What is Business Email Compromise (BEC) and how to avoid it
Business Email Compromise (BEC) is a scam where attackers impersonate trusted email senders to trick businesses into making fraudulent payments or sharing sensitive data.
It’s highly dangerous because it bypasses advanced defences by exploiting human trust and urgency.
This guide explains how BEC works, its impact, and how to prevent and respond effectively when one occurs.
Contents
- What is Business Email Compromise (BEC)?
- How does Business Email Compromise (BEC) happen?
- Warning signs of a Business Email Compromise (BEC)
- What to do if your business is hit by BEC
What is Business Email Compromise (BEC)?
Business Email Compromise (BEC) is a targeted form of social engineering in which attackers impersonate a trusted person or organisation, such as a company director, supplier, or client, to trick employees into transferring money or sharing sensitive information.
Unlike mass phishing campaigns that rely on malware or malicious links, BEC schemes exploit human trust and everyday communication patterns. Attackers research their targets, craft convincing messages or replies, and pose as legitimate contacts. BEC is less about breaching systems and more about manipulating people.
The goals of a BEC attack are typically straightforward: to steal funds, harvest valuable data, or gain access to internal accounts. Stolen information can then be reused to commit further fraud or to compromise other businesses within the victim’s supply chain.
BEC can take various forms depending on context. For example CEO fraud, invoice fraud, supplier impersonation and reply-hijacking are variations of the same core tactic of using deception to make fraudulent requests appear legitimate.
BEC has become one of the fastest-growing cyber threats to businesses because it’s inexpensive, difficult to detect, and often compelling.
Publicly available information on company websites, social media, and professional networking platforms like LinkedIn provides criminals with enough detail to impersonate senior staff or suppliers convincingly.
The shift to remote and hybrid work has further increased the risk, as more communication takes place digitally and critical business transactions are conducted via email, creating more opportunities for deception.
How does Business Email Compromise (BEC) happen?
Business Email Compromise (BEC) attacks typically unfold in a series of deliberate stages, each designed to appear legitimate and evade detection. Understanding these stages is key to recognising warning signs early and strengthening defences.
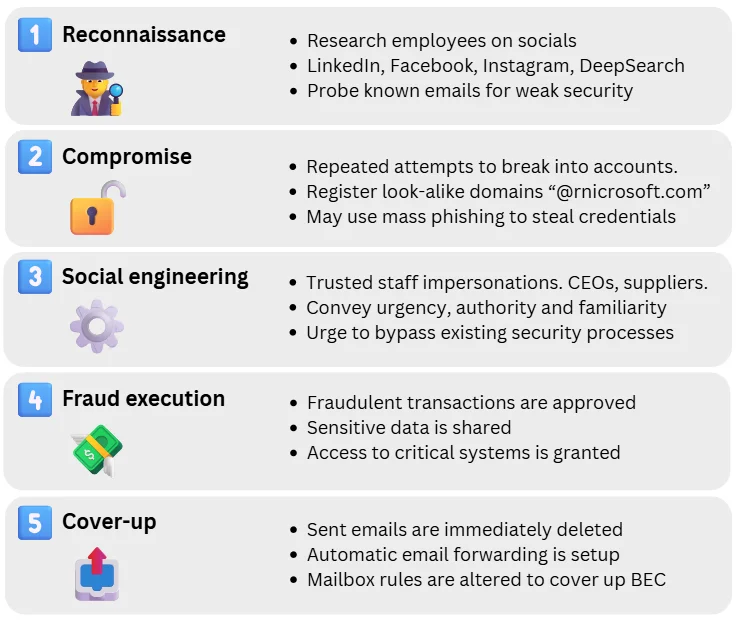
1. Reconnaissance
Attackers begin by collecting information about their target organisation and key personnel. Public sources such as company websites, LinkedIn profiles, and social media accounts provide valuable details about job roles, hierarchies, and supplier relationships.
They may also probe employee email accounts to identify weak points, such as reused or leaked passwords, or a lack of multi-factor authentication (MFA). Shared mailboxes, which are often harder to secure with MFA, can be particularly vulnerable.
Other alternatives to gain access include OAuth abuse (tricking users into granting a malicious app access to their account) or bypass text-based MFA with token theft or a SIM-swap attack.
This research enables attackers to craft convincing, targeted messages from credible accounts that closely align with genuine business operations.
