network interface card (NIC).
2. Wireless transmission
These radio signals travel through the air along their designated route to their designated access point. This could be the nearest AP or a series of hops in a mesh network with a wireless backbone.
The radio signal strength, channel quality, and signal-to-noise ratio (SNR) all affect how efficiently data moves. Obstacles such as walls, glass, and metal objects can absorb or reflect signals, reducing range and throughput. WLANs use various technologies to minimise this.
In enterprise networks with fast handoffs (roaming) and mesh networks, devices can dynamically change access points based on the signal quality or load balancing implemented by the WiFi network, and dynamically adjust power levels and channels to maintain stable, interference-free coverage, or as they change location, without losing connectivity.
3. Wireless Access Points (AP) convert data to local Ethernet traffic
The AP receives the WiFi packets (known as radio frames) and demodulates them into standard Ethernet traffic, ready for travel across the wired LAN, forwarding traffic to network switches or routers, depending on the assigned route.
Modern APs perform various performance and security functions: they manage client associations and access, encryption (like WPA3), Quality of Service (QoS) for prioritising VoIP or video traffic, and band steering to move clients between 2.4 GHz and 5/6 GHz bands for better performance.
In enterprise environments, APs are often centrally managed by a Wireless LAN Controller (WLC), which handles configurations, firmware updates, channel allocation, and real-time load balancing across hundreds of APs.
4. Traffic travels through wired LAN ethernet onto the router and firewall
Data continues travelling through the wired LAN, usually passing through network switches and local firewalls before reaching the business broadband router or gateway.
The router examines each packet to determine if it’s destined for another local device or for the internet. If it’s external, the router performs Network Address Translation (NAT) and sends it through its broadband or Business Ethernet WAN (wide area network) if sending to another site.
Return traffic follows the reverse route: From the internet, through the router and switches, back to the correct access point, and finally to the wireless client.
Throughout this process, network policies such as firewall rules, traffic shaping, and VLAN segmentation can apply to both wired and wireless traffic, maintaining unified security and performance.
Types of business Wireless LAN
Businesses use different types of Wireless LANs depending on their size, needs, and environment.
WLANs can also be categorised by factors like WiFi standard, backhaul design, or management method, but the most practical way to understand them is by the scale of deployment.
Small office/home office (SOHO) WLAN
Most suitable for: Home offices, remote workers, and very small businesses with fewer than 10 users.
A SOHO WLAN provides simple, reliable wireless access for small spaces, typically using a single WiFi router or a small number of consumer-grade access points to make a mesh network.
Management is usually local, through a web interface or mobile app, with no central controller or cloud system.
SOHO systems typically use WiFi 5 (802.11ac) or WiFi 6 (802.11ax) standards, offering multi-gigabit speeds and strong WPA3-Personal encryption.
They generally lack enterprise features like fast roaming (802.11r/k/v) or VLAN segmentation, instead relying on basic SSID separation (e.g., “guest” vs. “main” networks).
While easy to install and maintain, SOHO WLANs depend on consumer-grade equipment with limited analytics and minimal redundancy, making them suitable for low-density, low-risk environments such as small offices, retail kiosks, or remote setups.
Small and medium enterprise (SME) WLAN
Most suitable for: Cafes, retail stores, small offices, and distributed branch locations supporting 10–100 users.
An SME WLAN bridges the gap between consumer and enterprise wireless networks, providing professional-grade reliability and security without the complexity of large-scale deployments.
They typically use cloud-managed systems or controllerless access points, allowing central configuration, monitoring, and firmware updates through a unified dashboard.
These systems often use WiFi 6 or WiFi 6E for improved range, efficiency, and multi-user performance, with up to a dozen access points using wired backhaul for stability and power (via Power-over-Ethernet) and wireless mesh links to extend coverage between floors or buildings.
Many support fast-roaming standards (802.11r/k/v) for smoother mobility, VLANs for separating guest and staff traffic, and WPA3-Enterprise for stronger authentication.
Some vendors, such as Ubiquiti, TP-Link Omada, and Aruba Instant On, design solutions specifically for this tier, offering a balance of affordability, security, and scalability.
