Guide to the best business VPN services, providers and deals
VPNs encrypt all business data travelling over the internet, keeping remote employees, site-to-site connections, and any links to cloud applications secure and private.
This guide covers the best business VPN services, explaining the different types, how they work, and how to select and use one effectively.
Contents:
- What is a VPN?
- Why do businesses need VPNs?
- Top business VPN solutions
- Business VPN costs and pricing
- How business VPNs work
- Types of business VPN
- Key components of a business VPN deployment
- How to set up a business VPN
- Integrating business VPNs with broadband
What is a VPN?
A Virtual Private Network (VPN) is a technology that establishes a secure, encrypted connection between devices, sites or the cloud over the public internet.
While there are various types of VPNs, all of them are:
- Virtual: The connection is software-based, rather than physical. It sits on top of the physical lines that carry data.
- Private: All data sent through the VPN is encrypted and shielded from unauthorised access.
- Networked: It makes a tunnel between two or more endpoints to create a single, secure network.
VPNs are best known for providing remote employees with secure access to company networks, but their business applications extend far beyond that.
IT teams often set up and manage always-on VPNs between branch offices, data centres and cloud systems to protect data in transit while ensuring compliance with UK cybersecurity regulations.
Businesses typically avoid consumer-grade VPNs like NordVPN because they lack the scalable access controls, customisability, routing control or management features necessary for enterprises.
Why do businesses need VPNs?
VPNs are a defensive technology that encrypts data and controls access across public and private networks. They’re used by businesses to ensure:
Secure, private communication
All data in a VPN connection is encrypted, meaning no third party (e.g. internet providers, hackers, or internal threats) can read or trace it. VPN tunnels are typically formed between remote employees, devices, headquarters, branches and data centres.
Access control
Besides data encryption and obfuscation, VPNs can act as gatekeepers, allowing only approved devices and users to connect to sensitive systems, whether on-premises, in the cloud, or across offices (site-to-site, site-to-cloud).
By pass geo-block issues
Data travelling through VPNs will have the IP/location of the host, letting businesses access region-restricted services and operate globally without geo-block issues.
Regulatory compliance
The encryption and access control provided by VPNs is often critical for meeting legal and industry requirements for data protection like GDPR (Data Protection Act 2018), HIPAA, etc.) While not the only solution, it is often a cost-effective one.
Top business VPN solutions
The “best” VPN solution for your business depends entirely on what you’re trying to achieve.
A small business that requires straightforward VPN remote access for a handful of users doesn’t need the complex tooling of a multi-site enterprise with strict compliance and thousands of employees.
Some providers focus on basic open-source VPN tools you host yourself. Others offer fully managed, cloud-based services with user controls, dashboards, and built-in features.
Here are the top solutions for each use case, from the DIY software providers to the fully managed providers for startups and enterprises:
| Solution | Best for | Type of VPN (hosting) | Key features |
|---|---|---|---|
| Tailscale | Tech-savvy micro teams | Remote access (On prem) | WireGuard-based mesh networking, zero config, device-to-device connectivity |
| NordLayer | Small teams without IT departments | Remote access (Cloud) | Easy setup, SSO, centralised user control |
| Focus Group Business VPN | Small teams without IT (UK-based) | Remote access Site-to-site (Managed) | Fully managed service, UK support, bundles with connectivity/ VoIP telephony |
| Perimeter 81 | Multi-site SMEs | Remote access Site-to-site (Cloud) | Scalable cloud gateways, user segmentation, policy-based access |
| OpenVPN Access Server | SMEs with in-house IT | Remote access Site-to-site (On prem or hybrid) | Customisable, open-source-based, can run on your own infrastructure |
| SonicWall Secure Mobile Access (SMA) | SMEs needing strong perimeter control | Remote access (Cloud) | Endpoint compliance, granular access control, hardware or virtual appliance |
| Cisco Secure Remote Worker (AnyConnect) | Enterprises with compliance needs | Remote access Site-to-site (Any) | Endpoint control, full-stack Cisco integration, robust policy enforcement |
| Fortinet FortiClient + FortiGate | Enterprises with distributed networks | Remote access Site-to-site (On prem or hybrid) | Integrated firewall + VPN appliance, robust logging, enterprise-grade performance |
| WatchGuard Mobile VPN | Regulated SMEs or public sector | Remote access (Any) | Supports multiple VPN types (IPSec/SSL), MFA, policy control, UK MSP integrations |
Business VPN costs and pricing
The cost of a business VPN depends largely on how it is deployed, the scale of your organisation, and the level of management or support required.
