Multi-Factor-Authentication (MFA) for businesses: What it is and why it matters
Multi-Factor Authentication (MFA) adds additional verification steps before granting access to business systems. It is one of the simplest and most effective ways for organisations of any size to prevent unauthorised access, security breaches, and data theft.
This guide explains how MFA works, outlines the different types available, and provides practical recommendations for implementing it effectively across the organisation.
Contents:
- What is Multi-Factor Authentication (MFA)?
- How does Multi-Factor Authentication work?
- Types of Multi-Factor Authentication
- Best practices for implementing Multi-Factor Authentication in a business
What is Multi-Factor Authentication (MFA)?
Multi-Factor Authentication (MFA) is a security feature that requires users to provide two or more forms of verification to access an account, application, or system.
Instead of depending on just a password (known as single-factor authentication), MFA adds extra layers of protection by asking users to verify their identity through methods such as:
- A one-time code sent via SMS or email
- A fingerprint scan or facial recognition
- A hardware security key or authenticator app
MFA has become a cornerstone of digital security across both consumer and business applications. For example, anyone using a smartphone authenticates it in the form of biometrics (fingerprint or face ID), a PIN or a touch pattern, and push notifications for their Google/Microsoft accounts.
It is widely regarded as one of the simplest and most effective defences against common cybersecurity threats, including stolen credentials, phishing, and unauthorised access. It’s a core requirement of leading cybersecurity frameworks, such as Cyber Essentials, and is mandated by regulatory standards.
However, MFA’s effectiveness depends on careful implementation, one that strengthens security without compromising user experience, ensuring both protection and usability across the organisation.
How does Multi-Factor Authentication work?
Verifying a user’s identity through a series of MFA checks happens quickly (in seconds or minutes), but behind the scenes, it involves coordinated communication between the user’s device, authentication servers, and the organisation’s identity management platform.
The following sequence outlines how MFA typically works in a business environment:
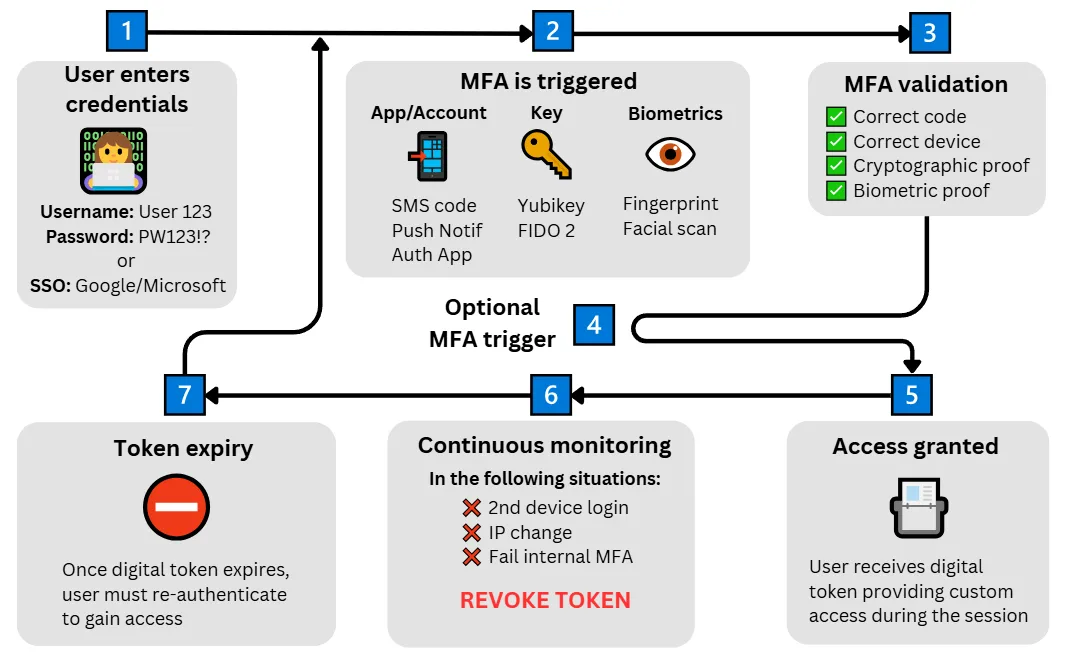
Step 1: User attempts to log in
The MFA process begins when a user, such as an employee or administrator, tries to access a company system, whether that’s email, a cloud application, or a remote network.
They enter their username and password, or authenticate through Single Sign-On (SSO).