Enterprise WLAN
Most suitable for: Corporate campuses, manufacturing sites, hospitals, universities, and other large organisations with hundreds or thousands of users.
An enterprise WLAN is built for scale, reliability, and control, connecting large numbers of access points through centralised or hybrid management, often a combination of on-premises controllers and cloud platforms.
These networks rely primarily on wired backhaul (PoE) for high throughput, with wireless mesh links extending coverage in hard-to-cable areas. They typically use Wi-Fi 6E or the latest WiFi 7 to support fast roaming, load balancing, and advanced AI-assisted optimisation.
Security and access are enforced through enterprise-specific IEEE standards such as WPA3-Enterprise, 802.1X, and RADIUS, often integrated with enterprise products such as Microsoft and Palo Alto.
VLAN segmentation and policy-based access ensure strong isolation between users, guests, and IoT devices. Vendors such as Cisco Meraki, Aruba, and Ruckus provide enterprise-grade solutions offering automation, analytics, and redundancy for always-on wireless connectivity.
Other WLAN types
Here are other common ways in which WLANs are categorised in the industry, each focusing on a different technical layer:
By the IEEE architecture
Describes how WiFi devices and access points (APs) communicate, which is useful for IT teams and planners to understand the underlying structure of a WLAN.
- Infrastructure WLAN: Standard business WLAN where devices connect through APs; best for stable, centrally managed networks.
- Ad Hoc WLAN: Direct device-to-device WiFi; useful for temporary, small, or isolated peer connections without infrastructure.
- Mesh WLAN: APs link wirelessly to each other; ideal for extending coverage where cabling is difficult or impossible.
- WDS WLAN: Bridges APs to extend the same WLAN; useful for stretching existing networks across larger or awkward spaces.
By the management model
Describes how teams manage access points (APs). It’s most useful for IT managers and administrators choosing how to maintain and monitor the WLAN.
- Controller-based WLAN: On-premises controller manages all APs; best for large, centralised environments needing tight control and low-latency decisions.
- Cloud-managed WLAN: APs managed via online dashboards; ideal for distributed sites, remote IT teams, and simplified updates.
- Hybrid WLAN: Combines local control with cloud analytics; suited for organisations needing on-site reliability with cloud-level insight.
By backhaul type
Describes how APs connect back to the wired LAN, which is useful for network engineers and installers planning wiring, placement, and performance.
- Wired WLAN: Ethernet/PoE links to each AP; provides maximum stability, throughput, and predictable performance.
- Wireless WLAN: AP-to-AP radio links; useful in heritage buildings, temporary setups, or areas where cabling cannot be run.
- Mixed WLAN: Combination of wired and wireless backhaul; ideal for most sites as most have both accessible and hard-to-reach areas.
By topology
Shows how the WLAN is structurally arranged, useful for designers and implementers shaping coverage across buildings or campuses.
- Mesh WLAN: Self-healing, multi-path AP network; great for flexible coverage and resilience without full wiring.
- Star WLAN: Traditional layout where each client connects to its nearest AP; best for straightforward indoor deployments.
- Point-to-Point / Multipoint: Long-range links between buildings or sites; suited for campuses, warehouses, and outdoor environments.
By a security framework
Defines authentication and protection models, useful for security teams and compliance owners ensuring safe access and segmentation.
- WPA2/WPA3 encryption: Protects wireless data; essential for safeguarding traffic from interception or tampering.
- 802.1X + RADIUS: Provides identity-based access control; ideal for enterprise environments with staff devices and certificates.
- VLAN / NAC Segmentation: Separates users, guests, and IoT devices; critical for limiting lateral movement and enforcing zero trust.
Features of Wireless LAN
Business WLANs incorporate a wide range of features to provide wireless connectivity effectively, securely and conveniently. Below are the core features that make business-grade WLANs effective:
Wireless connectivity
WLAN provides high-speed wireless access to local devices using radio frequencies, typically 2.4 GHz, 5 GHz, or 6 GHz. These high radio frequencies allow for high speed connectivity within a local area.
Mobility and roaming
Modern business-grade WLANs have roaming capabilities, meaning that devices can reconnect to different access points to maintain connectivity as they move, essential for uninterrupted video and voice calls on a mobile device, warehouse scanners, and moving IoT systems.