Importantly, VPNs are rarely purchased as standalone products. Instead, they are typically delivered in one of three ways:
- Built in-house using open-source tools: This offers the lowest direct cost but requires technical expertise for setup, hosting, and maintenance. Common in small teams or organisations with internal IT capabilities.
- Bundled into cloud VPN platforms: These subscription-based services charge per user per month. They include management tools, support, and security features, ideal for businesses seeking rapid, low-maintenance deployment.
- Included within managed IT services or network infrastructure: VPN functionality may be part of a larger package, such as a managed firewall, leased line, or full IT support contract. This typically carries a higher cost, but includes setup, support, and integration.
The table below outlines the estimated costs and what is included in each of these deployment scenarios:
| Scenario | Estimated cost | Notes |
|---|---|---|
| Fully self-hosted remote access VPN | £0 (direct cost) | Uses open-source software (e.g. OpenVPN, WireGuard). Cost = time, setup, and basic hardware. |
| Cloud VPN platform (e.g. NordLayer, Perimeter 81) | £7–£15 per user/month | Subscription-based. Scales with users. Includes access control and support. |
| MSP-delivered managed VPN (SME package) | £50–£200/month | Often bundled with IT support, VoIP or broadband. Pricing depends on the services included. Usually unlimited users. |
| Enterprise VPN with firewall (e.g. Cisco, Fortinet) | £1,000+ setup + ongoing license | Usually part of wider network/security deployment. Managed by an internal IT team or a managed service provider. |
| VPN included in a leased line | Bundled into leased line broadband costs | Typically included in larger connectivity contracts for multi-site businesses. |
How business VPNs work
When a VPN tunnel is set up at your business, four key processes happen in the background to ensure the connection meets your business security, privacy and performance requirements:
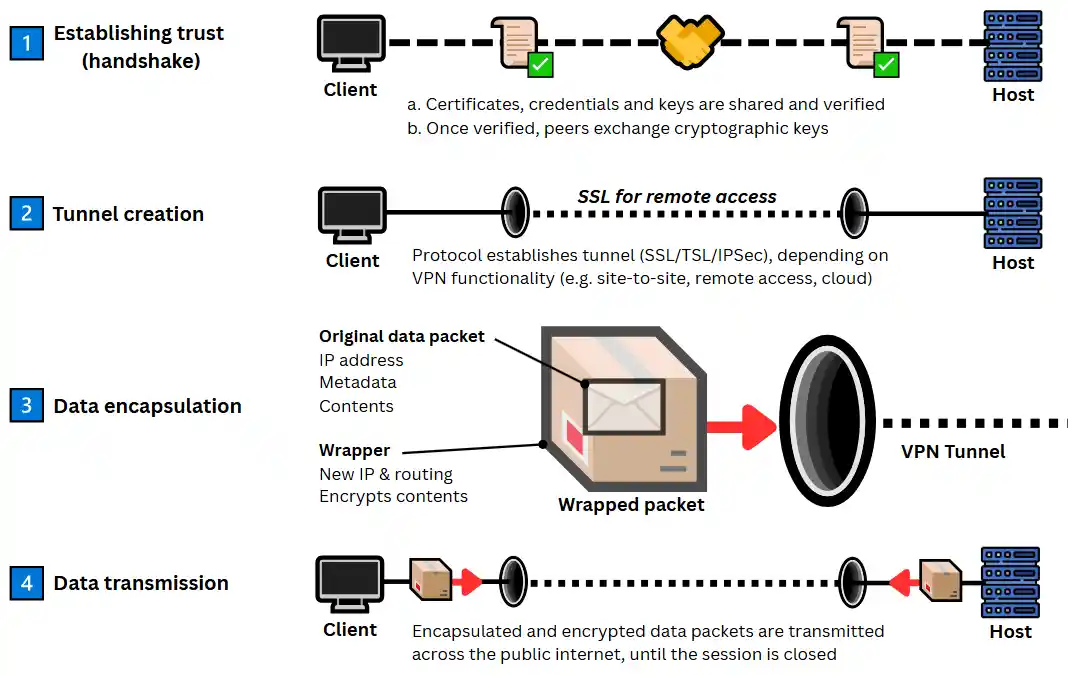
1. Establishing trust (handshake)
To initiate a VPN connection, both endpoints (peers) begin by verifying each other’s identity. This is typically done by sharing digital certificates, pre-shared keys, or login credentials.