2. Email compromise or spoofing
Once potential victims and weakly protected accounts are identified, attackers attempt to compromise the account or impersonate its owner.
If direct access isn’t possible, they may instead register a spoofed or look-alike domain (for example, rnicrosoft.com instead of microsoft.com).
All of these approaches make fraudulent emails appear authentic, especially when the organisation’s email systems lack proper authentication controls (i.e. SPF, DKIM, DMARC, which are explained later).
3. Social engineering
With the groundwork in place, attackers use social engineering to manipulate individuals into taking action.
They often impersonate senior executives or trusted suppliers, creating messages that convey urgency, authority, or confidentiality. The goal is to pressure recipients into bypassing normal verification or approval processes.
4. Fraud execution
The fraud is carried out once the target complies with the request. This might involve transferring funds to an attacker-controlled bank account, sharing sensitive company data, or granting system access.
Because legitimate users perform these actions, they can appear authentic and often evade automated security systems, even those protected by MFA.
5. Cover-up
After executing the attack, criminals frequently attempt to conceal their activity. They delete sent messages, alter mailbox folders, or create hidden inbox rules that automatically move fraudulent emails to folders such as RSS, Archive, or custom ones, keeping them out of sight.
They may also configure auto-forwarding so message copies are sent to an external address they control, allowing them to quietly monitor conversations and retain access even if credentials are changed.
Such tactics obscure evidence of compromise and delay discovery, giving attackers more time to profit or launch follow-on attacks before the breach is identified.
Common BEC attack types
Business Email Compromise can take several forms, each designed to exploit trust and routine communication within an organisation.
The tactics may vary, but the objective is always the same: To deceive employees into transferring funds or disclosing sensitive information, both of which are among a business’s most valuable assets.
CEO fraud
Frequency: Very common
Attackers impersonate senior executives to instruct staff to make urgent or confidential payments. These messages appear authoritative and time-sensitive, discouraging normal verification. They often use phrases such as “strictly confidential” or “I need this processed urgently” to create pressure and urgency.
Invoice fraud
Frequency: Very common
Criminals pose as legitimate suppliers or service providers and send fake or modified invoices requesting payment to new account details. Because these requests align with real business activity, they frequently bypass routine checks, particularly during busy periods such as quarter-end or financial close.
Account takeover
Frequency: Common
Instead of spoofing an email address (e.g. mrichards@rnicrosoft.com), attackers compromise genuine business email accounts using stolen credentials. Once inside, they quietly monitor conversations and insert fraudulent messages at strategic moments. Emails from legitimate accounts are particularly convincing and difficult to detect.
Supply chain compromise
Frequency: Increasingly common
Also known as vendor email compromise, this tactic targets suppliers directly, often smaller companies with weaker security controls. Attackers infiltrate a supplier’s mailbox and modify invoices or payment instructions before forwarding them to customers. Because these messages come from authentic domains, they are challenging to identify as fraudulent.
See the Tesco 2025 cyberattack case study for an example of how supply chain compromises can disrupt entire industries.
Payroll diversion fraud
Frequency: Somewhat common
Fraudsters impersonate employees and contact HR or payroll teams, requesting that salary payments be redirected to a new bank account. These changes often go unnoticed until payroll is processed, by which point the funds are irretrievable.
HR impersonation scams
Frequency: Occasional
Criminals pose as HR or internal support staff to request personal information, payslips, or tax details. These scams often coincide with year-end or tax periods and can lead to identity theft or further internal compromise. The goal is usually to steal sensitive data rather than money, catching employees off guard.
Gift card scams
Frequency: Frequent, but low impact
A low-value but persistent form of BEC. Attackers impersonate managers or directors and ask employees to urgently buy gift cards for clients or events. Once the codes are shared, they are redeemed or resold immediately.
Legal or investment impersonation
Frequency: Rare, but high impact
Attackers impersonate lawyers, solicitors, or investment advisors involved in property transactions, mergers, or acquisitions. They exploit confidentiality and perceived authority to convince targets to transfer large sums of money, often under the guise of legitimate legal or financial instructions.
Why BEC is so dangerous for businesses
Business Email Compromise (BEC) poses a significant cyber risk because it targets the weakest link in most security systems: human trust.
BEC bypasses strong perimeters such as firewalls, antivirus and cybersecurity software by manipulating people directly. The idea is to deceive even well-trained staff, often when they’re under pressure, distracted or fatigued.