Scalability
WLAN technology is highly scalable because it is based on international WiFi standards that are suitable for both homes and big organisations.
A WLAN can be as simple as a single access point directly at the router, or be made of hundreds of access points which support scalable add-ons like mesh networking (intelligent routing and wireless backhaul), load balancing, roaming and high frequency bands.
Centralised management and monitoring
Modern WLANs support management via a dashboard, whether that is an app running locally, an on-prem controller or a multi-site cloud dashboard. Network administrators can do things like monitor usage, track devices, adjust radio parameters, and push configuration updates in real time.
Quality of Service (QoS)
WLANs support traffic prioritisation to guarantee performance for critical applications such as internet-based voice and video. Through QoS policies, bandwidth can be reserved for specific traffic types, users, or devices, reducing latency and ensuring predictable service even during congestion.
Self-healing and adaptive performance
Enterprise and mesh WLANs include self-healing capabilities that automatically reroute traffic or adjust radio settings when interference or hardware failure occurs.
Adaptive features such as dynamic power control, band steering, and auto-channel selection keep performance stable as conditions change.
Guest access and captive portals
WiFi technology has built-in guest access features, such as captive portals, temporary credentials, and bandwidth controls to ensure the network can be segmented and controlled. These are common in hospitality, education, and retail environments.
Power over Ethernet (PoE)
Wired backhaul access points in business WLANs typically receive both data and power through a single Ethernet cable using PoE. This simplifies installation, enables remote power cycling, and supports deployment in areas without nearby electrical outlets.
Integration with local area network
WLAN technology is designed to extend business-wide policies wirelessly, supporting VLAN tagging, DHCP, DNS, Active Directory, and NAC systems. Users on WiFi can receive the same policies, logging, and access control as wired users, or even users in other sites.
Analytics and reporting
WLAN management platforms provide detailed usage analytics, tracking device types, application traffic, and performance trends. These insights help businesses optimise coverage, enforce policies, and plan capacity expansions intelligently.
Differences between Wireless LAN and wired LAN
Wireless LANs (WLANs) and wired LANs both provide local network connectivity, and in practice, they operate together, not separately.
A wired LAN typically forms the local, high-performance backbone, while the WLAN extends that network to users and devices that need mobility or cannot be cabled.
Here are the key differences:
| Feature | Wired LAN | Wireless LAN (WLAN) |
|---|---|---|
| Medium | Local data is carried over copper Ethernet cabling or fibre-optic links | Local data is carried over radio-frequency (RF) signals using Wi-Fi |
| Layer | Forms the core and distribution layers of the local network | Operates at the access layer, extending the wired LAN to wireless devices |
| Range | Limited by cable length (typically up to 100 m for copper Ethernet; fibre can run much further) | Indoors: typically 10–50+ m depending on walls and interference; Outdoors: can exceed 100–200+ m with clear line of sight |
| Mobility | None; devices require a physical connection | High; devices can move freely within wireless coverage areas |
| Performance | Very high, consistent performance. Bandwidth: 1–10 Gbps (modern standards up to 25/40/100 Gbps for specialist links). Latency: <1 ms. | Performance varies with distance, interference, and client load. Bandwidth (Wi-Fi 6/6E/7): 0.1 - 10 Gbps under ideal conditions. Latency: 5–20 ms, but can be lower with a good signal. |
| Reliability & stability | Extremely stable; unaffected by Radio-Frequency (RF) interference conditions; predictable performance | Affected by RF interference, congestion, obstacles, and environmental changes; performance is less predictable |
| Devices supported | One device per port, but switches can aggregate dozens to hundreds of ports; an entire wired network can scale to many thousands of devices | Many devices per access point (typically 20–100+, depending on design), but total WLAN capacity is constrained by shared spectrum and airtime |
| Security | Physical cabling limits unauthorised access; supports strong network security (802.1X, VLAN segmentation, MAC controls, ACLs, etc.) | Requires robust wireless security due to open medium: WPA3, 802.1X/EAP, segmentation, isolation, RF monitoring, intrusion detection, access controls and proper access-point placement |
| Installation complexity | Requires cabling, placement, and structured planning; more labour-intensive to extend or modify | Easier and faster to deploy; adjustments are usually made through AP placement, configuration, and controller management |
| Standards | IEEE 802.3 (Ethernet) | IEEE 802.11 (Wi-Fi) |
Wireless LAN standards and protocols
WLANs operate on a shared global framework defined by the Institute of Electrical and Electronics Engineers (IEEE) and supported by the WiFi Alliance, which certifies product interoperability and security.