Once authenticated, both peers perform a cryptographic key exchange using protocols such as Diffie-Hellman or Elliptic Curve Diffie-Hellman.
This ensures they can agree on a shared set of encryption keys without ever exposing those keys to the broader internet.
2. Encrypted tunnel creation
Once trust is established, the VPN host forms an encrypted tunnel using a protocol (e.g. IPSec, SSL/TLS, WireGuard) that suits the required use case. For example:
- Network-layer VPNs, such as IPSec, encrypt all traffic leaving a device. These are ideal for persistent site-to-site connections between offices.
- Transport-layer VPNs, such as SSL/TLS, typically secure traffic from a specific application (e.g., a web browser or remote desktop client), making them best suited for remote access.
Regardless of the protocol, the VPN tunnel acts as a protected pathway through which encrypted data flows, invisible to anyone outside it.
3. Data encapsulation
Before transmitting data over the VPN tunnel, the data is encapsulated. This means wrapping the original data packet inside another packet that contains:
- A new IP header (hides the data’s origin),
- New routing metadata (hides the data’s path and destination), and
- Encryption (hides the data’s content).
Beyond security, this also helps users bypass geo-restrictions, enforce network access control, and isolate sensitive traffic to avoid cybersecurity threats.
4. VPN data transmission
Finally, the encapsulated and encrypted data packets are transmitted across the public internet. Thanks to strong encryption algorithms like AES-256, even if the traffic is intercepted, it remains unreadable without the correct decryption keys.
When the data reaches the receiving endpoint, it is decrypted and decapsulated, restoring the original content. The data is then delivered to its intended destination: a business application, internal server, or cloud resource.
The VPN tunnel remains active for the duration of the session and can be closed at any time by either peer to end the secure connection.
Types of business VPN
While VPN solutions can differ in architecture, deployment model, and underlying protocols, they are most commonly classified by their use case. That is, what the VPN is intended to do for the business:
Remote access VPNs
Remote access VPNs are designed to connect individual users (e.g. employees, third-party contractors, IT admins) to the organisation’s internal systems from outside the corporate network.
This is the typical setup for hybrid and travelling employees or fully remote teams. Users usually connect using VPN client software or a browser-based portal.
Most remote access VPNs use SSL/TLS (for app-specific access) or IPSec (to secure all traffic) to create an encrypted tunnel over the public internet.
Depending on configuration, users might gain full access to the internal network or only to specific services (via split tunnelling or access restrictions).
This helps limit risk while ensuring workers can securely access the tools they need.
Site-to-site VPNs
Site-to-site VPNs connect two or more fixed locations(e.g. head offices, branch offices, warehouses, or data centres) to form a unified private network.
These tunnels are typically always-on and rely on VPN gateways built into firewalls or business broadband routers at each location.
While they often run over standard internet connections using IPSec, many businesses layer site-to-site VPNs over high-performance private circuits such as as MPLS or Business Ethernet networks to ensure lower latency and higher reliability.