The credentials are checked against a secure directory or identity provider. If correct, the authentication process moves to the next stage. If not, access is denied immediately.
Step 2: User verifies a triggered MFA challenge
Once the first factor (usually a password) is verified, the system requests an additional form of verification from the user.
This second factor can take several forms, such as:
- A time-limited code from an authenticator app (Microsoft Authenticator, Google Authenticator, Authy)
- A push notification sent to a registered mobile device
- A physical security key (such as a YubiKey)
- A biometric check, such as a fingerprint or facial scan
The user responds to the MFA prompt accordingly. Each method generates a verification response, which is securely transmitted to the authentication server.
This ensures that the person attempting access not only knows the password but also possesses something unique or personal that proves their identity.
Step 3: The system validates the second factor
The system then validates the second factor using secure, industry-standard methods:
- Authenticator apps: The system checks that the code matches the expected time-based one-time password (TOTP) generated from a shared secret key.
- Push notifications: The correct registered device must respond with an encrypted approval.
- Hardware keys: Validation occurs via cryptographic challenge–response protocols such as FIDO2 or WebAuthn, which confirm the physical presence of the user.
- Biometrics: The match is confirmed locally on the user’s device or within a secure hardware enclave (never stored as raw images).
If validation succeeds, the system confirms that both factors are genuine and that the request originates from the authorised user.
Step 4: Additional factors are triggered (optional)
While most MFA implementations use two factors (also called “2FA” or “Two-Factor Authentication”), highly sensitive operations such as system administration, privileged database access, or high-value financial transactions may require three or more.
This is sometimes referred to as step-up authentication or multi-step verification.
For example:
- A network engineer might be required to use a password, an authenticator app code, and a hardware token.
- A financial controller approving a large transfer may also need to confirm through a secure mobile device registered in their name.
This level of protection helps mitigate risks such as coercion or “wrench attacks”, where a user could be forced to share one authentication factor but not all. It is also essential for achieving compliance with some industry-specific cybersecurity frameworks.
Adaptive or contextual checks
Modern MFA systems often include adaptive authentication, where risk-based intelligence decides whether to enforce additional checks.
For example:
- A login from a known office location on a trusted device doesn’t trigger a full MFA prompt.
- A login attempt from a new country, at an unusual time, or on an unrecognised device requires an extra factor or is blocked.
This adaptive layer balances user convenience with strong security, minimising unnecessary interruptions while maintaining vigilance against suspicious activity.
Step 5: Access granted and session created
Once all factors are successfully validated, access is granted.
The organisation’s identity platform (such as Azure Active Directory, Okta, or Duo) issues a secure session token, which acts as proof that authentication has been completed.
This secure session token is a temporary, encrypted object held in the user’s login session that includes metadata such as user ID, device ID, access scope and expiry time. It’s like receiving a “visitor ID badge” that grants access to a limited part of a facility for a limited time.
It is customised for each session, granting users access as per the company’s security policy. It expires after a set period or if risk conditions change, forcing the user to reauthenticate.
This gives flexibility for different security postures. For instance, short session tokens for financial systems, and longer ones for standard productivity apps.
Step 6: Continuous session protection
MFA continues to play a role even after sign-in. It’s typically integrated with broader cybersecurity tools such as endpoint monitoring, Zero Trust frameworks, and user behaviour analytics.
These systems continuously evaluate activity for signs of compromise, for example, unusual data access, simultaneous logins from different regions, or attempts to disable MFA.
If anomalies are detected, the system can:
- Revoke the session token
- Require re-authentication
- Escalate to “step-up” MFA for critical actions
This makes MFA part of a continuous defence model rather than a single checkpoint at login.
Step 7: Token expiry and re-authentication
Every authentication token issued during login has a defined lifespan. When that token expires, the user must go through the authentication process again to renew access.
This expiry mechanism helps prevent long-term or unattended sessions from being exploited by attackers. If a session remains idle beyond the allowed period, or if risk signals change (such as the user’s IP address, device fingerprint, or location), the system automatically invalidates the token and prompts re-authentication.
Adaptive policies can shorten or extend session length based on the level of trust in the device or context.
Types of Multi-Factor Authentication
There are several types of multi-factor authentication (MFA) methods, each offering a unique balance of security, convenience, and complexity.
Each method falls into one or more of the following “MFA type categories”. Strong authentication typically combines factors from at least two of these:
- Something the user knows (knowledge): Passwords, PINs (typically the first factor)
- Something the user has (possession): Hardware device, app, e-mail account
- Something the user is (inherence): Biometrics
The list below is organised from the most common and basic to the most advanced and phishing-resistant options, noting their primary category for context.