The IEEE 802.11 family defines how WiFi transmits data, manages devices, and uses radio spectrum, while the WiFi Alliance and other standards bodies define how networks stay secure and interoperable.
Together, these frameworks make it possible for WiFi devices and infrastructure from different manufacturers to work together reliably and safely around the world.
Here are the main two groups:
1. IEEE standards (WiFi generations)
Each IEEE WiFi generation improves performance through new radio technologies, broader channels, and better spectral efficiency. These are the main versions of WiFi still in use across business networks today.
| WiFi Generation | IEEE Standard (Year) | Key characteristics | Typical Use |
|---|---|---|---|
| WiFi 4 | 802.11n (2009) | Introduced MIMO antennas and channel bonding (40 MHz), enabling speeds up to 600 Mbps and stronger indoor coverage. | Legacy business networks and small offices. |
| WiFi 5 | 802.11ac (2013) | Added MU-MIMO and beamforming, improving connection stability and throughput up to 3.5 Gbps. | Still widely used in offices, retail, and hospitality. |
| WiFi 6 / 6E | 802.11ax (2019 / 2021) | Improved efficiency and capacity, supporting more devices simultaneously with up to 9.6 Gbps throughput and lower latency. | The current standard for modern business WLANs. |
| WiFi 7 | 802.11be (2024) | Introduces multi-link operation and 320 MHz channels, enabling speeds up to 30 Gbps and ultra-low latency for real-time apps. | Emerging in next-generation enterprise and high-density networks. |
Aside from WiFi generations, several IEEE amendments add improvements to roaming, quality, security, and device experience. The most relevant are:
- 802.11r/k/v (2008–2011): Enables seamless roaming between access points without dropping connections.
- 802.11e (2005): Adds Quality of Service (QoS) to prioritise voice, video, and critical traffic.
- 802.11w (2009): Protects WiFi management frames against spoofing and disconnection attacks.
- 802.11s (2011): Enables wireless mesh networking between access points to extend coverage.
- 802.11h/d (2003–2004): Ensures WiFi meets regional spectrum and power regulations (e.g., Ofcom, EU).
- 802.11u / Hotspot 2.0 (2011): Allows secure, automatic connection to guest and public WiFi networks.
- 802.11ah / WiFi HaLow (2016): Provides long-range, low-power WiFi for IoT and industrial environments.
- 802.11ad/ay / WiGig (2012–2021): Delivers ultra-fast, short-range links for high-bandwidth apps like AR/VR.
2. Security standards and protocols
Security standards are defined primarily by the WiFi Alliance, building on IEEE foundations to ensure confidentiality, authentication, and integrity in WLAN communications.
They determine how users and devices prove their identity, how traffic is encrypted, and how networks enforce access policies.