Site-to-site VPNs can also be integrated with SD-WAN, enabling the dynamic routing of encrypted traffic over multiple network links, thereby improving performance and resilience.
Businesses opt for VPN-as-a-Service (VPNaaS) models when they need to simplify deployment, especially for remote or temporary locations. These cloud-managed services reduce hardware dependencies while maintaining security and scalability.
Otherwise, self-hosted or hybrid setups offer businesses more customisability, especially in heavily regulated industries.
Cloud VPNs
Cloud VPNs create secure tunnels between on-premises infrastructure and cloud platforms, or between different cloud environments (multi-cloud setups).
They’re essential for businesses that rely on services like AWS, Azure, or Google Cloud, as they allow secure access to cloud resources, databases, and apps without exposing them directly to the internet.
Cloud VPNs are usually deployed using the cloud provider’s built-in VPN gateway services and are typically delivered as cloud-native solutions or VPNaaS (Virtual Private Network as a Service).
Typical use cases for cloud VPNs include:
- Connecting internal tools to cloud-hosted databases or applications
- Securing VoIP traffic between company phones and cloud-based business VoIP phone providers
- Enabling secure communication between two cloud services in a multi-cloud environment
Key components of a business VPN deployment
While the types of VPNs covered earlier are key for explaining VPN options to customers, how a VPN solution truly aligns with your business depends on its key deployment components.
Hosting, interfaces, protocols, routing, and additional security features all play a crucial role in the VPN’s suitability for your organisation.
Let’s break down each of these components in more detail:
VPN hosting
VPN hosting determines who controls and maintains the VPN infrastructure. Businesses must choose based on their size, technical capacity, and regulatory obligations:
- Self-hosted (on-premises): Typically deployed via VPN-capable firewalls or appliances. Common in enterprises or regulated sectors requiring full control.
- Cloud-hosted (IaaS or VPNaaS): VPN infrastructure is hosted in a public cloud or delivered as a managed service. Ideal for hybrid or fully remote workforces.
- Hybrid: A mix of on-premises and cloud VPNs. Enables flexible access across both physical and cloud environments.
- Fully managed (outsourced): Third-party vendors set up and manage the entire VPN solution, including maintenance, monitoring, and support.
VPN access methods
VPN access methods describe how authorised users (e.g. employees, contractors, or systems) securely connect to the business network. Common business VPN access methods:
- Dedicated VPN client software: Most common for employee devices. Deployed centrally via endpoint management (e.g., Cisco AnyConnect, Fortinet, Palo Alto GlobalProtect).
- Web-based access portals (SSL VPN): Browser-based logins for controlled, application-level access. Often used for partners or limited remote access.
- Always-on VPN clients: Enforced on corporate-managed laptops to automatically connect when the device is online. Common in regulated industries.
- Virtual desktop infrastructure (VDI) within VPN: In high-security environments, users connect to a virtual desktop environment that is itself within the VPN.
- VPN gateways: Used in site-to-site scenarios where routers or firewalls handle the VPN connection; no client required on end-user devices.
VPN protocols
Business VPNs use a range of protocols depending on the use cases. The choice affects encryption strength, performance, and support for specific applications.
These are the most common business VPN protocols:
- IPSec: The enterprise standard for secure, network-layer VPNs, often used for site-to-site tunnels and full-tunnel remote access.
- SSL/TLS: Used in remote access VPNs for application-level access, especially with SSL VPN portals. TLS is considered a newer version of SSL.
- OpenVPN: Open-source and versatile, often used in custom or mid-sized deployments.
- WireGuard: A modern, efficient protocol gaining traction for high-performance VPNs. Still maturing in terms of enterprise-grade features.
- Proprietary vendor protocols: Used in specific enterprise VPN appliances (e.g., Cisco, Palo Alto, Fortinet) may have enhanced tunnelling protocols.
- MPLS VPN: An enterprise-grade VPN designed for MPLS networks. It runs over the MPLS provider’s private network, rather than the public internet.