These attacks cause immediate financial losses and can trigger a chain of legal, operational, and reputational consequences that frequently prove more damaging than the initial fraud.
Financial losses
The most immediate impact of BEC is monetary. Fraudulent payments (e.g. supplier invoices, payroll transfers, deposits) are diverted to attacker-controlled accounts, often routed through overseas banks or converted to cryptocurrency, making recovery nearly impossible.
For small and medium-sized businesses, a single successful incident can severely disrupt cash flow, particularly when cyberinsurance coverage is limited or denied.
Operational disruption
A significant BEC incident can halt operations as the business undertakes investigations, system audits, and account freezes. Managing these processes requires time and resources, reducing productivity and delaying core business functions.
When supplier or client payments are compromised, relationships can deteriorate quickly, affecting delivery schedules, project timelines, and customer satisfaction.
Legal and regulatory exposure
Beyond direct losses, businesses may face legal and cybersecurity compliance obligations under UK data protection and financial regulations.
If personal or financial information is compromised, the incident could trigger reporting requirements to the Information Commissioner’s Office (ICO).
Organisations may also face scrutiny from banks, regulators, or insurers, particularly if investigations reveal insufficient internal controls or a lack of employee awareness training.
Insurance and liability implications
Cyber insurance policies do not always cover BEC-related losses, especially when payments were willingly authorised by employees under deception. Insurers may classify such cases as social engineering or human error, leaving companies responsible for the full cost of the fraud.
Reputational damage
Loss of trust when the beach affects customers or suppliers is often the most challenging thing to rebuild.
It can damage relationships with clients, suppliers, and partners who may question its internal controls. Public exposure or legal proceedings can also harm brand reputation and erode customer confidence.
Warning signs of Business Email Compromise (BEC)
Recognising the early warning signs of Business Email Compromise (BEC) is one of the most effective ways to prevent financial and data loss.
Most scams rely on subtle inconsistencies such as unusual payment instructions, unfamiliar tone, or suspicious timing, details that only stand out when staff know what to look for.
Training teams to identify these clues can significantly reduce risk.
Financial red flags
These are often the easiest to recognise, although very targeted attacks can be persuasive. Requests involving payments are the most obvious signs of potential fraud. Be alert to:
- Unusual or last-minute payment requests, especially those outside routine procedures.
- Changes to bank details or new supplier accounts that haven’t been verified.
- Bank details are sent as images or embedded in attachments to evade keyword or fraud detection filters.
- Invoices that differ slightly in layout, reference number, or currency.
- New payees with names resembling legitimate suppliers or internal staff.
- Payment amounts that fall just below approval thresholds.
- Requests made just before holidays or at the end of the month, when approval processes may be rushed.
The key to preventing this is to always verify financial changes directly with a known contact using previous contact details, ideally by voice or video call on your business VoIP phone system, not through contact information provided in the suspicious email.
Behavioural clues
Attackers manipulate people, not systems. Notice when communication feels slightly off:
- Emails from executives or colleagues using urgency, secrecy, or authority to pressure for quick action.
- Requests that break company policy or skip usual sign-off steps.
- Tone, language, or phrasing that doesn’t match the sender’s usual style.
- Messages that discourage verification, such as “Please don’t call; I’m in a meeting.”
If a request feels unusual or out of character, verify it through a trusted channel before acting.
Technical anomalies
These are often subtle, but even convincing scams leave small digital trails which can help you confirm already suspicious activities. Keep an eye out for:
- Slight misspellings or variations in domain names.
- Domains that are newly registered or have very recent creation dates.
- Sender display names that don’t match the underlying email address, or reply-to addresses that differ from the sender’s domain.
- Missing sent items or unfamiliar forwarding rules in your mailbox are potential signs of compromise.
- External emails flagged as “Outside the organisation” but claiming to be from a colleague.
- Security banners such as “External email” or “This message failed DMARC validation,” where your systems support these warnings.
What to do if your business is hit by BEC
Even with a well-prepared workforce, there is a significant chance that a successful BEC attack will eventually occur.
Not only are impersonation tools like AI deep fakes evolving fast, but a single lapse due to fatigue, distraction, or miscommunication can be enough for an attacker to succeed.
BEC mitigation is therefore crucial. A clear BEC Incident Response Plan (IRP) allows your organisation to act quickly and limit financial, operational, and reputational damage.