| Standard / Protocol | Purpose | Key Features and Use |
|---|---|---|
| WPA3 (2018) | Encrypts traffic and provides stronger WiFi protection, making password-guessing attacks harder. | • Uses SAE for secure password exchange. • Offers forward secrecy to protect past data. • Standard on new Wi-Fi 6/6E/7 devices and modern enterprise access points. • Has widely replaced WPA2 (2004) except for home and legacy business networks. |
| RADIUS (Remote Authentication Dial-In User Service) | Central system that checks logins (passwords, certificates, device info) and grants or denies network access. | • Validates credentials coming from 802.1X. • Enforces access rules based on user/device identity. • For corporate/enterprise WiFi, less so for small businesses. |
| 802.1X Authentication (2001) | Verifies each user or device before allowing them onto enterprise WiFi. | • Works with a RADIUS server to check identity. • Supports certificate-based and password logins. • For corporate/enterprise WiFi, less so for small businesses. |
| EAP (Extensible Authentication Protocol) | Provides secure login methods for users connecting to enterprise WiFi. | • Runs within 802.1X for secure authentication. • Includes methods like EAP-TLS (certificates) and PEAP (username/password). • For corporate/enterprise WiFi, less so for small businesses. |
| SSID and MAC Controls | Identifies each Wi-Fi network (SSID) and can allow/block specific devices (MAC filtering). | • SSID = the Wi-Fi network name users see. • MAC filtering can allow/deny devices but offers weak security by itself. • Used in home routers and enterprise access points for guest networks, IoT segregation, or VLAN assignment. |
Wireless LAN security for businesses
Modern business WLANs are extremely secure. With today’s encryption and authentication standards, a properly configured WLAN is virtually unhackable without authorised credentials or insider access.
The problem isn’t the technology, it’s the inconsistency in setup and management. Many organisations still rely on outdated configurations, shared passwords, or unmonitored guest WiFi networks.
Common WLAN security threats
Here are the most prevalent security threats against WLANs:
Rogue access points
A rogue access point is an unauthorised WiFi device plugged into the internal LAN, usually added by staff or a contractor without security oversight. It’s rarely a deliberate attack, but more often an act of convenience or negligence. For example, someone setting up a small router or repeater for a demo, IoT testing, or to improve coverage in a dead zone.
In older or unmanaged networks, these devices can easily go unnoticed and extend the LAN outside the firewall, leaving a backdoor. Modern environments protected by 802.1X authentication or Network Access Control (NAC) make rogue APs much harder to install, but the risk remains if ports or switches are left unmonitored.
Evil twins
An evil twin is a malicious external clone of one of your WiFi networks. Attackers broadcast the same SSID (and sometimes spoof the MAC/BSSID) as a legitimate access point, often with a stronger signal, to trick users into connecting automatically.
Once connected, the attacker can intercept traffic, inject fake login pages, or capture credentials. These are ineffective in zero trust environments but very effective on older or misconfigured devices that don’t validate the AP’s identity.
To mitigate both evil twins and rogue access points:
- Enforce 802.1X or NAC to block unauthorised devices at the network switch level.
- Enable Protected Management Frames (802.11w) and WPA3-Enterprise so APs and clients authenticate each other (zero trust).
- Continuously monitor for unknown WiFi signals or new MAC addresses through your WLAN controller or security dashboard.
Shared or weak credentials
Many small businesses still rely on a single shared Wi-Fi password, often written on the wall, printed on guest cards, or shared over email.
While convenient, this setup quickly becomes a liability: if one employee leaves, shares it, or connects an unmanaged device, anyone with that password can access the network.
Without proper segmentation or visibility, a leaked key gives outsiders insider-level access, allowing them to scan or exploit connected devices. Even if guest WiFi is safely isolated, shared credentials on the internal WLAN remain one of the most common and preventable security weaknesses.
How to mitigate:
- Replace PSKs with 802.1X authentication and RADIUS, issuing unique credentials per user or device.
- Integrate with Active Directory or Microsoft Azure AD for automatic revocation and conditional access.
- Rotate passwords regularly and create guest VLANs to isolate visitor traffic from internal systems.
How to set up a business Wireless LAN
Besides home offices and other very small deployments that rely simply on a single access point at the router, all business WLANs require careful planning, configuration and management to ensure they are secure and fulfil the connectivity requirements.
Here are the typical steps for setting up a business WLAN:
1. WLAN planning
This stage determines what the WLAN must deliver. It involves analysing the physical environment, expected usage, and long-term needs:
- Floor layout: Room shapes and building materials influence how radio signals propagate, creating potential weak spots or coverage shadows.
- User and device density: Determines how many access points (APs) are needed and where higher-capacity coverage is required.
- Interference sources: External networks, machinery, or structural elements may degrade signal quality.
- High-traffic areas: Spaces with frequent meetings or gatherings often require additional capacity.
- Scalability expectations: Ensures the design keeps pace with organisational growth without major rework.