VPN routing
VPN routing defines how network traffic is handled once a connection is established. It directly impacts security, performance, and bandwidth usage:
- Full tunnel: All device traffic routes through the VPN. Ideal for security-focused environments or BYOD (bring your own device) scenarios where compliance is required.
- Split tunnel: Only business traffic routes through the VPN; all other traffic goes directly to the internet. Useful for improving performance and reducing load on central infrastructure.
- Policy-based routing: Traffic is routed based on rules (e.g., application type, destination, user group). Managed by firewalls or dynamically via business SD-WAN solutions.
VPN security features
Business-grade VPNs usually include additional security features beyond encryption. These features reduce the risk of data breaches, unauthorised access, and compliance violations:
- Multi-Factor Authentication (MFA): Enforced at the client or gateway level.
- Role-based access control (RBAC): Limit access to only the required resources based on job function. It can be implemented with the help of VLANs.
- Logging and auditing: Full session logs for compliance and incident investigation.
- Always-on VPN enforcement: Prevents employees from bypassing a VPN tunnel, especially on corporate devices.
- Kill switch and DNS leak protection: To maintain integrity if a VPN connection drops unexpectedly.
How to set up a business VPN
How you set up a business VPN depends on your use case and the key components required to support it.
While there are many possible configurations, the four common setups below will give you a clear idea of what a VPN deployment might look like in practice for your business:
1. Remote access VPN for a small team (self-hosted)
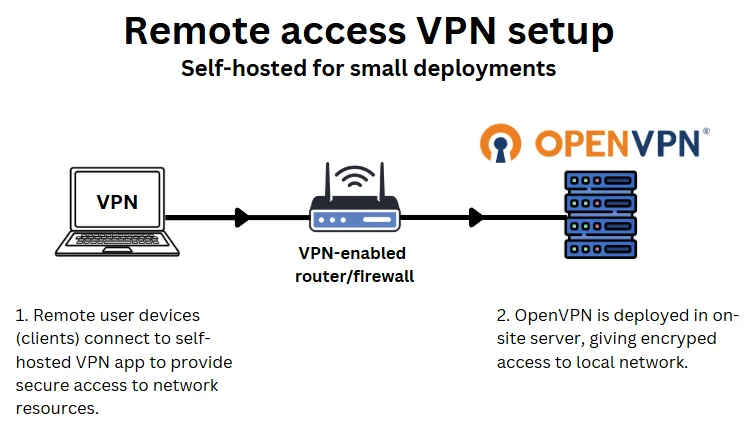
Who it’s for: SMEs with in-house or freelance IT support who want low-cost, secure remote access for employees working from home or on the move. For example, an independent accounting firm or a small design or marketing agency.
Small businesses with remote or hybrid teams often need secure access to internal systems such as file servers, CRMs, or remote VoIP solutions, particularly where SD-WAN is not in place.
Self-hosting a VPN remains a common approach because it’s cost-effective and relatively straightforward to set up using open-source tools like OpenVPN or WireGuard. However, it requires some technical know-how and ongoing in-house management.
Self-hosted VPNs can be deployed on-site or via a Virtual Private Server (VPS) hosted in the cloud or a data centre.
This setup typically requires:
- A VPN server (hosted on-site or via a VPS)
- VPN software such as OpenVPN or WireGuard
- VPN client applications installed on staff devices
- Firewall configuration and port forwarding
How its setup:
Your IT team installs and configures the VPN server, creates user credentials, and distributes connection profiles to staff.
Employees connect using a VPN client, either manually or via an always-on connection, encrypting their traffic and granting secure access to internal resources.
This setup provides complete control and low operating costs but relies on internal resources to monitor, maintain, and secure the VPN environment over time.