SMS/email one-time codes
Category: Possession
Single-use codes are sent to the user’s mobile phone or email address to be entered during login. These codes are typically time or session-sensitive, ensuring they cannot be reused later if someone gains access to the user’s messages or inbox.
This method remains popular because it relies on devices and accounts that users already have. Still, it is considered the least secure due to the potential for SIM-swaps and message interception.
Pros
- Simple to understand and quick to deploy
- No need for additional software or hardware
Cons
- Vulnerable to SIM-swap (attacker gains access to SMS) and phishing attacks
- Dependent on network connectivity (fails without cellular service)
- Least secure of all MFA types
Authenticator apps
Category: Possession
Applications such as Microsoft Authenticator, Google Authenticator, or Authy generate short-lived, time-based one-time passcodes tied to a user’s device.
Each code refreshes every 30–60 seconds, providing a secure, offline verification method. Because these apps work independently of mobile carriers, they’re much more secure than SMS or email-based MFA.
Pros
- Works offline once configured
- More secure than SMS (no carrier dependency or SIM-swap risk)
- Free and easy to distribute
Cons
- Requires initial setup and user training
- Device loss can lock users out if not backed up
Push notifications
Category: Possession
A verification prompt is sent to the user’s registered device, allowing them to approve or deny a sign-in attempt with a single tap. These prompts often include contextual details such as location or device name, helping users detect suspicious activity.
Push-based MFA is extremely user-friendly, though its convenience can lead to “MFA fatigue”, which is when users are overwhelmed by notifications and approve prompts without verifying them.
Pros
- Quick, frictionless user experience
- Includes contextual login data for transparency
Cons
- Vulnerable to “MFA fatigue” attacks
- Requires an active internet connection
Biometrics
Category: Inherence
Biometric authentication uses unique physical traits (fingerprint, facial scan, or voice pattern) to verify identity. These identifiers are usually processed and stored locally on the user’s device, reducing the risk of external data theft.
Biometric methods are fast and secure, but are rarely used as standalone authentication in enterprise settings. They’re most effective when paired with another factor.
Pros
- Fast and convenient; no codes to enter
- Highly secure; difficult to replicate or share
Cons
- Privacy and storage concerns around biometric data
- Usually paired with another factor for compliance
- Still vulnerable to phishing if users unlock devices without caution
Hardware tokens

Category: Possession
Separate physical devices (YubiKeys, RSA SecurID tokens) that generate or store secure cryptographic codes. These codes authenticate the user when entered manually or when the token is connected to a device.
They operate independently of mobile or internet networks, offering strong protection against remote attacks. However, they require careful management, distribution, and replacement.
Pros
- Very high security; phishing and SIM-swap-resistant
- Works offline
Cons
- More costly to issue and replace
- Requires users to carry an additional device
- Can be lost or damaged
FIDO2/WebAuthn (Passwordless MFA)
Category: Possession
FIDO2 and WebAuthn are modern authentication standards that use cryptographic keys bound to a device or hardware token.
They are designed to replace traditional credentials (usernames and passwords) with more user-friendly methods, such as a PIN, biometric scan, or pattern unlock. These are often referred to as Passwordless MFA, as their goal is to eliminate passwords entirely.
Instead of typing credentials, users confirm their presence using a device unlock method, such as:
- Tap “Log In.”
- Instead of typing a username and password, you’re prompted to use Face ID or Touch ID.
- Your phone scans your face or fingerprint.
- Behind the scenes, the device uses the biometrics to release a cryptographic key stored locally.
- The released key goes to the app’s server and signs a unique challenge on there, proving your identity to the app without revealing any passwords.
This form of authentication is now commonplace in banking apps and smartphone ecosystems. It’s phishing-resistant, fast, and eliminates the risks associated with password reuse or theft.
Note: While this method may feel similar to standard biometric login, FIDO2 and WebAuthn go a step further by using cryptography to mathematically prove your identity to the app’s server, not just to your device.
Pros
- With phishing protection, users can’t be tricked by fake login pages or phishing e-mails.
- Replay-resistant, meaning attackers can’t use the same code in the same session to authenticate.
- No passwords to steal, forget, or reset
Cons
- Requires compatible hardware and software support
- Implementation can be complex at scale
Smart cards / PKI tokens

Category: Possession
Smart cards and PKI (Public Key Infrastructure) tokens are physical authentication devices (ID cards, USB keys) that contain embedded digital certificates.