The key is to act immediately, preserve evidence, and follow a structured process from containment through to recovery:
Immediate response
Takes place: Within the first hour
This stage focuses on damage control and containment. It’s the cybersecurity equivalent of calling emergency services.
- Stop further losses: Suspend any pending transfers and contact your bank’s fraud department immediately to request a recall or freeze of funds. If the receiving bank is known, report the incident to them as well and request a Safeguard confirmation (part of many banks’ internal fraud-handling processes). Acting fast greatly increases the likelihood of recovering funds.
- Secure access: Change passwords for all potentially affected accounts (emails and internal systems that may have been breached) and enforce multi-factor authentication (MFA) if not already active.
- Tech containment: Revoke active sessions, reset MFA (not just passwords), rotate API tokens, remove unapproved OAuth app consents, and disable external mail forwarding.
- Freeze changes: Temporarily suspend the creation of new payees and lower or freeze payment limits until verification controls are rechecked.
- Disconnect compromised systems: If a computer, mailbox, or cloud account shows signs of unauthorised access, isolate it from the network until it can be reviewed by IT or your cybersecurity provider.
- Alert key staff: Notify finance, IT, and senior management teams to coordinate the immediate response and ensure actions are logged and consistent.
Incident management
Takes place: Within the first 24 hours
Once the immediate threat has been contained, the next phase involves investigation, reporting, and coordination across internal and external stakeholders.
- Preserve evidence: Save and export the original email (with headers), message logs, and any communication threads. Do not delete suspicious messages, even if they’re embarrassing; they are vital for investigation and law enforcement.
- Contact Action Fraud: This is the UK’s national reporting centre for fraud and cybercrime. Contact them and record the reference number.
- Notify the National Cyber Security Centre (NCSC): If internal systems or data were accessed, the NCSC can provide technical guidance.
- Inform internal stakeholders and legal counsel: Early communication ensures compliance with data protection laws and keeps decision-makers aligned on response strategy.
- Cyber insurance: If you hold cyber insurance, report the incident within the first 24 hours. Some policies require early notification to cover investigation costs or financial losses.
Post-incident recovery
Takes place: Days or weeks after the incident
Once the situation is stabilised, shift focus to recovery, communication, and strengthening future defences.
- Notify affected parties: If suppliers, clients, or employees may have been exposed to fraudulent messages, contact them directly and explain what happened. Quick, honest communication protects relationships and prevents follow-on scams.
- Conduct a security review: With your IT or cybersecurity partner, determine how the attacker gained access (e.g., a weak password, a phishing email, or missing MFA). Check mailbox rules, forwarding settings, and login histories for further compromise.
- Update defences and policies: Review financial approval workflows, supplier verification processes, and email authentication (DMARC, SPF, DKIM). Implement dual sign-off for all payment or banking changes.
- Provide training: Use the incident as a case study to raise awareness, particularly among finance, HR, and executive teams. Walk through how the attack happened and what should trigger suspicion next time.
- Review insurance and legal obligations: Follow up on any cyber insurance claims. If personal data was involved, assess whether to report the breach to the Information Commissioner’s Office (ICO) within 72 hours, as required under GDPR.
How to prevent BEC with cybersecurity solutions
Preventing Business Email Compromise (BEC) is less about deploying complex technology and more about awareness, access control, and disciplined processes.
It’s about giving employees the time and confidence to spot scams before they succeed, and putting layered systems in place that make it difficult for attackers to exploit human error.
The following cybersecurity solutions can dramatically reduce BEC risk for organisations of any size.
Access and credential protection solutions
Securing access is the first line of defence against BEC because most attacks begin by hijacking a legitimate account to make fraudulent requests appear credible.
Identity-focused protections make it harder for attackers to exploit stolen or leaked credentials:
- Multi-Factor Authentication (MFA): Adds a second verification step, preventing attackers from logging in even with stolen passwords.
- Password Managers: Encourage the use of unique, complex passwords for every account and reduce password reuse across systems.
- Dark web monitoring services: Alert businesses when staff credentials appear in data breaches so passwords can be reset before attackers exploit them.
Implementation tip: Microsoft 365 and Google Workspace include built-in tools for MFA, password policies, and login alerts, simple measures that small businesses can enable with minimal effort.
Email security and anti-spoofing solutions
Email remains the primary attack vector for BEC because of how easily senders can be impersonated. Authentication protocols and secure gateways protect your domain from spoofing and help filter malicious messages before they reach users.