The outcome is a clear set of technical requirements that include coverage, capacity, and environmental constraints, which directly guide the hardware decisions that follow.
2. Hardware selection
Using the requirements identified during planning, the next step is choosing infrastructure capable of meeting them. Here are the key considerations:
- Access point type and capabilities: Selected to match coverage areas, density demands, and environmental conditions (indoor, outdoor, warehouse, high-ceiling, etc.). For example, the WiFi generation (6/6E/7) and any add-on capabilities.
- Backhaul design: Wired, wireless mesh, or hybrid, chosen based on cabling feasibility, performance needs, and building constraints.
- Network infrastructure: Switches, routers, and firewalls sized appropriately for expected traffic, VLAN design, and security policies.
- Management architecture: Cloud-managed, controller-based, or standalone, depending on scale, operational preference, and required visibility.
The outcome is a hardware stack aligned to the planned design, ready for deployment.
3. Deployment and configuration
Once the hardware has been installed, IT teams must configure it according to the design and ensure it aligns with business performance and security requirements. This stage brings together both operational setup and security controls.
- SSID structure: Separate staff, guest, and IoT networks maintain clarity, prevent congestion, and support policy enforcement.
- VLAN mapping: Extends existing network segmentation (e.g., accounting, management, guest) into the WLAN so that traffic remains isolated and controlled.
- Authentication and access control: Applying appropriate security methods, such as Multi-Factor Authentication for staff and simplified access for guests, ensures only authorised users and devices can connect.
- Traffic segregation: Guest and IoT networks must remain isolated from corporate systems to limit risk and reduce exposure.
- Firewall and policy alignment: WLAN traffic should follow the same internal access rules, inter-VLAN restrictions, and monitoring standards used on the wired network.
- Roaming behaviour: Consistent AP settings support smooth transitions between access points, especially important for mobile devices and voice applications.
- QoS policies: Prioritising critical applications such as VoIP, video conferencing, or business-specific systems maintains VoIP call quality during peak usage.
The outcome is a fully deployed, secured, and operational WLAN that meets the organisation’s technical, performance, and security requirements, ready for testing, optimisation, and phased rollout.
4. Testing and optimisation
With the WLAN deployed and configured, the next step is to verify that it behaves as intended and make adjustments based on real-world performance. Testing ensures the design holds up under actual conditions before full-scale rollout. The key tasks are:
- Coverage and signal verification: Walking the site with basic survey tools confirms that actual signal levels match the planned design and that no unexpected dead zones or weak spots are present.
- Performance and roaming checks: Testing throughput, latency, and movement between access points validates that users experience stable connectivity, especially in high-traffic areas or during voice/video sessions.
- Interference and channel analysis: Reviewing AP channel use and local interference helps identify overlaps or noisy areas that may require power adjustments or channel changes.
- Load and capacity testing: Simulating real user numbers or device types ensures the WLAN can handle peak demand without degradation.
- Configuration refinement: Small adjustments, such as transmit power, band steering, or minimum data rates, can significantly improve overall reliability and efficiency.
- Staged rollout: Deploying the WLAN to a limited user group first helps identify issues early and refine settings before expanding to the wider organisation.
The outcome is a validated and optimised WLAN that performs consistently across the site, ready for full production use.
Common issues in business Wireless LANs
Despite good planning and ample testing, WLANs usually encounter issues from time to time due to changing real-world conditions. Below are common symptoms and what they typically indicate, along with brief guidance on how to address them.
Slow or unstable connections
Often caused by interference from neighbouring networks, metal structures, machinery, or poor channel allocation.
Fix: Adjust channel selection, optimise transmit power, and reduce interference by reviewing the RF (radio frequency) environment.
Access point overload due to too many users
When too many devices connect to a single access point (AP), performance and responsiveness drop sharply.
Fix: Add more APs in high-density areas, rebalance coverage, or adjust band-steering and load distribution settings.
Dead zones or weak coverage
Usually, the result of incorrect access point placement, unexpected signal obstruction, insufficient AP density and insufficient testing before full rollout.
Fix: Reposition APs, add additional units, or adjust antenna orientation and power levels.