2. Managed VPN service (outsourced solution)
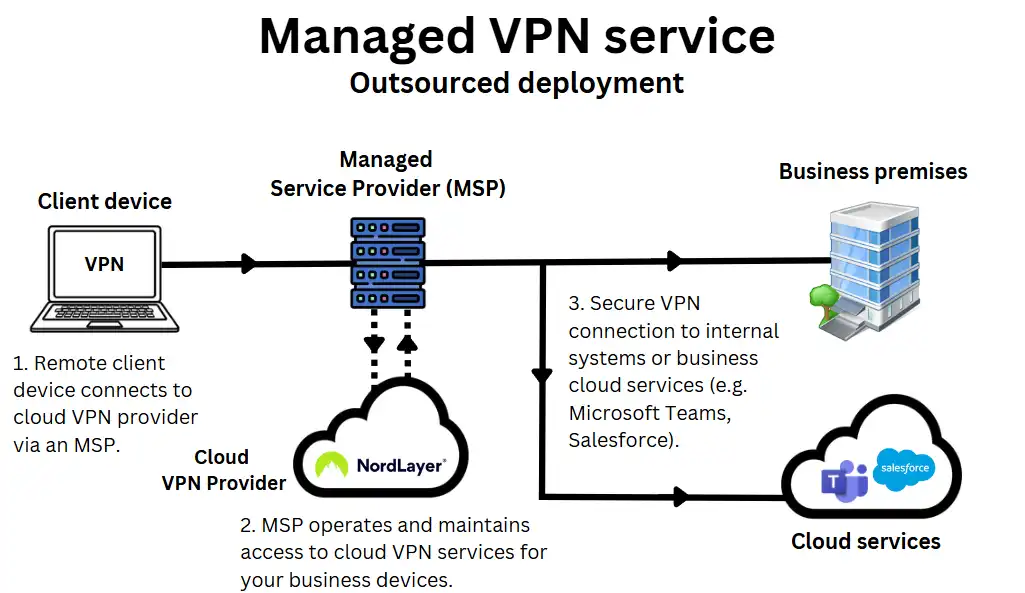
Who it’s for: SMEs without internal IT teams who need a secure VPN managed by an external provider or a business VPN platform such as NordLayer. For example, a recruitment agency or a legal firm.
Many SMEs in the UK opt for a fully managed VPN service to avoid the complexity of configuring, hosting and maintaining their own VPN infrastructure.
This is particularly common among businesses without a dedicated IT team or those already working with an external MSP (Managed Service Provider).
Managed VPN solutions are typically delivered as a subscription service. They are usually bundled into a wider managed IT support package that may include a business VoIP phone system, a leased line broadband connection and a cybersecurity SaaS.
On the MSP’s side, VPNs are implemented through third-party cloud VPN providers like Nord Layer or Perimeter 81, or their custom-built VPN, depending on the MSP’s needs.
This setup typically includes:
- A cloud-hosted or hybrid VPN managed by your provider.
- A centralised management console for access and monitoring
- VPN client apps or browser-based access for users
- Ongoing support, monitoring and updates handled externally
How it’s set up:
- Your MSP or provider handles the full deployment, including server configuration, user provisioning and security policies.
- Employees are given login details or VPN apps to connect securely, without needing to manage anything on their devices beyond the install.
- While most MSPs use third-party VPN platforms for convenience and scalability, some may also build and host custom VPNs, especially for larger client accounts with custom network requirements, on-premises infrastructure, or specific compliance needs.
- This setup offers convenience, fast rollout and minimal internal overhead, making it ideal for growing businesses or non-technical teams.