These certificates securely verify a user’s identity when the card is inserted or tapped against a reader, often alongside a PIN or biometric for additional verification.
Because they’re based on strong cryptographic principles, smart cards are widely used in government, defense, banking, and other highly regulated industries.
They not only confirm a user’s identity but can also digitally sign actions (for example, approving a banking transaction or signing a legal document), providing both authentication and non-repudiation.
Note: These devices go beyond hardware tokens like YubiKeys by adding digital signature capabilities. They cryptographically verify actions and integrate with physical access systems for stronger identity assurance.
Pros
- Mature, trusted technology with strong identity assurance
- Supports digital signing and encryption at the same time
Cons
- Expensive to deploy and manage
- Requires specialist readers or supporting infrastructure
Best practices for implementing Multi-Factor Authentication in a business
The effectiveness of MFA depends entirely on how it is implemented. Simply enabling it across all applications is not enough; it must be introduced in a way that aligns with the organisation’s size, risk profile, and working practices.
A well-designed implementation strengthens security without undermining usability or efficiency. If it’s too complex, employees may resist or find workarounds; if it’s too lenient, it won’t deliver adequate protection.
The following best practices outline how to deploy MFA effectively and sustainably across a business.
Start with a risk-based rollout
Begin by protecting the most sensitive apps, and work downwards. Prioritise high-risk accounts such as administrators, executives, and finance users before extending MFA to the wider workforce. This phased approach delivers early risk reduction while allowing time to refine policies and processes before wider deployment.
Choose phishing-resistant MFA
Avoid SMS codes and email links wherever possible. While they’re better than passwords alone, these methods can be intercepted or spoofed and offer limited protection against modern threats like SIM-swap attacks.
Instead, adopt a combination of phishing-resistant options such as biometrics, authenticator apps, hardware tokens, or FIDO2/WebAuthn.
Balance security with user convenience
User experience is key to successful adoption. If MFA feels intrusive or time-consuming, people may resist using it or seek ways to bypass it. Select authentication methods that align with how staff work.
Consider implementing adaptive MFA, which requests additional verification only when risk indicators appear (such as logins from unfamiliar devices or locations).
Integrate MFA with identity and access management systems
MFA is most effective when part of a broader identity and access management (IAM) cybersecurity solution.
Integrate it with single sign-on (SSO), identity federation, and privileged access management (PAM) solutions to enforce consistent access policies across all platforms. This unified approach simplifies administration while improving both user experience and compliance.
Train users and communicate clearly
People are central to MFA success. Before rollout, explain why MFA is necessary and how it protects both the organisation and individuals.
Provide clear setup instructions, short training sessions, and accessible support for users who encounter difficulties. Effective communication fosters understanding, trust, and smoother adoption across the organisation.
Set up secure recovery and fallback options
Occasionally, users will lose devices or lock themselves out. Ensure that recovery processes are both secure and straightforward, using:
- Backup authentication codes stored securely
- Secondary trusted devices
- Verified IT-assisted recovery procedures
Avoid weaker fallback methods like email-based resets, which can undermine MFA’s effectiveness.
Apply MFA consistently across all access points
MFA should be enforced wherever business data or systems are accessed, not just for core platforms.
Make it company policy to apply it to cloud services, VPNs, business VoIP phone systems, administrative portals, and third-party apps. Regularly review access configurations to close any remaining gaps; consistency is essential for true protection.
Monitor and review authentication activity
MFA generates valuable data on authentication behaviour. Monitor failed sign-in attempts, repeated prompts, and access from unexpected locations. Integrating these logs with security monitoring or SIEM tools enables early detection of anomalies, better visibility for auditors, and stronger compliance evidence.
Keep MFA policies and technology up to date
Cybersecurity threats evolve, and so should MFA policies. Audit the deployment regularly to ensure coverage remains complete. Retire outdated methods such as SMS-based codes and ensure authenticator apps, devices, and configurations are kept up to date.
Measure adoption and impact
Monitor MFA adoption rates, user feedback, and incident statistics to assess effectiveness. Track metrics such as reductions in account compromises or password resets to demonstrate measurable improvement. These insights help refine policies, support ongoing investment, and maintain executive confidence in the security programme.
Why Multi-Factor Authentication is important for businesses
Multi-Factor Authentication is one of the simplest and most effective ways to prevent unauthorised access to valuable data and systems.
Here are ten key reasons why MFA matters:
1. Protects against password breaches
Passwords are often reused, guessed, or stolen in large-scale data breaches and traded on the dark web. Even basic MFA methods like SMS codes ensure that a stolen password alone isn’t enough for access.