Device authentication errors
Often linked to misconfigured authentication methods, RADIUS timeouts, certificate issues, or mismatched security policies.
Fix: Verify authentication settings, check RADIUS integration, ensure time synchronisation, and confirm certificates or credentials are valid.
Poor roaming or dropped sessions
Caused by inconsistent AP settings, mismatched RF parameters, or gaps in coverage between APs.
Fix: Standardise AP configurations, align channels and power levels, and ensure overlapping coverage is sufficient for roaming.
Guest or IoT devices accessing internal resources
Indicates incomplete or incorrect segmentation on VLANs or firewall rules.
Fix: Review VLAN assignments, tighten inter-VLAN firewall policies, and validate network isolation is functioning as intended.
The future of business Wireless LANs
Wireless LANs continue to evolve rapidly as AI, robots, and IoT demand higher and higher performance and stronger security. Several emerging trends are shaping how organisations will design and operate their networks in the coming years.
Adoption of WiFi 7
WiFi 7 is the latest standard; it was only released in 2024, so only a few businesses have rolled it out. It offers multi-gigabit speeds, improved spectrum efficiency, and lower latency. WiFi 7 will gradually become the standard for high-density offices and bandwidth-heavy environments.
Use of 6 GHz spectrum
The cleaner 6 GHz band reduces interference and provides more consistent performance, especially in crowded urban areas or large corporate buildings. As of the end of 2025, it remains under consultation by Ofcom.
AI WLAN automation
AI-driven controllers and cloud platforms will increasingly handle channel selection, power tuning, anomaly detection, and optimisation without manual intervention, leaving IT teams focusing on executive functions.
Unified wired and wireless management
Networks are increasingly moving toward centralised policy engines where access control, segmentation, and monitoring apply consistently across both wired and wireless environments (as well as local and wide area networks).
Zero Trust WLANs
Like all network components, WLANs are expected to follow Zero Trust Network Access (ZTNA) architectures completely, meaning everything from device access to data flow is frequently verified to ensure higher security.
Zero trust is becoming increasingly integrated across all networks, so local, wide, wireless, wired, cloud, and on-site should eventually become fully unified.
IoT and operational devices
As more sensors, automation systems, and specialised devices connect wirelessly, WLANs will require stronger segmentation, monitoring, and support for diverse device capabilities.
Business Wireless LANs – FAQs
Our business networking experts answer commonly asked questions about Wireless LANs and how they support modern organisations.
What is a Wireless LAN and how is it different from WiFi?
A Wireless LAN or WLAN refers to the wireless component of a local area network. WiFi is the technology that delivers that wireless connectivity.
In everyday language, the terms are often used interchangeably (“Use the WiFi”), but technically, the WLAN is the network, while WiFi is the method of connecting to it.
Is Wireless LAN suitable for small businesses?
Yes. WLANs are fundamental for businesses of all sizes. They connect critical devices such as payment terminals, laptops, tablets, scanners, and mobile phones. Small organisations especially rely on WLANs for day-to-day operations.
How secure is a Wireless LAN?
When properly designed and configured, a business WLAN is highly secure and can reliably protect corporate data. Security issues typically arise not from the technology itself, but from misconfigurations, weak passwords, outdated equipment, or lack of ongoing management, which are common challenges in smaller organisations.
See our WLAN security section for best practices.
Can Wireless LAN replace wired LAN completely?
It depends on the business. Wired LANs remain the core of most networks, providing stable, high-performance connectivity for servers, switches, VoIP phones, and other fixed devices. However, small sites with only a few devices can operate entirely on WiFi, especially if performance requirements are modest.
How much does it cost to install a Wireless LAN for a business?
Costs vary depending on the size and complexity of the network.
In small businesses, a WLAN is often included as part of a standard full fibre business broadband service, using the router as the sole access point with no additional cost.
In SMEs, deployments requiring multiple APs, mesh coverage, enterprise authentication (802.1X), conditional access, or enhanced security features typically range from a few hundred to a few thousand pounds.
In large or complex enterprise sites, WLANs require custom planning, design, hardware procurement, installation, and ongoing management. These projects often reach tens of thousands of pounds, especially when delivered by a Managed Service Provider.