3. Cloud VPN for hybrid infrastructure
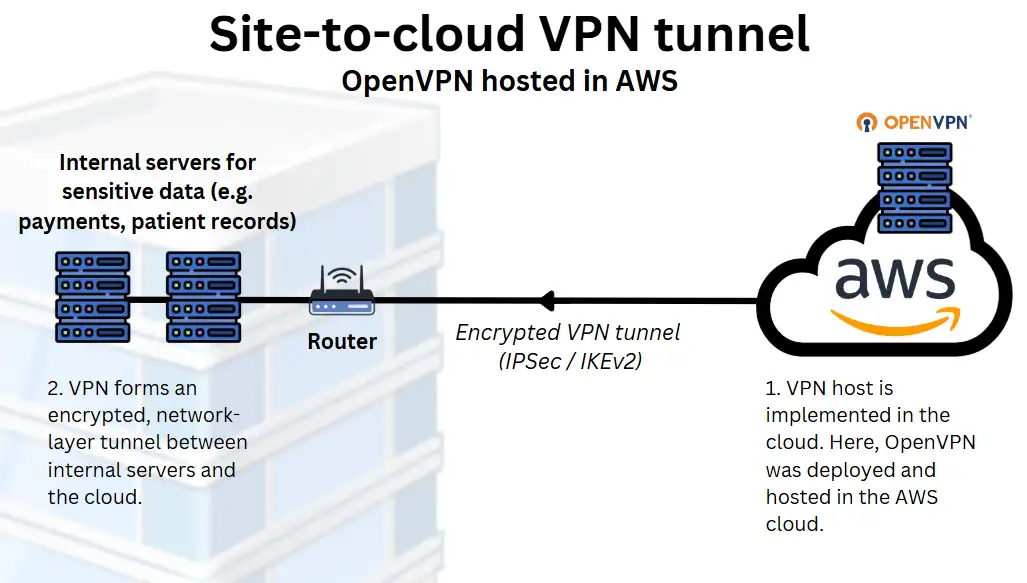
Who it’s for: Hybrid or cloud-native SaaS companies or digital agencies using AWS or Azure to link cloud-hosted apps with on-site resources.
Businesses operating across both on-premises and cloud environments often use a cloud VPN to connect these systems securely.
This setup is standard among SaaS providers, agencies, or tech-led SMEs that host applications or data in platforms like AWS, Microsoft Azure, or Google Cloud, but still run some local infrastructure for critical applications such as payments or patient data handling.
Cloud VPNs create a secure connection between a business’s physical network and a cloud-hosted network to ensure resources on each can communicate securely.
This setup typically includes:
- An active account with a cloud provider (e.g. AWS, Azure)
- A cloud VPN gateway
- A VPN-capable router or firewall on-premises
- A tunnel using a protocol like IPSec or IKEv2
How it’s set up:
Your IT team or managed service provider provisions a VPN gateway using your cloud provider’s network tools.
They then configure your on-site network hardware to establish a site-to-cloud VPN tunnel. This tunnel routes traffic securely between your office network and your cloud environment.
Cloud VPNs are ideal for hybrid infrastructure, as they maintain secure, reliable access between environments without needing everything hosted in the same place. They’re also scalable and well-supported by major cloud platforms.
4. Site-to-site VPN between physical locations
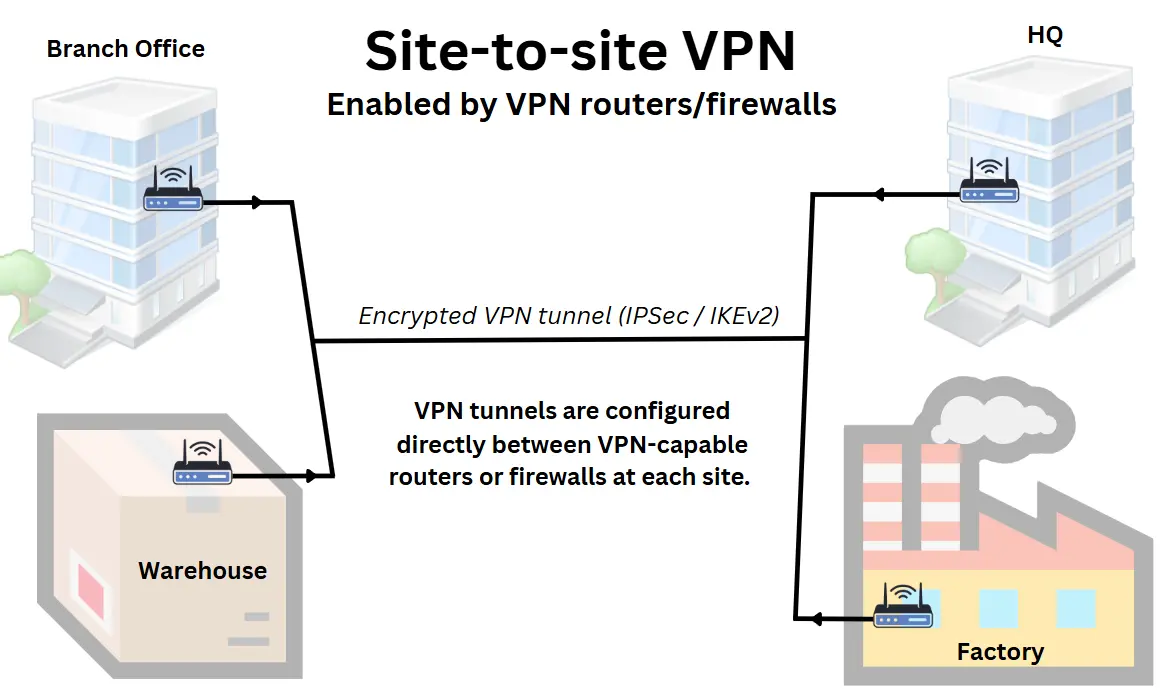
Who it’s for: Perfect for multi-site organisations, like a regional retail chain, a consultancy firm with offices across the UK, or a courier company, that require secure, always-on connectivity between branches without relying on SD-WAN for security.
Site-to-site VPNs securely connect multiple LANs, allowing teams in different offices, warehouses or branches to access shared systems and data as if they were all in the same location.
Site-to-site VPNs are typically configured between routers, firewalls, or dedicated VPN appliances at each site, forming a permanent, encrypted tunnel over the public internet or private business networks like MPLS or Business Ethernet.
This setup typically includes:
- A VPN-capable router, firewall or VPN appliance at each location
- A static IP address or for each site or a dynamic DNS solution.