Key defences include:
- SPF (Sender Policy Framework): Specifies which mail servers are authorised to send email on behalf of your domain.
- DKIM (DomainKeys Identified Mail): Digitally signs emails to prove they haven’t been altered in transit.
- DMARC (Domain-based Message Authentication, Reporting and Conformance): Instructs other mail servers on how to handle unauthenticated messages (reject, quarantine, or allow).
- Secure Email Gateways: Filter inbound messages, scan attachments, and flag or block suspicious content.
- Sandboxing and URL Rewriting: Test suspicious attachments or links in safe environments before they reach inboxes, preventing phishing payloads and credential theft.
Implementation tip: Most hosting providers and cloud platforms set up SPF and DKIM by default, but DMARC needs to be configured manually. Set it to reject unauthenticated messages and monitor reports regularly.
Human awareness and behavioural resilience solutions
People are the final line of defence, and often the first target. Even the best technology can’t prevent someone from trusting a convincing message.
Ongoing awareness, clear procedures, and a verification-first culture help employees recognise social engineering and respond safely.
- Cybersecurity awareness training: Regular, short sessions help staff recognise phishing, impersonation, and social engineering tactics before they happen.
- Verification culture: Encourage staff to double-check unusual or high-pressure requests by phone or in person rather than email.
Implementation tip: Short, focused micro-trainings (15–30 minutes quarterly) are far more effective than one long annual seminar. Frequent refreshers keep awareness high and practical.
Financial and process control solutions
Most BEC losses occur when employees are tricked into transferring money or changing payment details. Strong internal processes can stop these attempts before any funds move.
- Dual approval workflows: Require two people to authorise any high-value or unusual payments.
- Out-of-band verification: Confirm changes to bank details or urgent transfers via phone or video call, not email.
- Audit trails and alerts: Use accounting software to flag anomalies or irregular payment patterns.
Implementation tip: Business banking platforms offer dual-authorisation and anomaly alert features, which are simple ways to build fraud resistance into daily operations.
Endpoint and integrated protection solutions
While MFA and credential monitoring prevent most unauthorised logins, endpoint and managed detection solutions help identify suspicious behaviour that occurs after an attacker gains entry.
They reduce the “blast radius” of a successful compromise by detecting and isolating unusual activity early.
- Endpoint security integration: Connects email and device monitoring to detect unusual downloads, file access, or login activity.
- Managed Detection and Response (MDR): Provides 24/7 expert monitoring, investigation, and rapid incident containment.
- Identity protection integration: Correlates user activity across accounts, devices, and email to detect compromised credentials.
- Zero Trust Network Access (ZTNA): Continuously verifies every user and device, requiring reauthentication for access to sensitive systems.
- Network Segmentation (VLANs): Separates critical departments such as finance and HR to prevent lateral movement in case of compromise.
BEC incident response plan
No defence is perfect, so every business should maintain a clear, rehearsed BEC response plan. A defined playbook ensures a fast, coordinated response to limit damage and speed recovery.
- Incident response playbook: Define clear steps and responsibilities for detecting, containing, and reporting BEC incidents. Make sure all key staff know their role.
- Reporting and communication channels: Ensure employees know how to report suspicious messages or potential compromises quickly and confidentially.
- Business continuity integration: Include BEC scenarios in wider disaster recovery and continuity plans to minimise disruption if an attack succeeds.
- Post-incident review: After any incident, conduct a short debrief to identify what went wrong, update controls, and retrain affected teams.
Implementation tip: Treat your BEC response plan as a living document. Test it annually, update it after every incident or near miss, and make sure contact details and processes stay current. Cyber Essentials guidance documents have great resources for this.
Business Email Compromise – FAQs
Our cybersecurity experts answer some of the most common questions about Business Email Compromise (BEC).
How can small UK businesses protect themselves affordably?
Use free or built-in tools within Microsoft 365 or Google Workspace. Enable MFA, SPF, DKIM, and DMARC. Provide short, regular cyber-awareness training, verify payment changes by phone, and use dual approval to authorise all payments.
Why are anti-BEC e-mail configurations so complex?
Email was created long before cybercrime existed, and there was no built-in system to verify who could send messages from your domain.
This makes spoofing easy unless protections are put in place.
Setting up SPF, DKIM, and DMARC records tells receiving mail servers which emails are legitimate and blocks fakes pretending to be from your business.