Adding dark web monitoring helps detect and respond quickly if credentials are leaked.
2. Reduces phishing and social engineering risks
Phishing is still the leading cause of credential theft. With MFA, stolen usernames and passwords are useless without a second factor, forcing attackers into more complex and less successful tactics. Combined with cybersecurity awareness training, MFA makes your business extremely robust to phishing.
3. Ensures regulatory and compliance alignment
Many industries (finance, healthcare, government) require MFA under regulations such as GDPR, HIPAA, PCI-DSS, and NIST guidelines. Using MFA in the right places demonstrates compliance and reduces legal and financial risks.
Implementing MFA demonstrates cybersecurity compliance, reduces liability, and can mitigate penalties after a security incident.
4. Limiting insider threats
MFA on internal systems makes it harder for compromised credentials to be misused. For example, if attackers gain privileged admin access to the business SD-WAN system, the system may still require additional MFA for sensitive actions like adding devices or endpoints, preventing significant damage.
5. Securing remote and hybrid work
With distributed teams, MFA is essential for securing VPNs, cloud platforms, and collaboration tools like Microsoft Teams and CRMs. Modern MFA integrates with identity and endpoint management systems to maintain consistent protection wherever employees connect.
6. Prevents account compromise
MFA drastically reduces the risk of credential stuffing, brute force, and session hijacking. It adds visibility into login activity (i.e. who signs in, when, and from where, helping detect anomalies early.
7. Enables zero trust and digital transformation
MFA is a foundational component of Zero Trust Network Access (ZTNA), which assumes no user or device is trusted by default.
Combined with Single Sign-On (SSO) and device compliance checks, it supports centralised, risk-based access control across cloud and on-prem environments.
8. Improves user experience and productivity
Modern MFA (biometrics, push approvals, adaptive prompts) balances security with convenience. It reduces password fatigue, minimises lockouts, and cuts IT support tickets, improving both security and efficiency.
9. Strengthens customer and partner trust
Visible security measures like MFA show customers, partners, and regulators that data protection is a priority. It strengthens reputation and fosters confidence in your organisation’s security practices.
10. Boosts IT efficiency and reduces overheads
MFA integrates with SSO, Privileged Access Management (PAM), and identity monitoring tools to centralise authentication. This streamlines administration, reduces manual recovery tasks, and improves incident response, lowering overall operational costs.
Multi-Factor Authentication – FAQs
Our cybersecurity experts answer frequently asked questions on Multi-Factor Authentication for businesses:
What’s the difference between 2FA and MFA?
Two-Factor Authentication (2FA) uses exactly two factors, while Multi-Factor Authentication (MFA) can use two or more.
Is SMS MFA still secure?
SMS MFA adds protection beyond passwords but is vulnerable to SIM-swap and phishing attacks. In some industries, it is already considered a legacy MFA. Stronger options like authenticator apps or hardware keys are recommended.
Does MFA slow down employees?
When paired with SSO and adaptive access, MFA adds minimal friction. An immense reduction in account breaches and downtime outweighs the small delay.
Do small businesses really need MFA?
Yes, attackers often target small businesses because they assume their security is weaker, and these businesses are frequently an entry point to larger corporations, as was the case in the 2025 Tesco cyberattacks. MFA is one of the most cost-effective defences available.
Can MFA stop phishing attacks completely?
MFA significantly reduces phishing success but doesn’t eliminate it entirely. Attackers can still trick users into approving fraudulent logins (so-called “MFA fatigue” or “push bombing” attacks).
Phishing-resistant methods like FIDO2 or WebAuthn provide the strongest protection by requiring hardware or cryptographic verification rather than user interaction alone.
How do I know what type of MFA to roll out?
The best type of MFA depends on your organisation’s risk profile, user base, and technology environment. Different scenarios call for different approaches:
- Low to moderate risk / small teams: App-based authenticators are typically sufficient. They’re easy to deploy, cost-effective, and provide a strong layer of protection beyond passwords.
- High-risk or regulated industries: App-based authenticators for low risk accounts and departments. Phishing-resistant MFA methods, such as FIDO2/WebAuthn hardware keys, for sensitive networks. These provide cryptographic verification and meet strict compliance standards.
- Remote or hybrid workforces: Combine app-based codes with adaptive MFA that factors in device type, network, and user behaviour. This balances strong security with flexibility for users on the move.
- Legacy systems: When hardware keys or modern protocols aren’t supported, use app-based codes or one-time passwords (OTPs) as a temporary safeguard until upgrades are possible.