- A configured VPN tunnel using IPSec or a similar network VPN protocol
- Routing rules and firewall adjustments
How it’s set up:
Your IT team or VPN service provider configures a secure VPN tunnel between each site using IPSec. Once connected, the tunnel runs in the background continuously, routing encrypted traffic between locations without requiring any action from staff.
This setup is a cost-effective and stable choice for businesses centralising systems such as VoIP platforms, file servers or internal apps, while keeping multiple sites securely connected.
💡 Site-to-site VPN solutions are slowly losing ground to SD-WAN for multi-site network security and optimisation.
Integrating business VPNs with broadband
If you’re planning to run a VPN over your existing small business broadband connection, whether for remote access, site-to-site connectivity, or secure access to cloud services, there are a few technical considerations to get it working reliably.
Here’s what to keep in mind when integrating a VPN with your broadband setup:
1. Most VPNs work over standard broadband
VPNs don’t require a specialist connection to function. The encrypted tunnel can be formed over SoGEA business broadband, full fibre business broadband, or even business satellite broadband.
This applies to both the broadband used at your main site and the connection used by the client or remote employee at home.
2. For on-site VPN hosting, hardware matters
If you’re self-hosting a VPN server or linking multiple locations via site-to-site VPN you’ll need VPN-capable routers/firewalls.
3. Leased lines offer better performance for VPNs
A leased line connection that offers guaranteed speeds, lower latency, and symmetrical upload/download will improve VPN performance and reliability, especially for multiple users or persistent site links.
In rural areas without access to fibre, wireless leased lines and EFM offer alternative, Ethernet-grade solutions. Alternatively, compare business broadband deals to find the best connection for your premises at the best price.
4. VPNs will affect your connection speed
VPNs introduce bandwidth overhead by encrypting and encapsulating data before transmission. This will reduce your available speed, particularly during high-bandwidth activities like file transfers or UCaaS video conferencing.
A faster, uncontended broadband connection can help mitigate this on the business side, though performance will still depend on the client’s broadband if they connect remotely.

